product
- Macnica SOC Service
- CrowdStrike Monitoring Operation Support Service
- Active Directory Diagnostic/Monitoring Service
- Trellix EDR Monitoring Service
- Threat Hunting & Incident Response Service
- Triage service
- security assessment
- security advisory
- CSIRT construction support
- CSIRT enhancement exercise
- Suspicious email training service
- platform diagnostics
- Website security monitoring service
- Web application vulnerability diagnosis
- Supports initial response to incidents. Responds smoothly from stopping the bleeding to neutralizing the attack and preventing damage from spreading.

Macnica Security Service
Macnica Security Services
Tick Group targeting Japanese manufacturing industry
Tick Group targeting Japanese manufacturing industry

The attacker group Tick, which is believed to be based in the Chinese-speaking world, has a long history of activity and is said to have been active since around 2008. We have also observed that Tick is continuing its activities in Japan. In January 2020, an incident was reported in Japan in which the Tick group may have been involved. In light of this situation in which attacks by the same group are active, we are writing this article in the hope that we will be able to assist in incident investigation and response by organizing and publishing the information we possess.
What are ticks?
The Tick group's activities have been observed mainly in Japan and South Korea, and so far it has targeted many industries such as marine engineering, telecommunications, electric power, and manufacturing. Based on the activity so far, the purpose is believed to be intellectual property theft. The first public mention of Tick was in 2016, the same year an analysis report was published on one of Tick's tools, the malware Daserf. In 2017, vulnerabilities in domestic asset management software were exploited, and many organizations were infected with malware called “XXMM”.
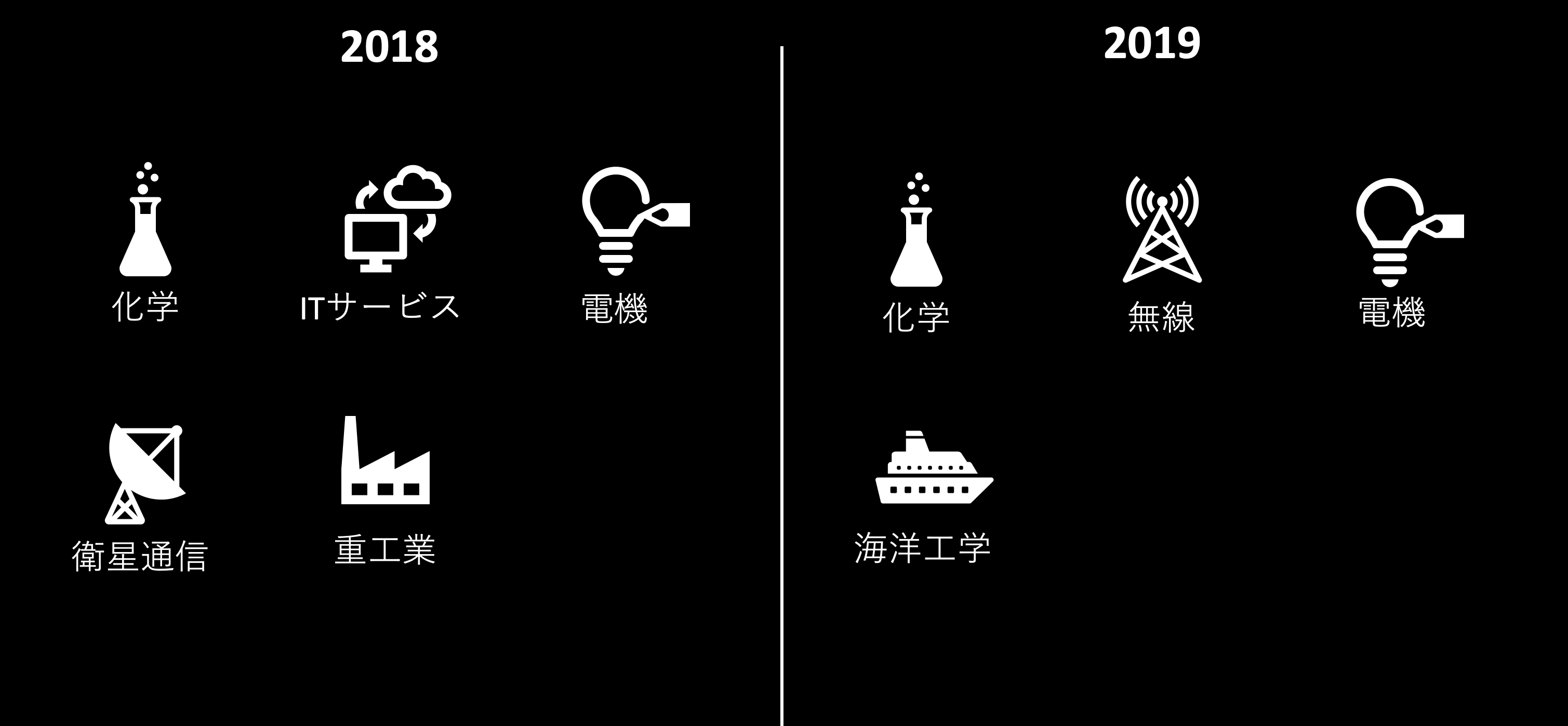
In 2018 and 2019, we will continue to target multiple technology verticals. They were particularly active in the chemical industry (Fig. 1).
Figure 1. Sectors with observed attacks in 2018 and 2019
Changes in TTP observed since 2018
One of the changes in TTP that can be seen from 2018 is that the delivery destination of attack emails has changed from domestic to overseas bases. Attacks began to use files that are likely to be interesting and likely to be executed in the culture of the destination country (Figure 2). It is believed that attackers shift their targets to overseas bases because they have determined that the possibility of internal intrusion is higher at overseas bases than in Japan, where security has been strengthened.
Figure 2. Delivered file
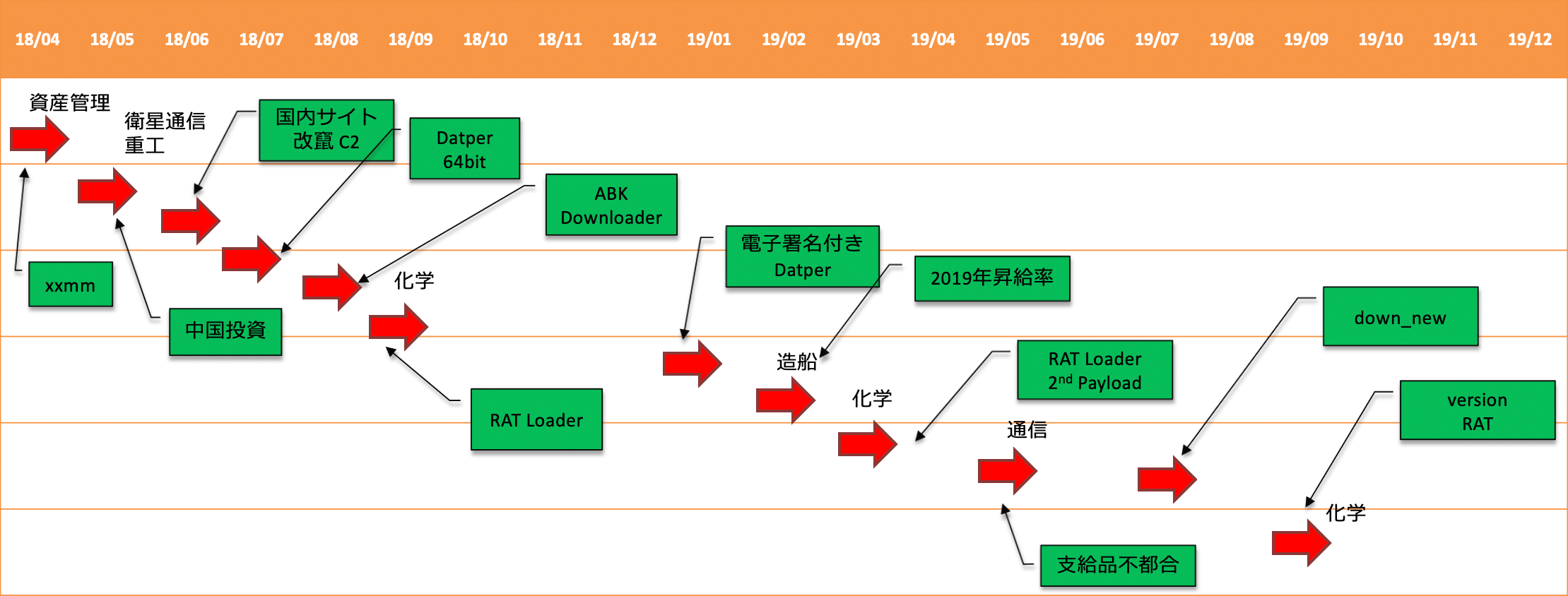
The timeline of Tick's activities observed by our company is as follows (Fig. 3).
