
Okta
Octa
I played around with Okta's session lifetimes and authentication factors.
Introduction
In this article, I will explain how to freely set the Okta session lifetime and authentication factor requirements according to it through a concrete example.
SAML authentication flow in Okta
The flow of authentication in Okta is as shown in the figure below.
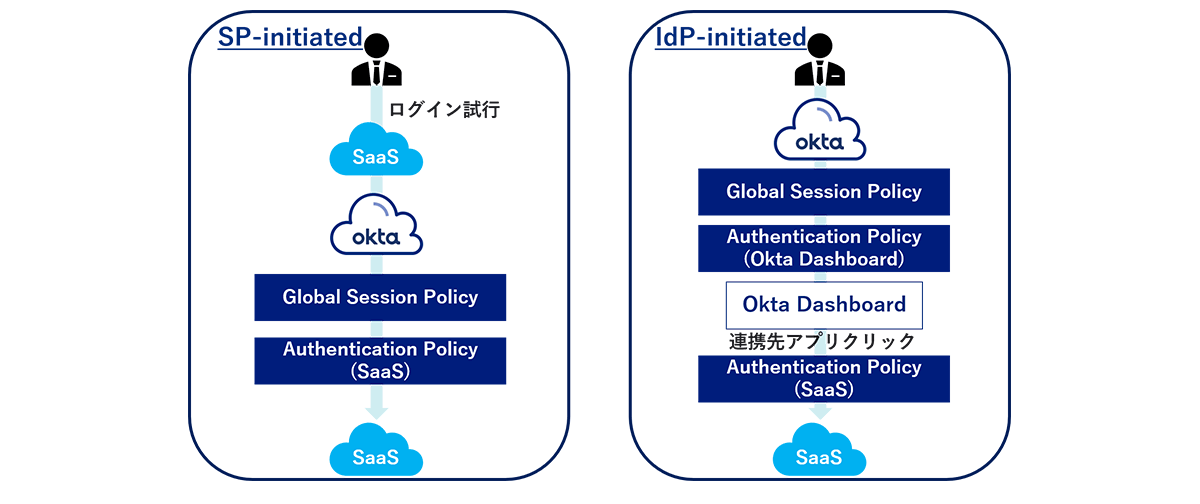
- SP-initiated
Authentication flow when directly accessing the linked Service Provider (SP) in Single Sign-on - IdP-initiated
In Single Sign-on, authentication flow when accessing Identity Provider (IdP) like Okta and then accessing SP
The specific authentication flow is explained below.
For SP-initiated
- Login attempt to SaaS
- Authentication is requested by Okta, and the screen transitions to Okta's authentication screen.
- Authentication according to the policy is requested in the order of Global Session Policy → Authentication Policy (SaaS), and the user enters the authentication factor
- Authentication process completed
- A SAML authentication response is issued from Okta and you can log in to SaaS
For IdP-initiated
- Access Okta and transition to the Okta authentication screen
- Authentication according to the policy is requested in the order of Global Session Policy → Authentication Policy (Okta Dashboard), and the user enters the authentication factor
- After completing the authentication process, log in to the Okta Dashboard
- On the Okta Dashboard, click SaaS
- (If there are additional authentication factors) authentication according to Authentication Policy (SaaS) is required, and the user enters the authentication factors
- Authentication process completed
- A SAML authentication response is issued and you can log in to SaaS
This time, we will explain the session lifetime and authentication factors in SAML authentication of SP-init.
What is the session lifetime that can be set in Okta?
- Okta session lifetime according to time Okta is not in use
- Reauthentication session lifetime for each authentication factor when signing in to the Okta Dashboard or a specific SaaS
For 1., set in [Expire session after user has been idle on Okta for] in the corresponding Rule of Global Session Policy,
For 2., set in [Re-authentication frequency is] in the corresponding Rule of Authentication Policies.
Understanding the Lifetime and Authentication Behavior of Each Configured Session
When the lifetime of each set session expires, the operation of authentication is as shown in the figure below.
