
Okta
Octa
Brief description
About Device Trust

How Device Trust works for iOS devices
Device trust is performed on the condition that the device participates in MDM. (Participated in MDM -> Considered as an authorized device)
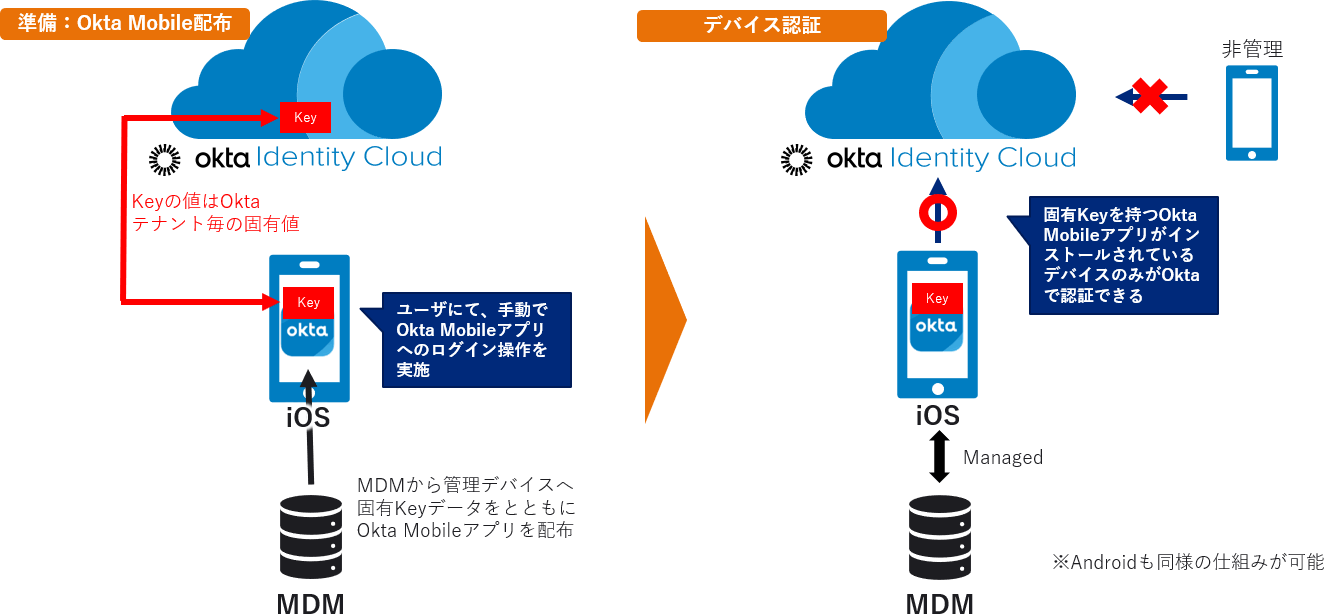
iOS device trust setup flow
Device Trust for iOS gives a secret key on the MDM side such as Ivanti MobileIron (formerly MobileIron), Microsoft Endpoint Manager (formerly Intune), and VMware WorkSpace One.
This is achieved by registering the Okta Mobile app and distributing Okta Mobile to target iOS devices.
