
Okta
Octa
Introduction
With Auth0's Adaptive MFA feature, it is possible to request MFA only when a user is identified as a risky user upon login. For example, logins from devices that have not been used in the last 30 days or logins from locations where it is impossible to move due to time or distance from the previous login are judged to be risky and require MFA.
On this page, we will introduce an overview of the Adaptive MFA function and customization of MFA request judgment using the Rules function, divided into several patterns, and introducing the setting method and actual operation.
premise
The operation examples on this page are for Auth0-linked web applications.
In addition, the information regarding functions and settings described on this page is current as of October 2022.
Adaptive MFA feature
The Adaptive MFA function in Auth0 calculates the confidence score and reason (code) based on the three evaluation axes of NewDevice, ImpossibleTravel, and UntrustedIP.
| Evaluation axis | Target risk | Evaluation method |
| New Device | Login attempts from devices that have not logged in for 30 days |
|
| Impossible Travel | Attempting to log in from a location that is impossible due to time or distance from the previous login |
|
| Untrusted IPs | Login attempts from risky IP addresses |
|
Adaptive MFA - How it works - Auth0 docs
Based on the calculated results, we will determine whether or not an MFA request is required. Customize the conditions under which MFA is required using the Actions or Rules function.

Setting overview
The usage settings for the Adaptive MFA function and the customization settings for determining MFA requirements are as follows.
- Enabling Adaptive MFA
- Rule: Enable [ Adaptive MFA ] and [ Require MFA Enrollment ]
- Customization of MFA request judgment by script editing (JavaScript description) in Rule
- Judge MFA request based on Confidence Score value or Codes value calculated by Adaptive MFA function
- Determines MFA requests based on Confidence or Code values calculated by the Adaptive MFA function
Adaptive MFA - assessments object - Auth0 docs
From here, we will introduce specific configuration methods and operation check examples using the Rules function. For configuration methods using the Actions function, please see below.
Implementing custom logic using Auth0 Actions (MFA request determination in Adaptive MFA function)
Setting example (MFA request judgment based on confidence.score value as NewDevice evaluation result)
- On the Auth0 management screen, click [Security] > [Multi-factor Auth]
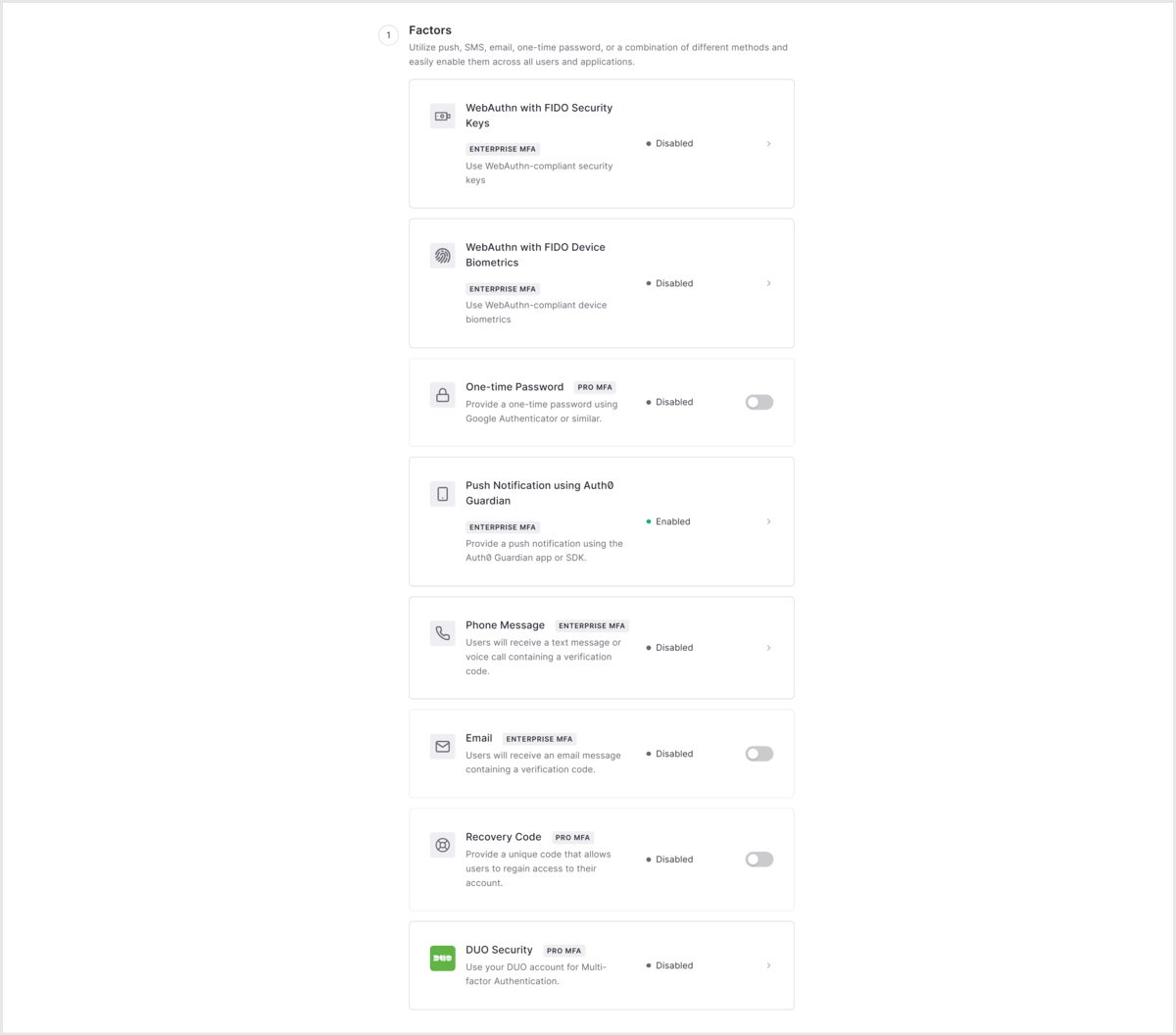
- Enable Optional MFA in Factors
- Select [Use Adaptive MFA] in [Require Multi-factor Auth] and click [Save]
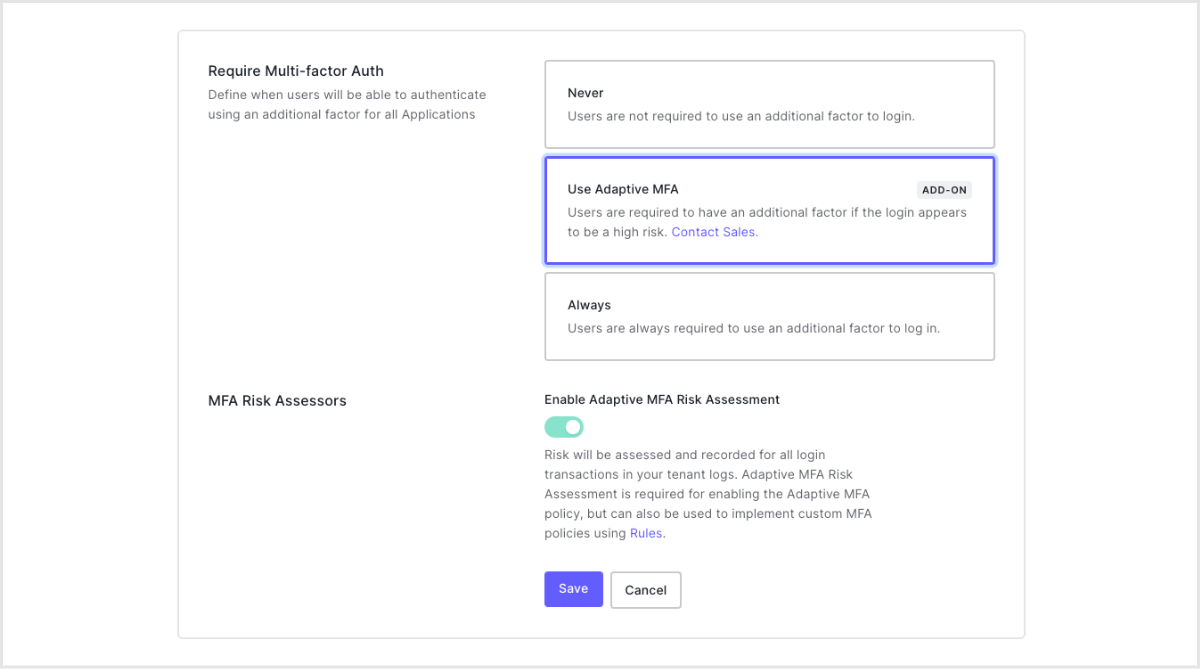
*If you select [Use Adaptive MFA] in MFA Risk Assessors, the risk assessment will be automatically enabled and recorded in the tenant log.