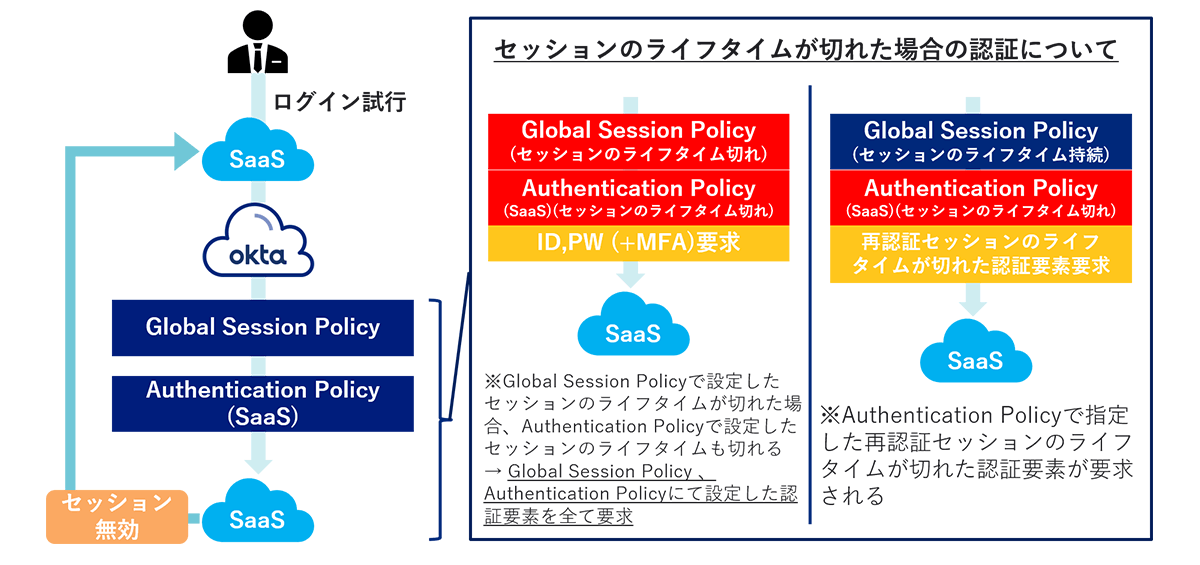
When the session lifetime set in the Global Session Policy has expired
In this case, the lifetime of the re-authentication session for each authentication factor set in the Authentication Policy assigned to SaaS will also expire.
Therefore, during authentication, not only the authentication factors specified in the Global Session Policy, but also all the authentication factors specified in the Authentication Policy are required from ID confirmation.
When the lifetime of the re-authentication session set in the Authentication Policy has expired
In this case, the session lifetime set in the Global Session Policy will not expire at the same time.
Therefore, ID verification is not required during authentication, and only the authentication factors whose re-authentication session lifetime has expired are requested among the authentication factors specified in the Authentication Policy.
Concrete example and setting method
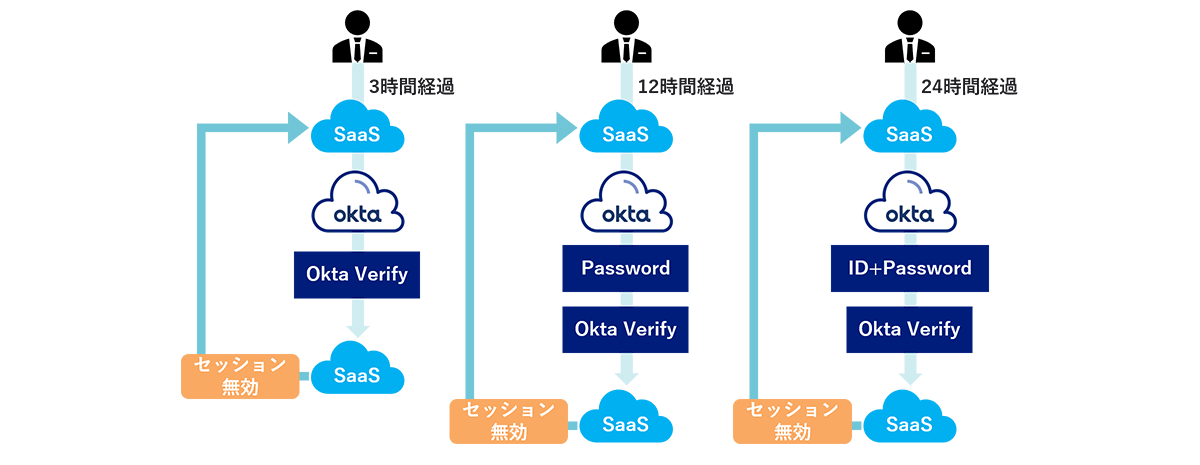
Now, let's take a look at an example of a setting that actually changes the requested authentication factor for each elapsed time.
In this case, we will use an example of changing authentication factors to users who have been 3, 12, and 24 hours since their last login to Okta, respectively.