If a user logs in using Okta Mobile without a secret key, it is possible to deny access to a specific application by determining that the device is not a trusted device because there is no secret key. .
Follow the steps below to configure the settings.
- Enable iOS device trust on Okta side and issue a secret key
- Register the Okta Mobile app with a secret key on the MDM side and distribute the app to the target iOS devices
- Applies policy settings to control access to applications on the Okta side
- Enable Device Trust on Okta side
- Register Okta app on MDM side (for Ivanti MobileIron)
- Enroll the Okta app on the MDM side (for Microsoft Endpoint Manager)
- Set policy on Okta side
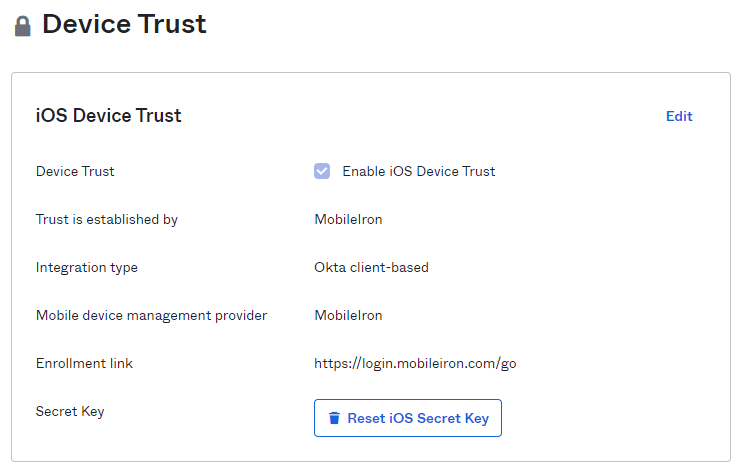
Enable Device Trust on Okta side
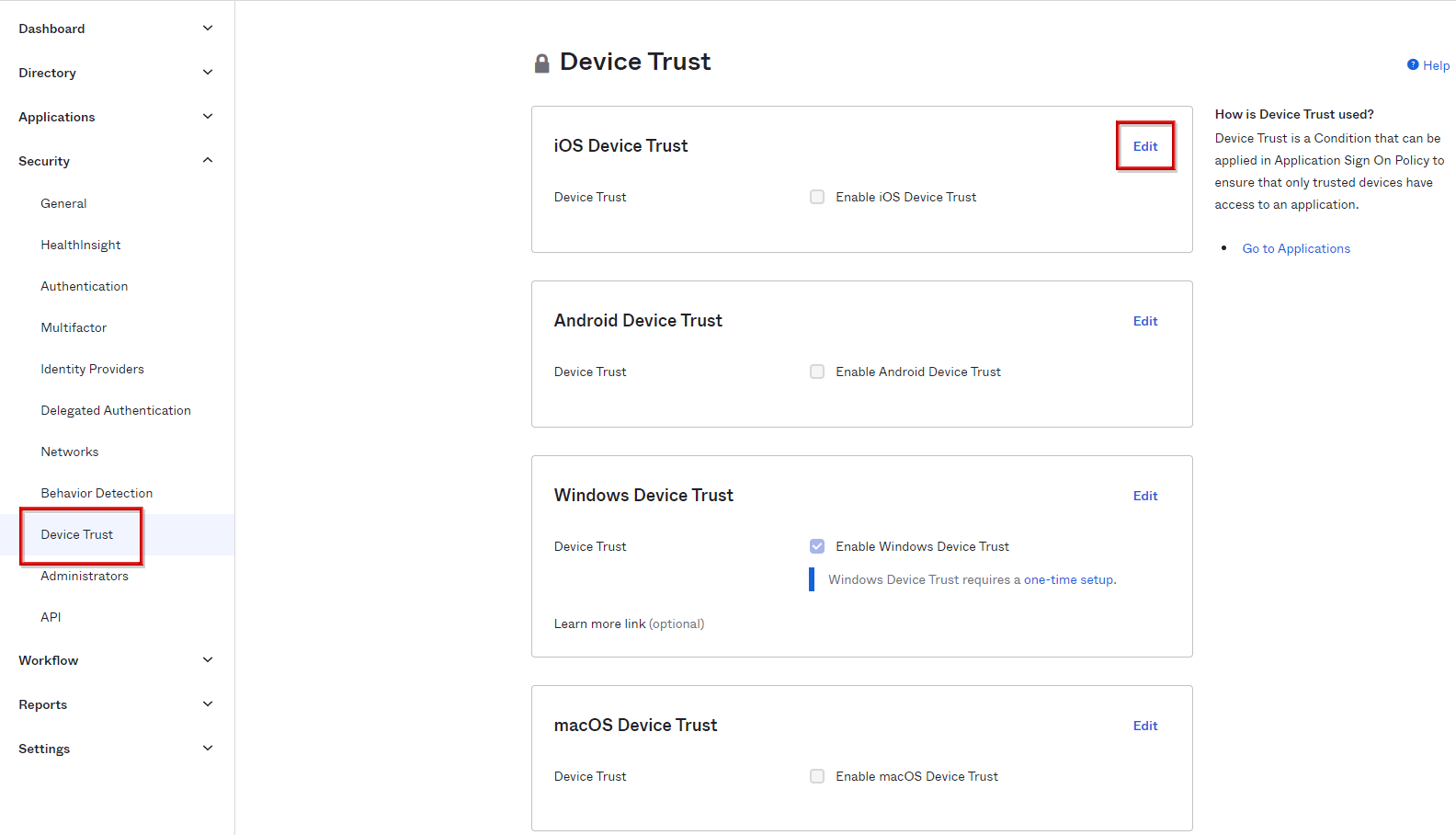
- Go to Security > Device Trust screen and click Edit of iOS Device Trust
- Check Enable iOS Device Trust, select MDM, and click Next
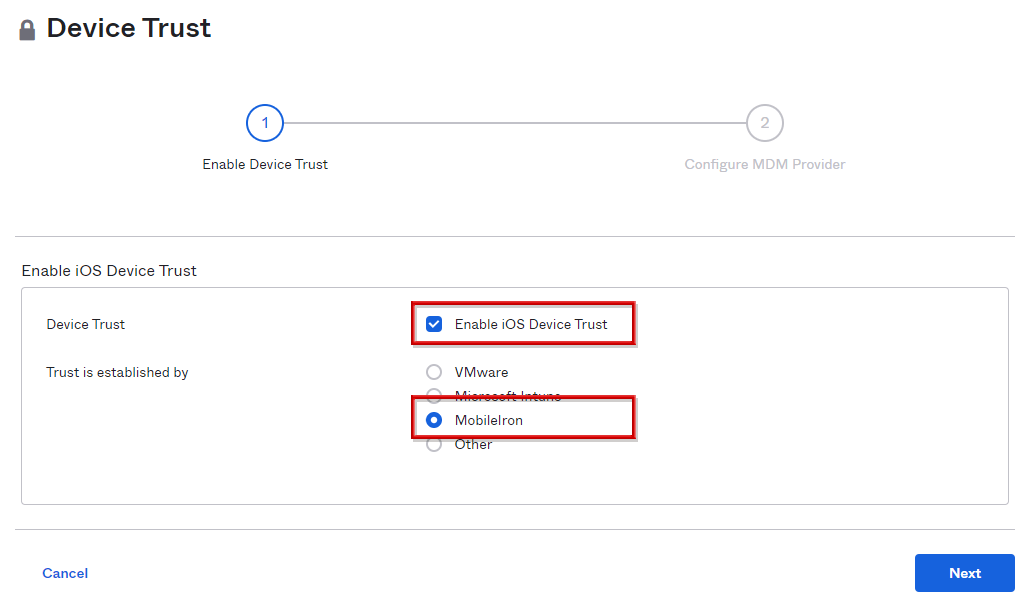
*In the above example, select MobileIron
