Skyhigh Security
スカイハイセキュリティ
- 企業のクラウド化で懸念される脆弱なセキュリティ- クラウドサービス別セキュリティ対策のポイント

企業のクラウドシフトで見えてきた、脆弱なセキュリティ対策 ~クラウド別セキュリティ課題とその対策を考える~
企業の成長に、変革は欠かせません。最先端テクノロジーを活用しながら、働き方や業務スタイル、組織や文化を変革することが、企業の競争力を強化します。実空間とサイバー空間が高度に融合するデジタルトランスフォーメーションが進む中、企業はこぞって自社の業務システムやサービス、社内システムのクラウド化を図っていますが、利用の増加に従いクラウド特有の課題が表出しています。
ここでは、クラウドの種類とそれぞれが抱える特有の課題、企業がさらされているセキュリティリスクについて整理し、オンプレミス時代とはアプローチが異なる「クラウドセキュリティ」について解説します。
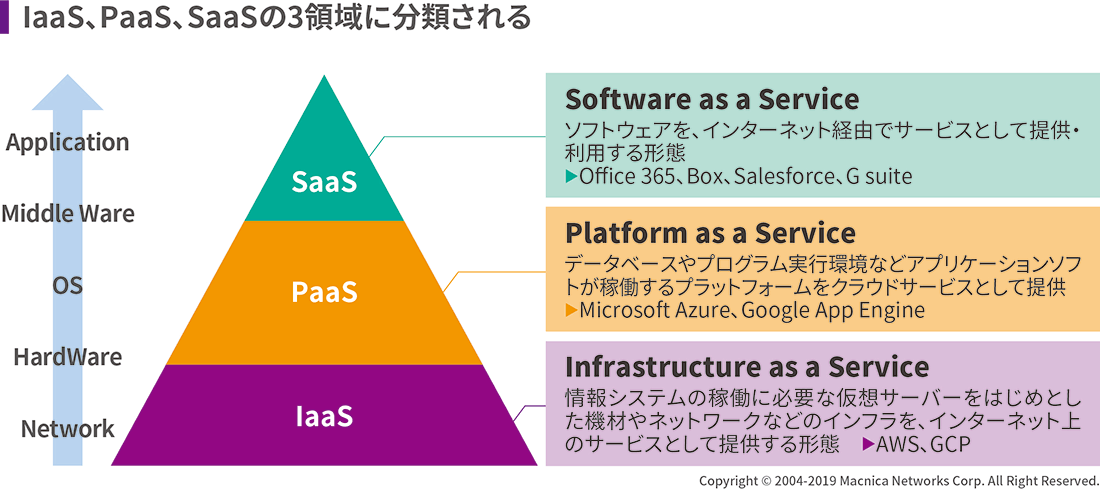
クラウドの3領域(IaaS、PaaS、SaaS)
クラウドサービスは、大きく以下の3つに分類されます。
- IaaS(Infrastructure as a Service):AWS、GCPに代表される、インフラを提供
- PaaS(Platform as a Service):Azure、Google App Engineに代表される、アプリケーションソフトが稼動するプラットフォームを提供
- SaaS(Software as a Service):Office 365、Box、Salesforce、G Suiteに代表される、ソフトウェアを提供