Figure 3. Tick activity timeline
Another change is that the observation of conventional backdoors (Daserf, XXMM, Datepr) has decreased, and new tools (RAT Loader, ABK Downloader, etc.) have begun to be used very often. These tools are constantly being improved to avoid detection.
attack flow
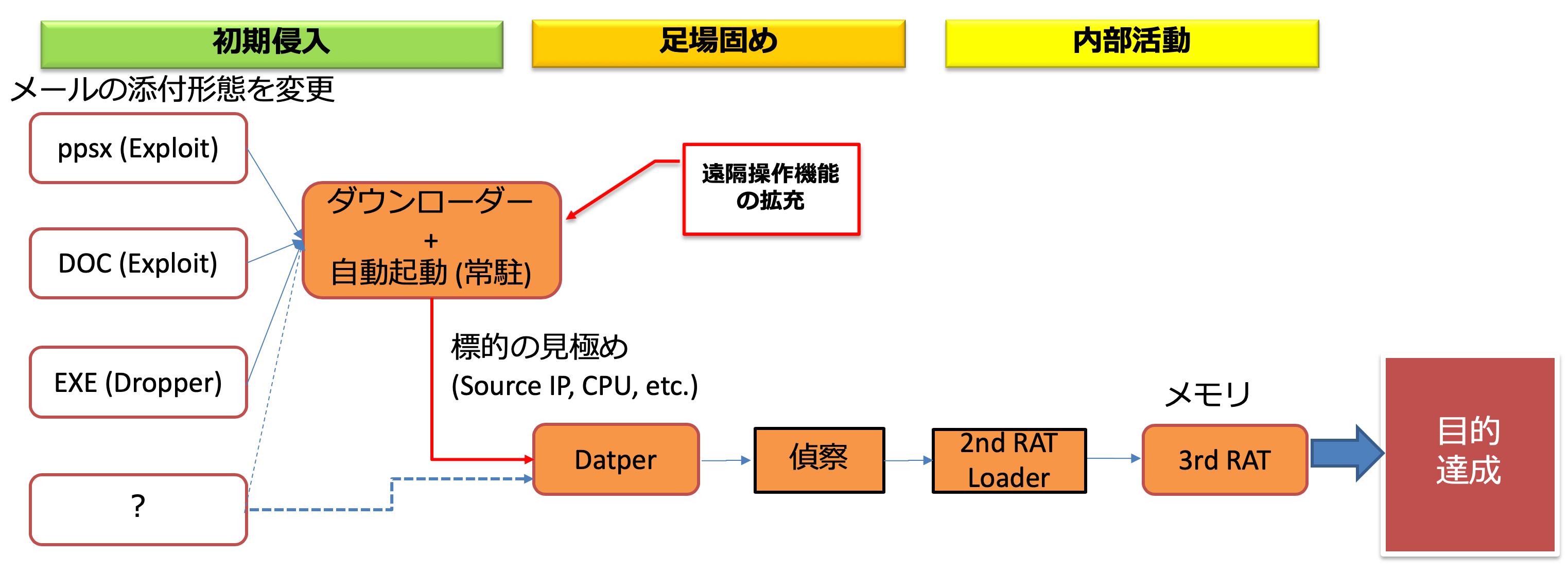
Attacks mainly originated from spear phishing emails, which used social engineering to camouflage known vulnerabilities such as CVE-2017-8759, CVE-2018-0798, and CVE-2018-0802 and icons to make the recipients execute them. doing.