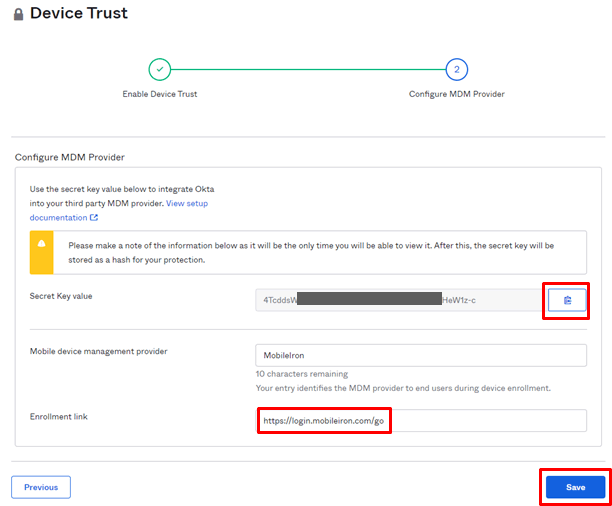
- Copy the Secret Key value to the clipboard, enter the URL for MDM enrollment (optional) in the Enrollment link, and click SAVE
*The URL for MDM registration is displayed to the user to prompt MDM registration when an MDM non-registered device accesses. (Do not set if you do not want to prompt MDM enrollment for non-MDM enrolled devices)
- Confirm that there is no problem with the iOS device trust settings, and complete the activation settings
Register Okta app on MDM side (for Ivanti MobileIron)