IaaS、PaaS、SaaSはそれぞれ役割や特性が異なり、各サービス特有のセキュリティ課題があります。これに対処するにはまず、自社内で利用されているクラウドサービスが、どの領域のどのようなサービスなのかを正確に把握する必要があります。また、システムにもAWSなどのIaaS上に構築された顧客向けビジネスシステム、従来のパッケージからインターネット上のSaaSサービスに移行した社内のOA系業務システムなど、クラウドと関係のある様々なシステムがありますので、あわせて現状を把握することが大切です。
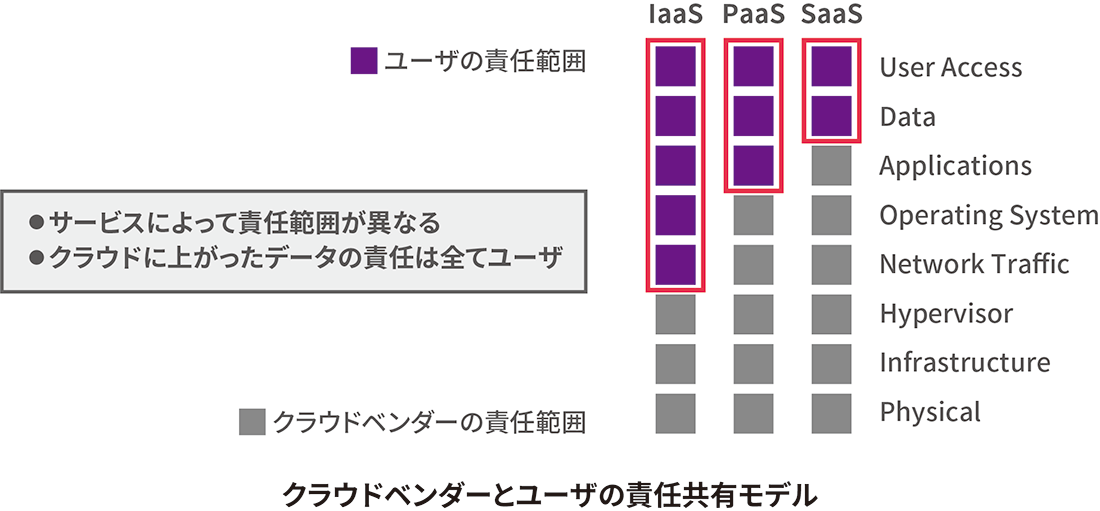
クラウドベンダーが担うセキュリティの範囲
3つに分類されるクラウドサービスは、下の図の通り、それぞれベンダー側の責任範囲が異なります。しかし、いずれの領域においてもクラウド上に上がった「データ(情報)」は、すべてユーザ側に責任範囲があることをご存じでしょうか。「クラウドベンダー側が責任をもってセキュリティ対策をし、安全を担保してくれている」というのは思い込みです。この点を、まず認識する必要があるでしょう。
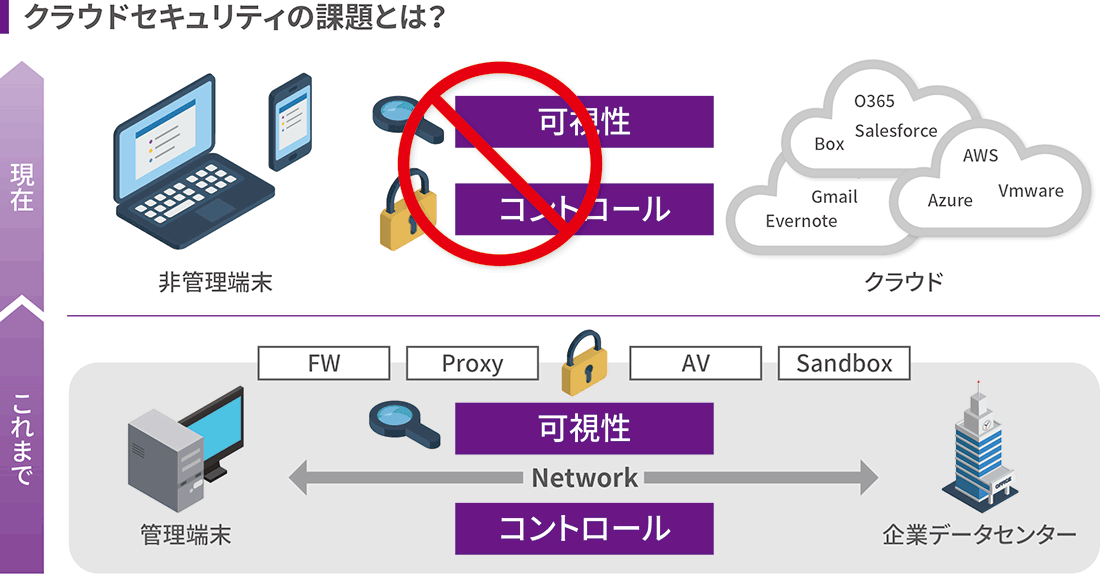
クラウド化が進んだ結果、オンプレミス環境で講じていた従来型のセキュリティ手法とは、異なるアプローチが必要となりました。「閉じられた環境」の中で、可視性が高く、自社で運用がコントロールできていた従来のシステムとは異なり、「外部へ開かれた」クラウドでは、可視化もコントロールも難しく、万が一情報漏洩などのインシデントが生じた場合の影響は格段に大きくなります。オンプレミスとは異なるクラウド特有のセキュリティを、IaaS、PaaS、SaaSそれぞれの特性を踏まえて、内部監査と外部攻撃の両方の観点で対処する必要があります。
クラウドセキュリティの課題とは?
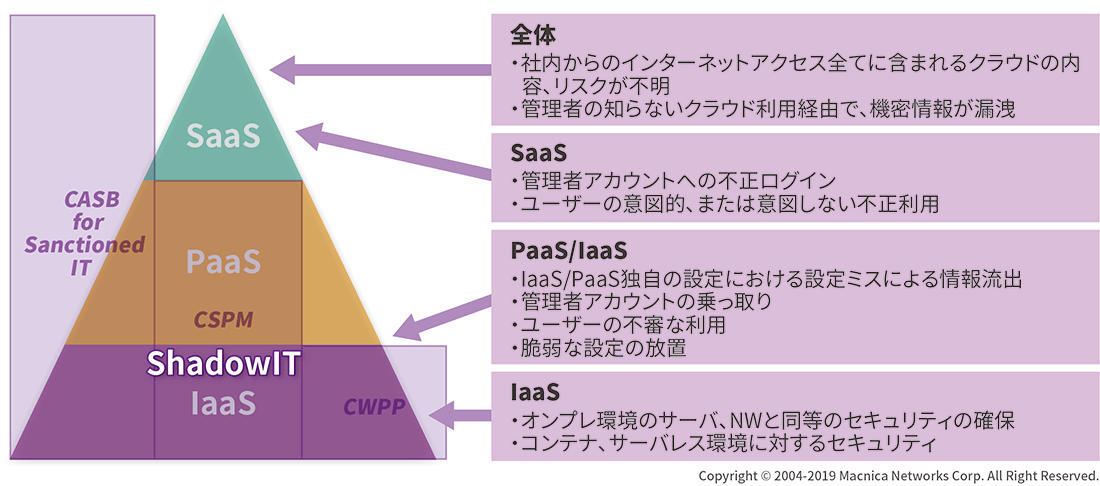
IaaS、PaaS、SaaSそれぞれに求められるセキュリティ要素
では、それぞれのクラウドサービスに適したセキュリティとは、どのようなものでしょうか?