The downloader that downloads the next malware initially sent information about the CPU of the infected terminal and the anti-virus product that was running to an external server to filter the target of sending new malware. A conventional backdoor-type Datper was sent in, and after reconnaissance of the internal network, secondary and tertiary RATs were infected to other terminals to expand the range.
Downloaders in 2019 have added a simple remote control function. We believe that the purpose of this is to evade detection by security products and hinder the acquisition of specimens by security vendors by obtaining more information from the infected terminal and delivering the next malware only to the real target. increase.
Figure 4. Attack flow
Continuously Improved Downloader
In November 2019, we observed a Tick downloader (SHA256: 80ffaea12a5ffb502d6ce110e251024e7ac517025bf95daa49e6ea6ddd0c7d5b) uploaded to an open malware repository. This sample also had a characteristic pdb file path left in the sample used by Tick.
C:\Users\jack\Desktop\test\ec_new\down_new\Release\down_new.pdb
Although it was uploaded in November 2019, we believe that this sample was used before July 2019 based on the compilation date of the sample and the passive DNS information of the communication destination.
This sample adds the following registry to be automatically executed when the user logs on to the infected device, and copies itself to the registry path.
reg add HKEY_CURRENT_USER\Environment /v UserInitMprLogonScript /t REG_SZ /d "C:\Users\<username>\AppData\Local\Microsoft\Internet Explorer\wuauct.exe" /f
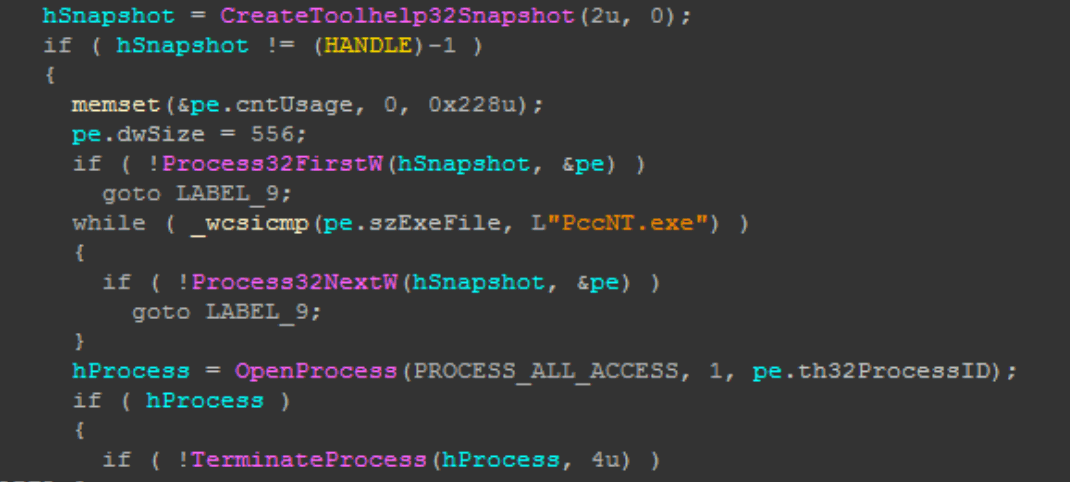
Tickの多くのダウンローダに実装されているアンチウイルス製品を停止する処理が、この検体にも実装されています。
Figure 5. Process of stopping the antivirus product
It encrypts the infected device's MAC address and C drive serial number with AES and base64, uploads it to an external server via HTTP POST, and downloads a new file when a response in the expected format is returned. The communication destination was tampered with and exploited by attackers on a legitimate domestic site.