- Open the management screen of the selected MDM and transition to the application setting screen
* It is assumed that the application from the MDM side can already be distributed to the target iOS device.
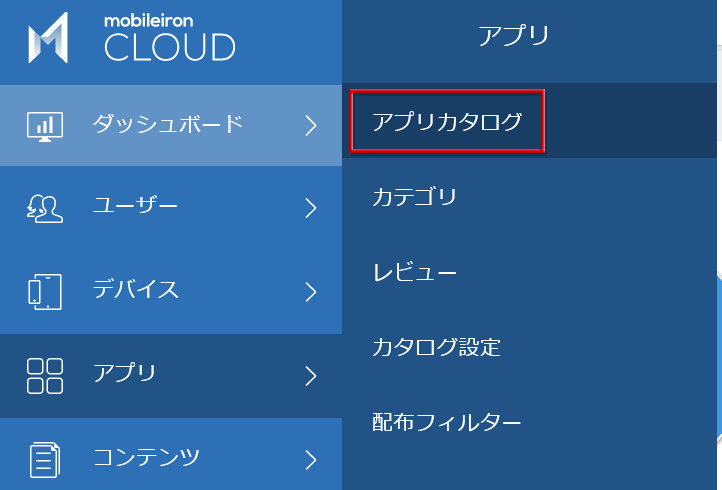
*In the above example, the management screen of Ivanti MobileIron
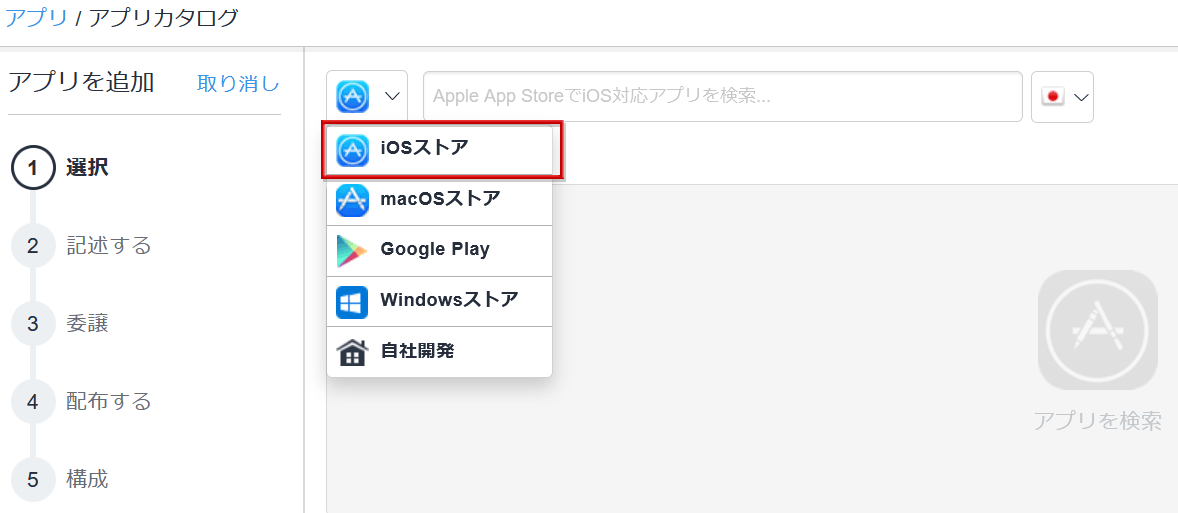
- Click Add and select iOS Store App in App Type
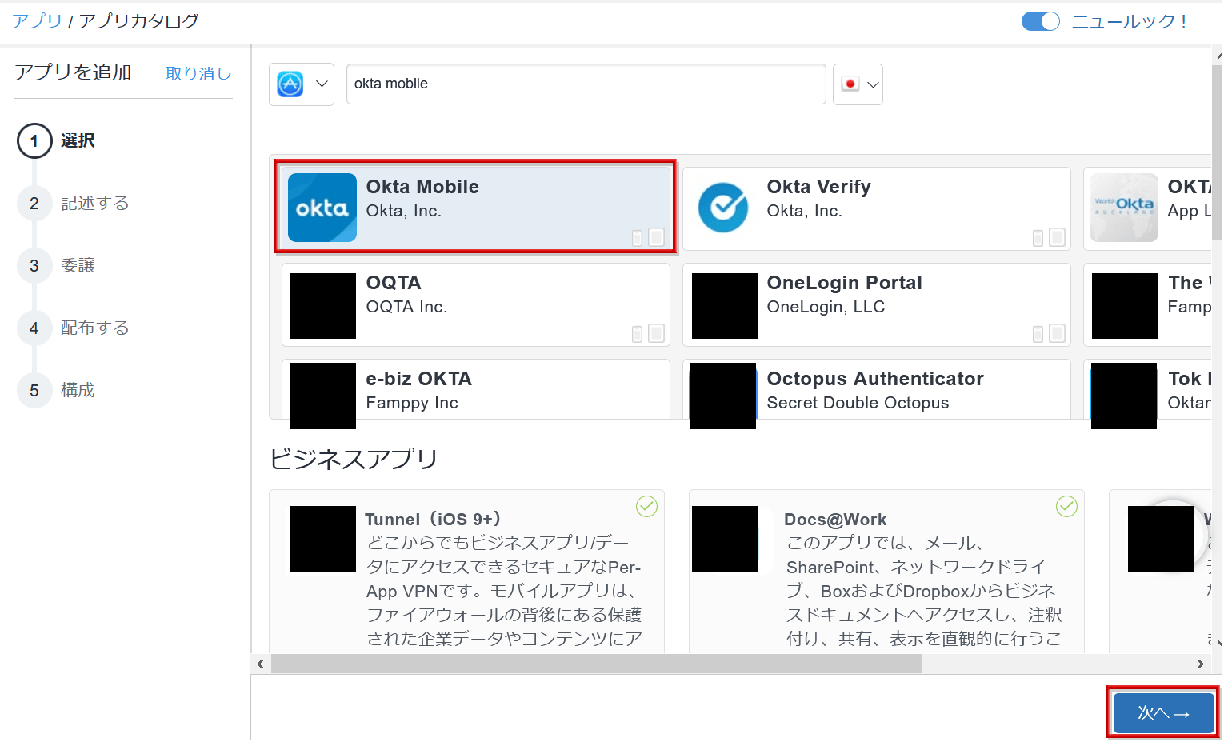
- Enter Okta Mobile in the search window, select Okta Mobile and click Next