- On the Auth0 management screen, click [Auth Pipeline] > [Rules]
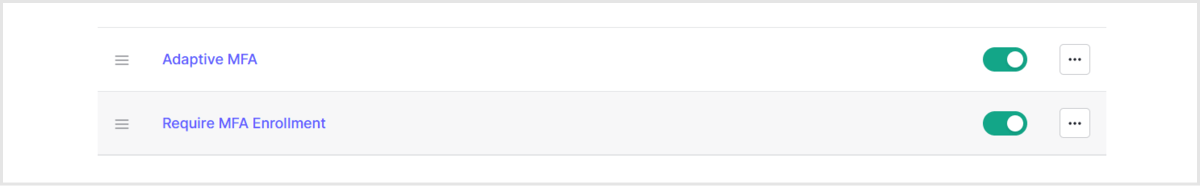
- Enable Rule [ Adaptive MFA ] and [ Require MFA Enrollment ]
- Adaptive MFA: MFA requirement determination based on evaluation results by Adaptive MFA function
- Require MFA Enrollment: Mandatory MFA Enrollment
- Click on the Rule [ Adaptive MFA ] that was activated earlier
Confirm the pre-written processing details (request MFA based on the confidence.score value as the NewDevice evaluation result)
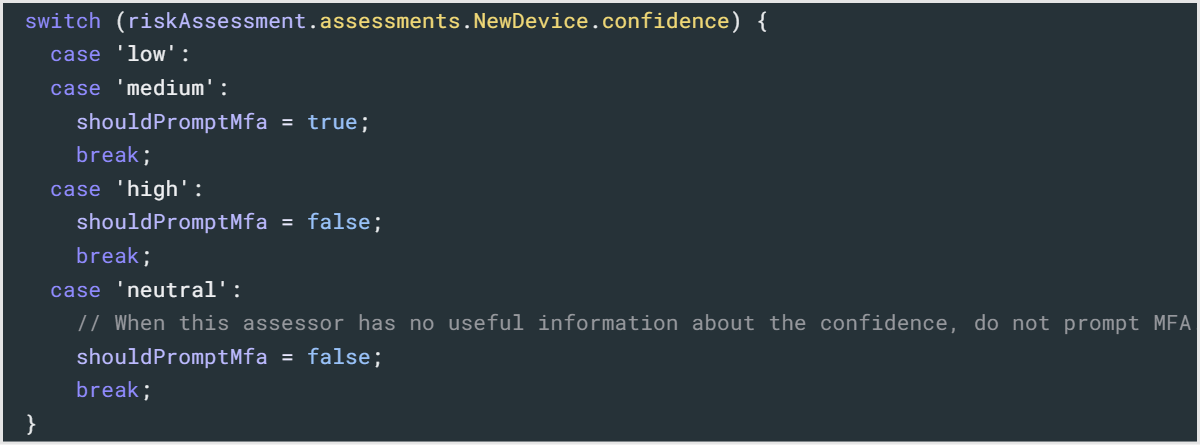
- Add the following to your script for debugging purposes:
- console.log(riskAssessment.assessments.NewDevice.confidence);
- Log confidence score value
- console.log(shouldPromptMfa);
- Log output of judgment result of whether to activate MFA (activated by true)
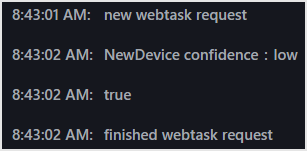
Operation confirmation example: Attempting to log in with a device different from the previous login
- Perform login/logout operations on the web application screen linked with Auth0. Make sure this login operation does not require MFA
- In order to let the Adaptive MFA function determine that the login is from a new device, perform a login operation with a different UserAgent web browser from the previous login.