The AES key is generated using two strings '!@#$%^$$#$%^%$#@' and 'sdjfiejkflmvjfkd' and a random number. This sample attempts to download a file from an external server and exits regardless of success or failure.
In the September 2019 attack on the Chinese base of a chemical company, malware with an improved downloader “down_new”
(SHA256: ec052815b350fc5b5a3873add2b1e14e2c153cd78a4f3cc16d52075db3f47f49) was used.
We call it “version RAT” after the pdb path left behind by this malware.
C:\Users\jack\Desktop\test\version\Release\version.pdb
The malware is a DLL file with the same file name as version.dll installed on Windows, and placed in the same location as the legitimate file that loads version.dll, causing the malware to load instead of the legitimate version.dll. I was doing it. (DLL Search Order Hijacking)
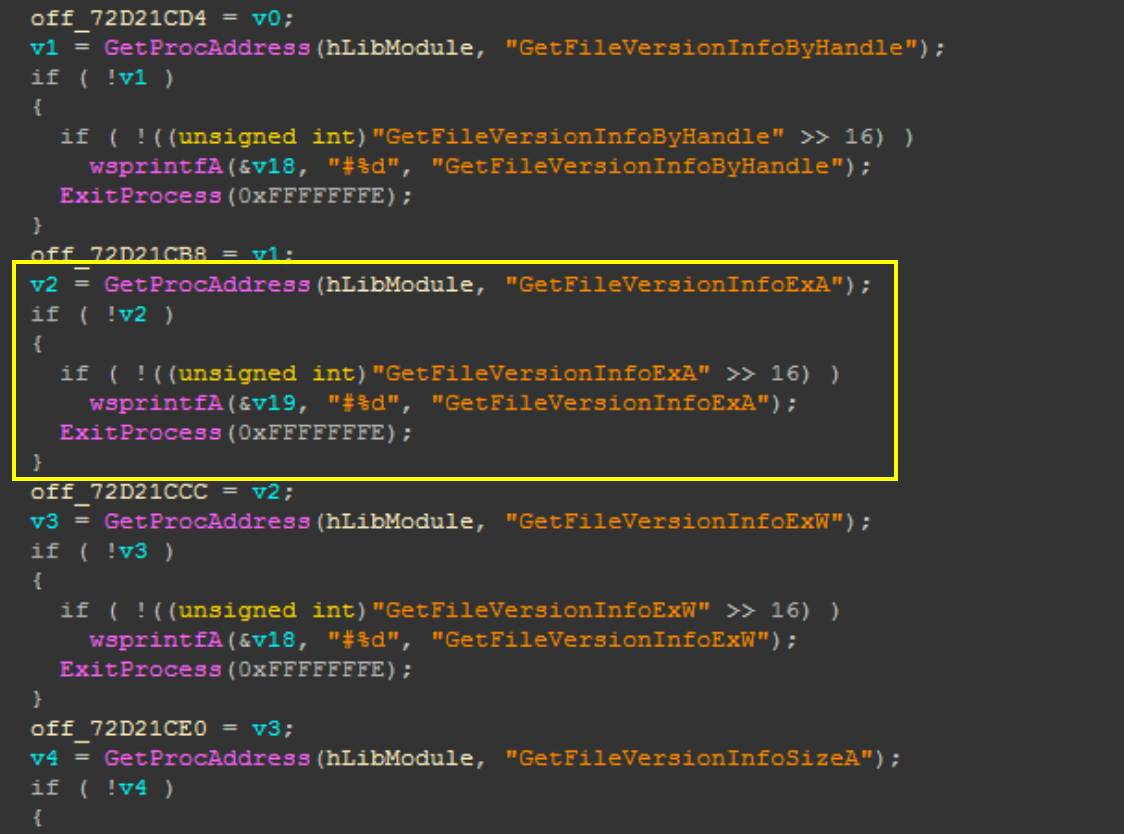
In addition, it uses a characteristic method to determine the OS of the infected terminal.