- Okta Mobile information will be reflected, so click next
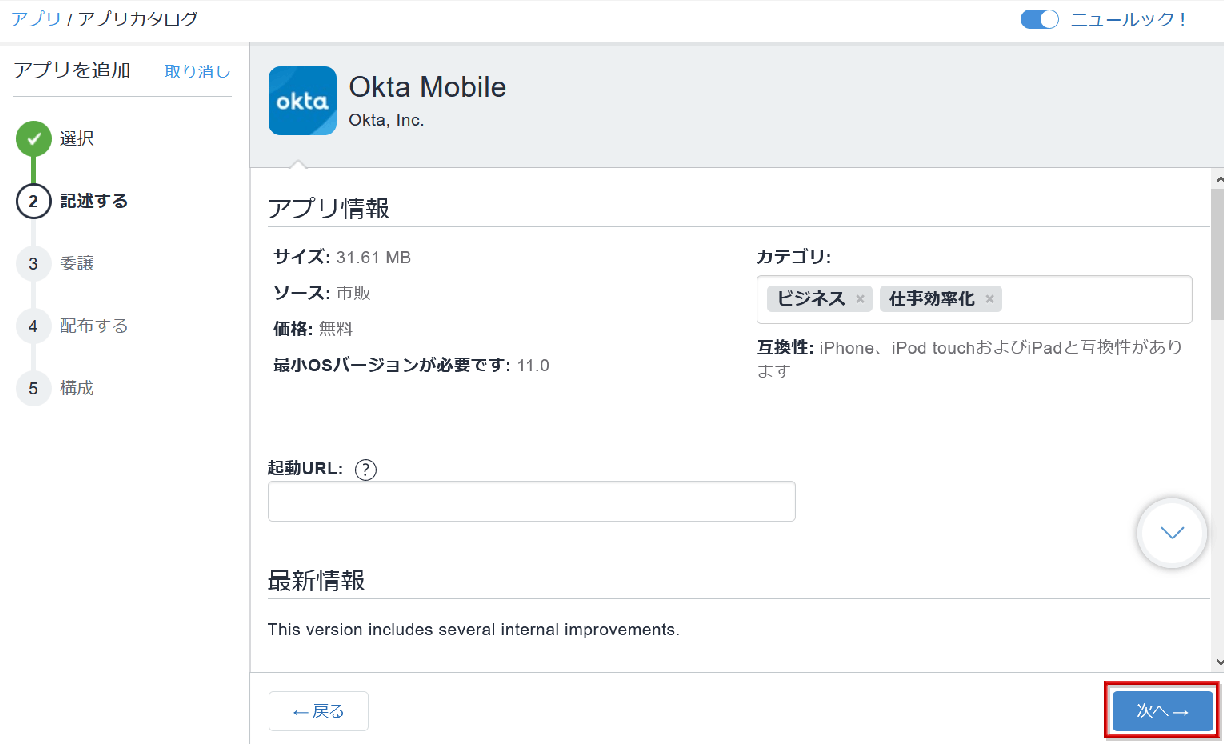
- After configuring the user groups to distribute Okta Mobile to, click Next
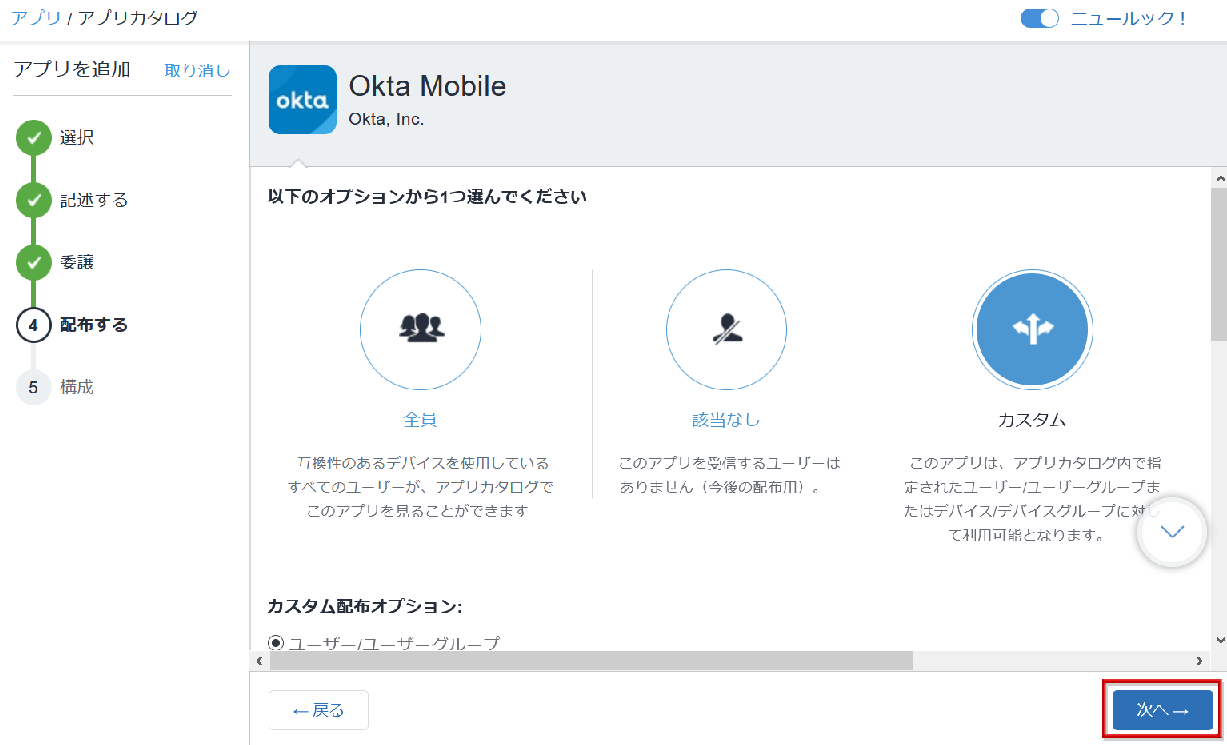
- After confirming the information of Okta Mobile to be added, click Done. Completion of adding the app (Okta Mobile) itself
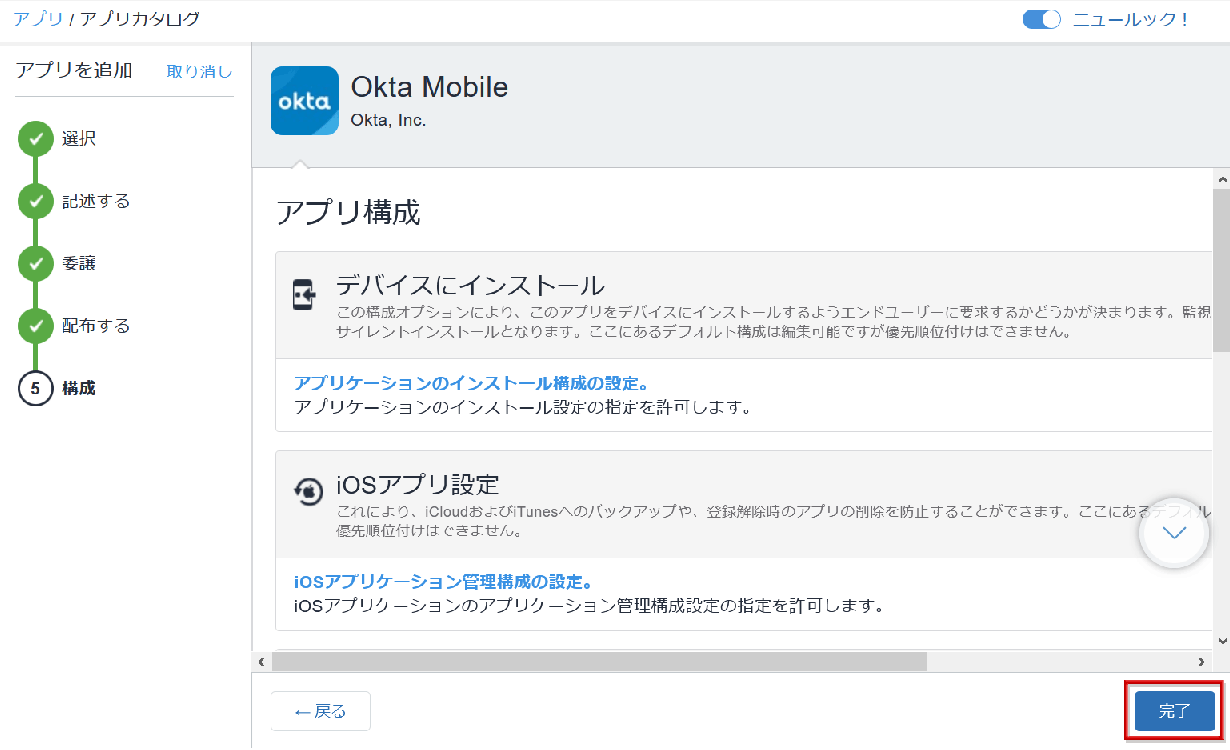
- In order to assign Okta side secret to the added Okta Mobile, select iOS managed app configuration on Okta Mobile's app configuration tab.