- IaaSの課題と対策
2019年7月、米国大手金融会社が、WAF(Web Application Firewall)の設定ミスにより、SSRF(Server Side Request Forgery)攻撃を受け、AWS上にある約1億人分の個人情報に違法にアクセスされる情報漏洩事件が発生しました。
IaaSでも、サーバ、ネットワークに対してオンプレミス時代と同様のセキュリティが必須です。IaaS基盤上でオンプレと同等のセキュリティを提供し、コンテナ、サーバレス環境などへの対応もカバーする、IaaSに適合したセキュリティソリューション、CWPP(Cloud Workload Performance Platform)が有効です。
- PaaS/IaaSの課題と対策
AWS S3のユーザ設定ミスによる情報漏洩インシデントが多発しています。AWSのサービスリリースの速度にユーザが追随できないことから、脆弱な設定を通じて個人情報データが外部に公開されるケースが少なくありません。AWS独自の機能に対するユーザ設定ミスが要因ですが、攻撃者はこうした脆弱性を突いてきます。管理者アカウントの乗っ取りなどと同様の外部攻撃リスクと言えるでしょう。脆弱な設定に気が付かない、ユーザが不審な行動をする、といった内部リスクへの対処も必要です。
こうしたPaaS/IaaS特有のリスクには、管理者アカウントへの攻撃や脆弱な設定、不審な動きを検知するCSPM(Cloud Security Posture Management)が有効です。
- SaaSの課題と対策
Office365、box、G Suiteなど、社内業務に使う機会が多いSaaSのサービス。知らないうちに不正ログインされているなどの外部攻撃リスクと、社員の(意図的とは限らない)不正利用などの内部リスク、両面に対するセキュリティ対策が必要です。例えば、社員が自宅で作業をするために、自社契約SaaSに機密文書をアップロードし、共有リンクを利用して個人メールアカウントに機密情報を共有したことから、重要なインシデントに発展したケースもあります。
SaaS利用の大きな課題は、自社で契約し利用しているサービス(サンクションIT)であっても、誰が何をどのように使っているのか、システム管理者が監視できないことです。オンプレミスでは可能だった利用状況の可視化やログの追跡、運用コントロールが、クラウドでは難しいからです。こうしたSaaS特有の課題には、クラウドの利用状況を可視化し、アクセスを制御するなどのコントロール機能を有するCASB(Cloud Access Security Broker)が有効です。
- クラウド環境全体に通じる課題と対策
クラウドサービスのあらゆる領域に関わる課題が、「シャドウIT」の存在です。安全性が担保されないファイル保管・データ共有、電子メールなどのクラウドサービスが、「便利だから」と勝手に使われています。社員がインターネット経由でどれだけ使っているか、管理者は把握できません。会社が許可しない無料のストレージサービスを自己判断で使用し、機密情報が漏洩したケースもあります。
McAfeeの調査では、企業内のインターネットアクセスログを解析すると、平均で1,935のクラウドサービスが検出されています。社内の全クラウドの利用を可視化し、利用状況や危険なサービスが含まれていないかチェックすべきでしょう。こうしたシャドウITへの対策にも、CASBが有効です。
まとめ
ここまで述べてきた各クラウドサービスにおけるセキュリティリスクは、インシデントが起きて初めて気付くことが多いものです。しかし、多くの企業が、稼働が止まると困るビジネスシステムをクラウド環境上で展開している今、インシデントが起きてからの対応では遅すぎます。McAfeeの調べでは、クラウド上の機密情報の9割が、契約しているSaaS/IaaSにあることが分かっています。契約しているクラウド上に、どのようなデータがどのように共有されているかを把握しセキュリティ対策をすることは、急務の経営課題といえるでしょう。
McAfeeは、こうしたクラウド上のセキュリティリスクに対応するCASB製品として、「MVISION Cloud」を提案しています。自社が契約するクラウドに適したセキュリティ対策ができているかどうかを含めて、まずはご相談ください。
※取材当時の情報となります。
お問い合わせ・資料請求
株式会社マクニカ Skyhigh Security 担当
- TEL:045-476-2010
- E-mail:mfe-info@macnica.co.jp
平日 9:00~17:00