It loads the legitimate version.dll and checks if a specific API can be loaded. The GetFileVersionInfoExA function is exported by version.dll of Windows 10 and cannot be loaded on other OS. As a result, measures that do not work on OSs other than Windows 10 have been taken.
Figure 6. Process for checking exported functions in version.dll
A major feature of this sample is that in addition to file downloads, simple remote control functions such as remote shell and process list display are implemented.
We believe that version RAT is an improvement of down_new because the code for encrypting communication with AES and base64 and processing to stop antivirus products are the same.
We believe this is to gather information about who we send our next payload to.
| down_new | version RAT | |
|---|---|---|
| file type | exe | DLLs |
| Anti-virus product stop function | can be | can be |
| Persistence method | logon script | Dll Search Order Hijacking (loaded by regular file) |
| Operating environment | Windows 32bit/64bit | Windows 10 |
| Resident | none | can be |
| Communication encryption | AES + base64 | AES + base64 |
| Main function | Download new file | Remote operation (simple) |
Table 1 Function comparison
In this attack, a legitimate domestic site was also altered and used as a C&C server.
Threat Detection and Mitigation Considered from TTP
Malware Delivery
Tick's spear phishing emails exploit compromised legitimate email accounts, create password-protected compressed files, create decoy files that take into consideration the culture of overseas bases, etc., making it extremely difficult for security products to detect and humans to notice. . As a mitigation measure, it is considered necessary to conduct e-mail training and alerts for overseas bases, taking into consideration the local culture that is different from Japan. In addition, it is also effective to check whether the Tick technique used in the attack phase and the intrusion expansion phase can be detected after the malware delivery. We have mapped the techniques we observe that Tick uses to the MITER ATT&CK framework (Table 2). Please check it together with the Tick technique published by the security vendor.
There is BAS (Breach and Attack Simulation) as a solution for evaluating whether security products and security teams that have been introduced can respond as expected. It is also effective to use it to evaluate during normal times.
About attack
Although we have not observed any zero-day attacks on Office or attacks exploiting new vulnerabilities, routine patch management can be an effective mitigation measure in terms of controlling the ease of infiltration by attackers. In particular, it is necessary to give priority to the vulnerabilities of devices that can be accessed from the Internet.
RAT to be installed, remote control (about C&C)
Recently observed attacks rarely use XXMM and Datper, which have been observed in the past, and often exploit various downloaders and public tools, making detection difficult. Loaders that download RAT function code from a C&C server and run malicious code only in memory can be detected by memory scanning. Since it alters legitimate sites in Japan and South Korea and uses them as C&C, it is difficult to detect with signature-based network sensors. However, there are cases where it is difficult for attackers to change (or they are not careful enough), and there are samples that use a fixed user agent. In that case, it is possible to detect it with a rule based on its characteristics.
In terms of network detection, NDR (Network Detection & Response) products that detect anomalous communications can be expected to be effective.
Expansion of intrusion/purpose execution
EDR products are effective in detecting the internal activities of attackers after a break-in. However, as a high-threat detection pattern of general EDR products, there are many phases that create a foothold for MITER ATT&CK attacks (Initial Access/Execution/Persistence/Privilege Escalation/Defense Evasion), and attackers create footholds. After this phase, it seems that the detection pattern of the product tends to make it difficult to detect attacks when it starts to move internally by remote control using authorized commands. In particular, in cases where targeted attacks have started before the introduction of EDR products, the phase of creating a foothold has already been completed, so there is concern that the product's detection patterns may fail to detect them. When EDR products are introduced, analyze from the viewpoint of the execution status of regular commands included in logs collected periodically and whether those commands are frequently executed by terminals owned by people other than IT engineers. Please be careful not to miss detection of attacks.