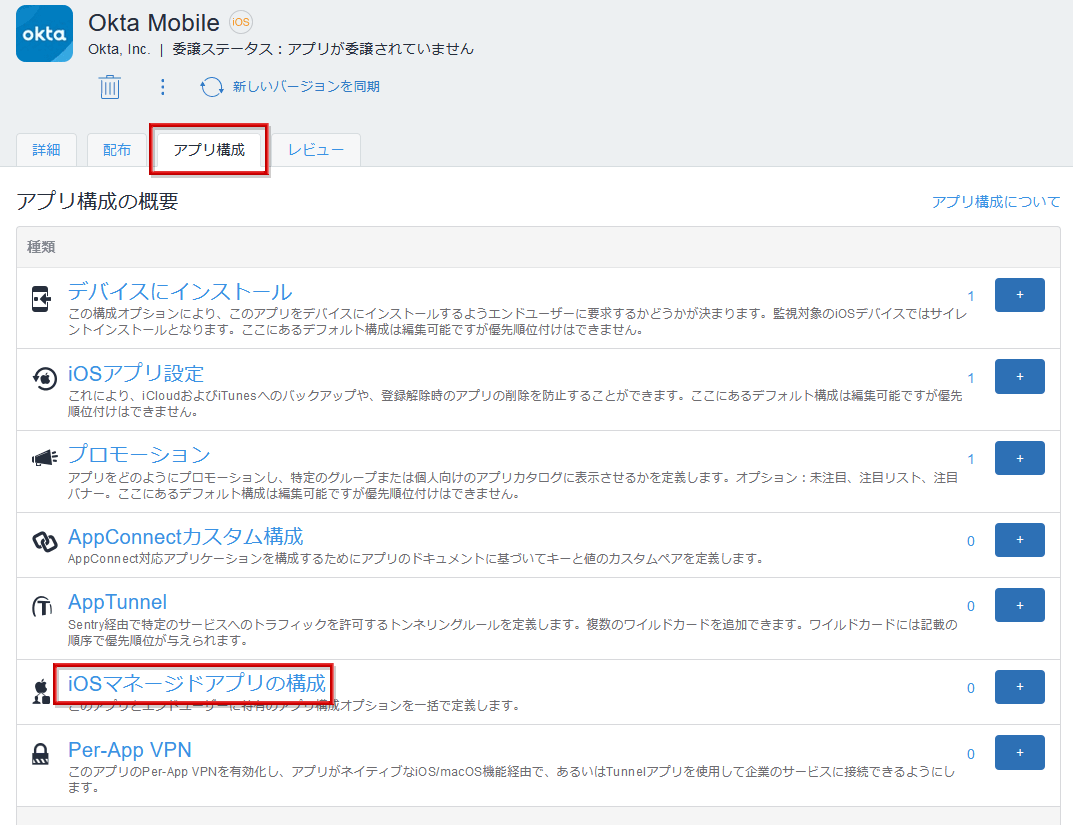
- select add
- Enter any name
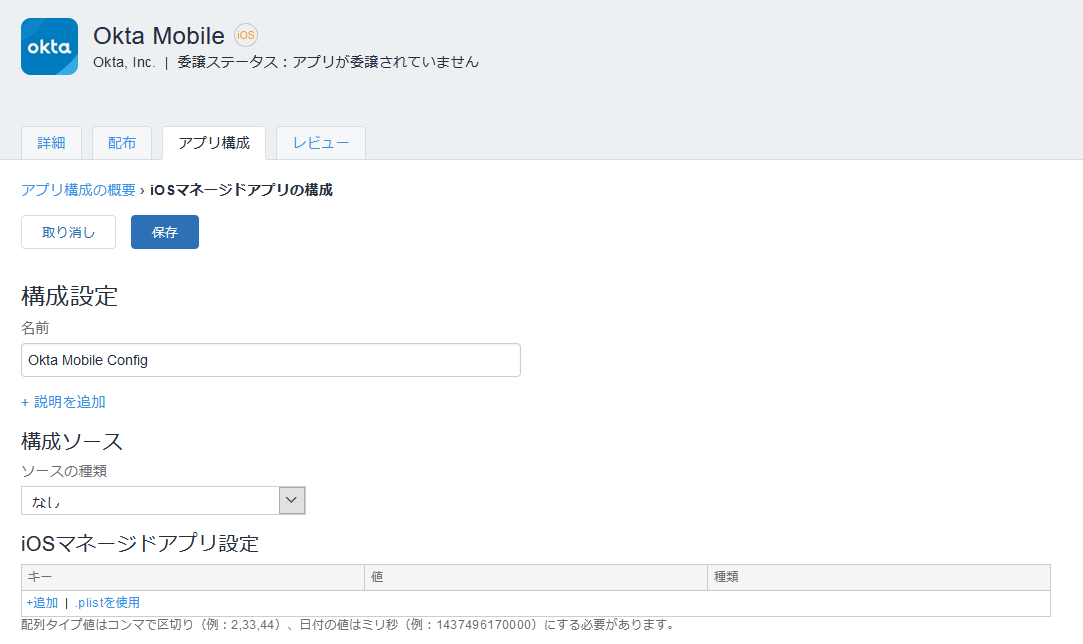
- Click Add iOS Managed App Configuration and enter the following information:
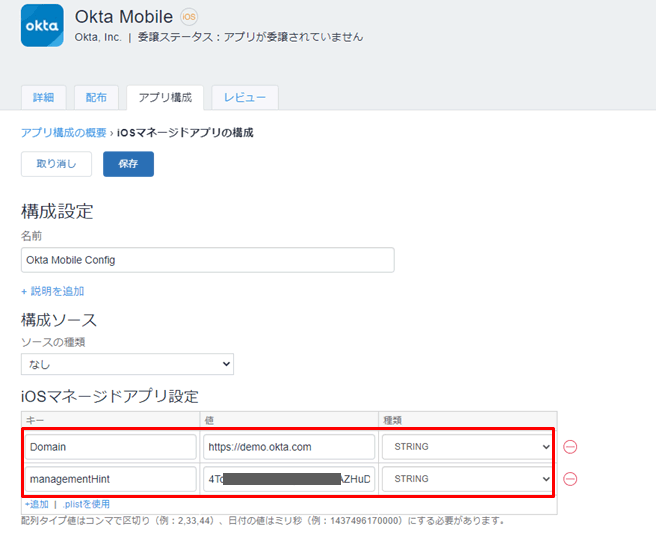
- Domain: Okta Tenant URL (e.g. https://demo.okta.com)
- managementHint: Secret Key that you copied in advance
- Set the configuration distribution target and click Save
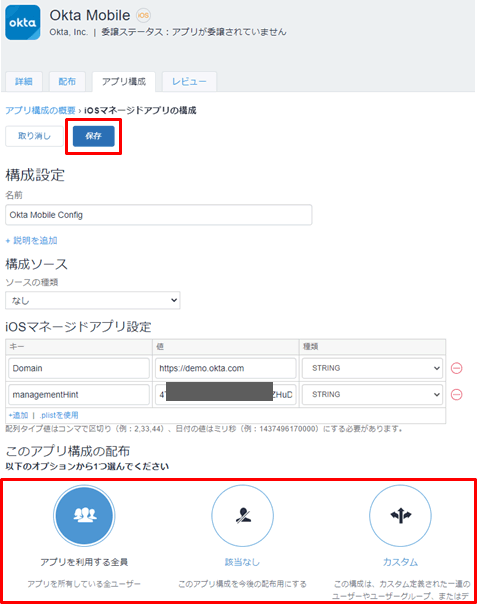