- Make sure MFA is required at login

(Supplement) Rule: Judgment processing log output in Adaptive MFA
Rule: Logs related to judgment processing within Adaptive MFA are not output to the Auth0 tenant log (Monitoring > Logs), so check the log output in the following way.
- Arbitrary log output is possible by describing console.log in the script of Rule

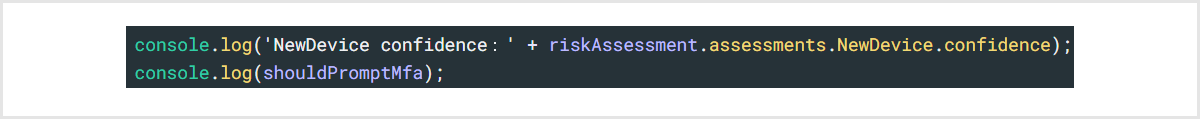
Setting example (MFA request judgment based on codes value as NewDevice evaluation result)
- Customization example of Rule [ Adaptive MFA ]
- switch statement: Changed to process to judge MFA request by reason (code) of reliability score with NewDevice as evaluation axis
- console.log: Changed to log the reason (code) value for debugging purposes.
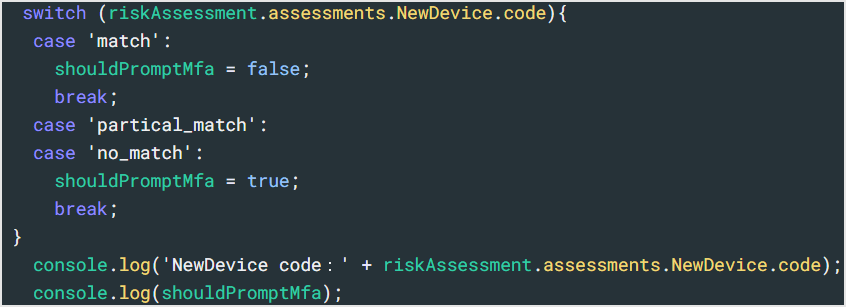
Operation confirmation example
- Perform login/logout operations on the web application screen linked with Auth0. Make sure this login operation does not require MFA
- In order to determine that the device is different from the one used when logging in last time, perform a login operation using a web browser with a UserAgent different from the one used when logging in last time.
- Make sure MFA is required at login
- Log output on the Real-time Webtask Logs screen: Check the reason (code) value
Setting example (MFA request judgment based on confidence.score value as ImpossibleTravel evaluation result)
- Customization example of Rule [ Adaptive MFA ]
- switch statement: Change to process to judge MFA request by confidence score (confidence.score) with ImpossibleTravel as evaluation axis
- console.log: changed to log confidence score (confidence.score) and reason (code) values for debugging purposes
![Customization example of Rule [ Adaptive MFA ]](/business/security/okta/image/okta_tech_auth0_mfa_dr14.png)
![Customization example of Rule [ Adaptive MFA ]](/business/security/okta/image/okta_tech_auth0_mfa_dr15.png)
Operation confirmation example
- Perform login/logout operations from within Japan on the web application screen linked with Auth0. Make sure this login operation does not require MFA
- Immediately after 1., log in from a place where it is impossible to log in due to time and distance (such as the United States).
- Make sure MFA is required at login
- Log output on the Real-time Webtask Logs screen: Check the reason (code) value
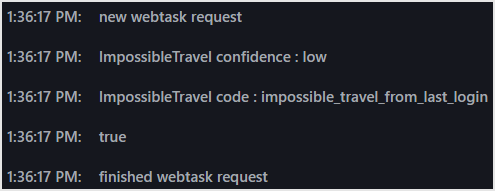
Summary
By using Auth0's Adaptive MFA feature, you can implement risk-based control of MFA requests in the authentication process. In addition, you can customize the MFA request determination by coding with the Rules function. For customization, version control, testing, and debugging functions necessary for coding are also provided in advance.
You can also try the Adaptive MFA feature in the free Auth0 trial environment. If you are interested in Auth0's Adaptive MFA feature, please contact us.
reference
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00