| Tactic | Technique | identification | remarks |
|---|---|---|---|
| Initial access | Exploit Public-Facing Application | T1190 | Exploiting vulnerabilities in domestic asset management software |
| Spearphishing attachment | T1193 | Delivered from spoofed or compromised email accounts | |
| Supply Chain Compromise | T1195 | Deliver attack emails to overseas bases | |
| Execution | Exploitation for Client Execution | T1203 | Exploiting vulnerabilities in Office products |
| User Execution | T1204 | Disguise an icon and have the recipient run it | |
| Command-Line Interface | T1059 | start bat to delete files | |
| Service execution | T1035 | Start as service | |
| Rundll32 | T1085 | Used for independent execution of DLL | |
| Persistence | New Service | T1050 | Service registration |
| DLL Search Order Hijacking | T1038 | Name it the same as the DLL used by the regular file and place it in the same folder | |
| Logon Scripts | T1037 | Add registry to autorun at logon | |
| Registry Run Keys / Startup Folder | T1060 | Add registry/copy to startup directory so that it will be automatically executed after rebooting the infected device | |
| Defense Evasion | Binary Padding | T1009 | Bloated file to drop |
| Deobfuscate/Decode Files or Information | T1140 | Attempts to avoid detection by obfuscating strings inside samples | |
| Code Signing | T1116 | Add stolen signature | |
| Disabling Security Tools | T1089 | stop antivirus | |
| Software Packing | T1045 | Use commercial packers, etc. | |
| Process Hollowing | T1093 | Launch svchost.exe, injection | |
| File Deletion | T1107 | Delete obsolete files | |
| Hidden Files and Directories | T1158 | Set hidden attribute to dropped file | |
| DLL Side-Loading | T1073 | Equipped with regular EXE that loads DLL (malware) | |
| Credential Access | Credential dumping | T1003 | Use Mimikatz |
| Discovery | System Information Discovery | T1082 | File search with dir command |
| Account Discovery | T1087 | Search for users with the net user command | |
| Network Share Discovery | T1135 | Search by net share, net view command | |
| System Network Connection Discovery | T1049 | Search remote desktop etc. with netstat command | |
| Process Discovery | T1057 | Search with the tasklist command | |
| Lateral movement | Windows Admin Shares | T1077 | Using PsExec to spread infection |
| Remote File Copy | T1105 | Use RAT such as Datper to upload/download files to infected devices | |
| Collection | Data from Local System | T1005 | Collect infected device information using cmd |
| Command and control | Commonly used ports | T1043 | use 80, 443 |
| Custom Cryptographic Protocol | T1024 | Encrypt using AES, RC4, XOR, etc. | |
| Data encoding | T1132 | Encode communication using base64 | |
| Data Obfuscation | T1001 | Downloading an image file with embedded malware | |
| Standard Application Layer Protocol | T1071 | Communicate with C&C server via HTTP, HTTPS | |
| Standard Cryptographic Protocol | T1032 | Encrypt HTTP transmission data with RC4, AES | |
| Web Service | T1102 | Alters legitimate websites and uses them as C&C servers | |
| Exfiltration | Exfiltration Over Command and Control Channel | T1041 | Upload files to C&C server using RAT |
| Data Compressed | T1002 | Compress files with zip and makecab commands |
Table 2 MITER ATT&CK Techniques
The techniques in red are those that we believe should be observed more often at our company and emphasized on confirmation.