- 3 hours passed → Okta Verify
- 12 hours passed → Password + Okta Verify
- After 24 hours → ID, Password + Okta Verify
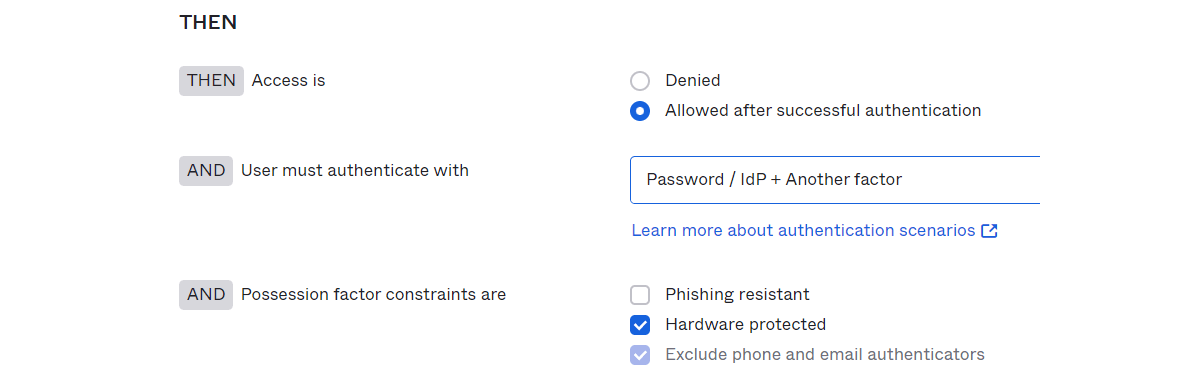
First, set as follows in the corresponding Rule of Authentication Policies on the Okta management screen.
- Select the authentication factor required when logging into the target SaaS (Password + Okta Verify)
- In "User must authenticate with", select [Password + Another factor]
- In "Possession factor constraints are", check [Hardware protected]
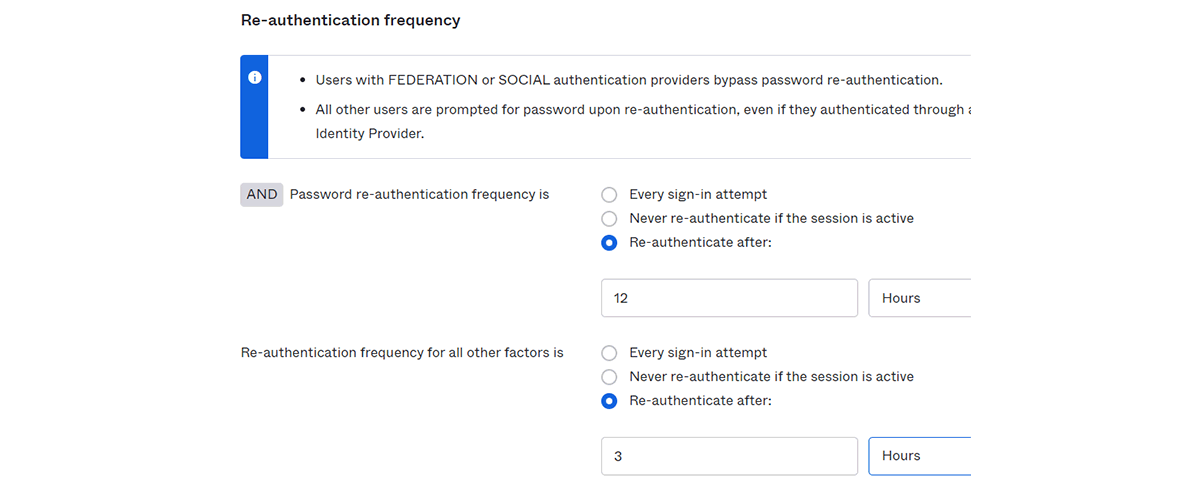
- Set Okta Verify reauthentication session lifetime to 3 hours
Check [Re-authenticate after: ] in Okta Verify's "Re-authentication frequency is" and set to [3 hours] - Set password reauthentication session lifetime to 12 hours
Check [Re-authenticate after: ] in Password re-authentication frequency is and set to [12 hours]
Finally, set the following in the corresponding Rule of Global Session Policy on the Okta management screen.
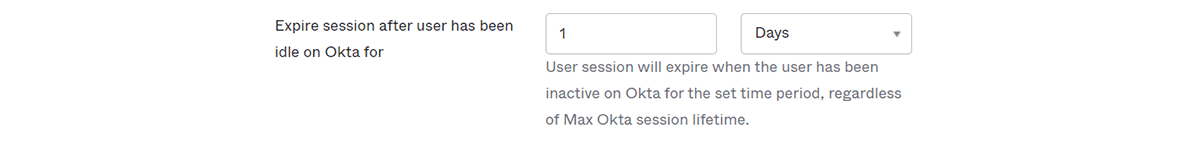
- Set lifetime of session to Okta itself to 24 hours
Set "Expire session after user has been idle on Okta for" to [1 days]
Summary
I hope you understand Okta's session lifetime and authentication.
One of the attractions of Okta is that you can set the session lifetime for each authentication factor as well as the session lifetime for Okta itself, and you can freely request authentication factors according to the elapsed time.
If you are interested or have any other inquiries about Okta, please contact us.
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00