以下Tickに関連するインディケータは、大半が過去弊社レポートに含まれているものですが、インシデント調査、対応にてご活用頂ければと考え改めて記載します。
| indicator | type | remarks |
|---|---|---|
| a04d2668b1853051dd5db78721b7deae7490dbd60cef96d55cc91ff8c5d4730d | SHA256 | XXMM |
| d91894e366bb1a8362f62c243b8d6e4055a465a7f59327089fa041fe8e65ce30 | SHA256 | Datper |
| 706a6833b4204a89455f14387dbfc4903d18134c4e37c184644df48009bc5419 | SHA256 | Datper |
| fdd4a4b3d56217579f4cd11df65cf4bd4c60cac428aa649d93227604fbb8b49e | SHA256 | Exploit ppsx |
| 569ceec6ff588ef343d6cb667acf0379b8bc2d510eda11416a9d3589ff184189 | SHA256 | Datper |
| e38d3a7a86a72517b6ebea89cfd312db0f433385a33d87f2ec8bf83a62396bb3 | SHA256 | Datper |
| 6530f94ac6d5b7b1da6b881aeb5df078fcc3ebffd3e2ba37585a37b881cde7d3 | SHA256 | Datper |
| 569ceec6ff588ef343d6cb667acf0379b8bc2d510eda11416a9d3589ff184189 | SHA256 | Datper |
| 0542ecabb7654c6fd6fc4e12fe7f5ff266df153746492462f7832728d92a5890 | SHA256 | RAT Loader |
| d705734d64b5e8d61687db797d7ad3211e99e4160c30ba209931188f15ced451 | SHA256 | RAT Loader |
| 3f5a5819d3fe0860e688a08c1ad1af7208fe73fd9b577a7f16bcebf2426fbdaf | SHA256 | RAT Loader |
| 911fbd95e39db95dbfa36ff05d7f55fc84686bbe05373fc2f351eb76a15d9d74 | SHA256 | Downloader |
| 337d610ebcc9c0834124f3215e0fe3da6d7efe5b14fa4d829d5fc698deca227d | SHA256 | Downloader |
| 706a6833b4204a89455f14387dbfc4903d18134c4e37c184644df48009bc5419 | SHA256 | Downloader |
| 58b06982c19f595e51f0dc5531f6d60e6b55f775fa0e1b12ffd89d71ce896688 | SHA256 | Downloader |
| 1fdd9bd494776e72837b76da13021ad4c1b3a47c8a49ca06b41dab0982a47c7e | SHA256 | Dropped Word Plugin DLL |
| fb0d86dd4ed621b67dced1665b5db576247a10d43b40752c1236be783ac11049 | SHA256 | Downloader |
| d1307937bd2397d92bb200b29eeaace562b10474ff19f0013335e37a80265be6 | SHA256 | Downloader |
| 32dbfc069a6871b2f6cc54484c86b21e2f13956e3666d08077afa97d410185d2 | SHA256 | Downloader |
| 80ffaea12a5ffb502d6ce110e251024e7ac517025bf95daa49e6ea6ddd0c7d5b | SHA256 | down_new |
| ec052815b350fc5b5a3873add2b1e14e2c153cd78a4f3cc16d52075db3f47f49 | SHA256 | version RAT |
| http://www[.]cheapraybanoutletonline[.]com/fooler.php | C2 | XXMM |
| http://www[.]<redacted>[.]co[.]jp/halftime/other/goods.php | C2 | Datper |
| www[.]aromatictree[.]co[.]kr | C2 | Datper |
| http://211.233.81[.]242/hp.php | C2 | Datper |
| robot[.]softsrobot[.]com:443 | C2 | RAT Loader |
| www[.]runinngboys[.]com:443 | C2 | RAT Loader |
| dns[.]safedexperiences[.]com | C2 | RAT Loader |
| google[.]safedexperiences[.]com | C2 | RAT Loader |
| web[.]birthhappiness[.]com | C2 | RAT Loader |
| www[.]birthhappiness[.]com | C2 | RAT Loader |
| www[.]efficitivesubject[.]com | C2 | RAT Loader |
| www[.]korlearn[.]com | C2 | RAT Loader |
| www[.]miniiants[.]com | C2 | RAT Loader |
| www[.]safedexperiences[.]com | C2 | RAT Loader |
| dndns8866[.]com | C2 | RAT Loader |
| efficientsubjectapp[.]com | C2 | RAT Loader |
| korlearn2030[.]com | C2 | RAT Loader |
| Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.0; SV1) | User-Agent | XXMM |
| Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko | User-Agent | Datper |
| d4fy3ykdk2ddssr | Mutex | Datper |
Table 3 Indicative Information (IOC)
The TTPs of other attacker groups BlackTech and Emdivi are listed in the report below, so please refer to them.