- If the added configuration is displayed in the list, the setting on the MDM side is complete.
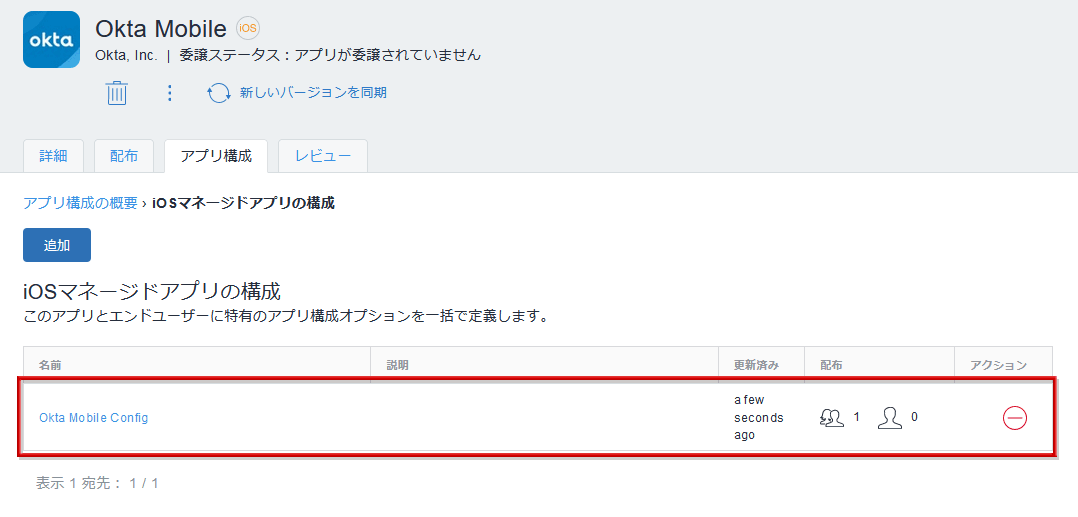
Enroll the Okta app on the MDM side (for Microsoft Endpoint Manager)
- Open the management screen of the selected MDM and transition to the application setting screen
*It is assumed that the target iOS device is already ready to distribute the application from the MDM side.
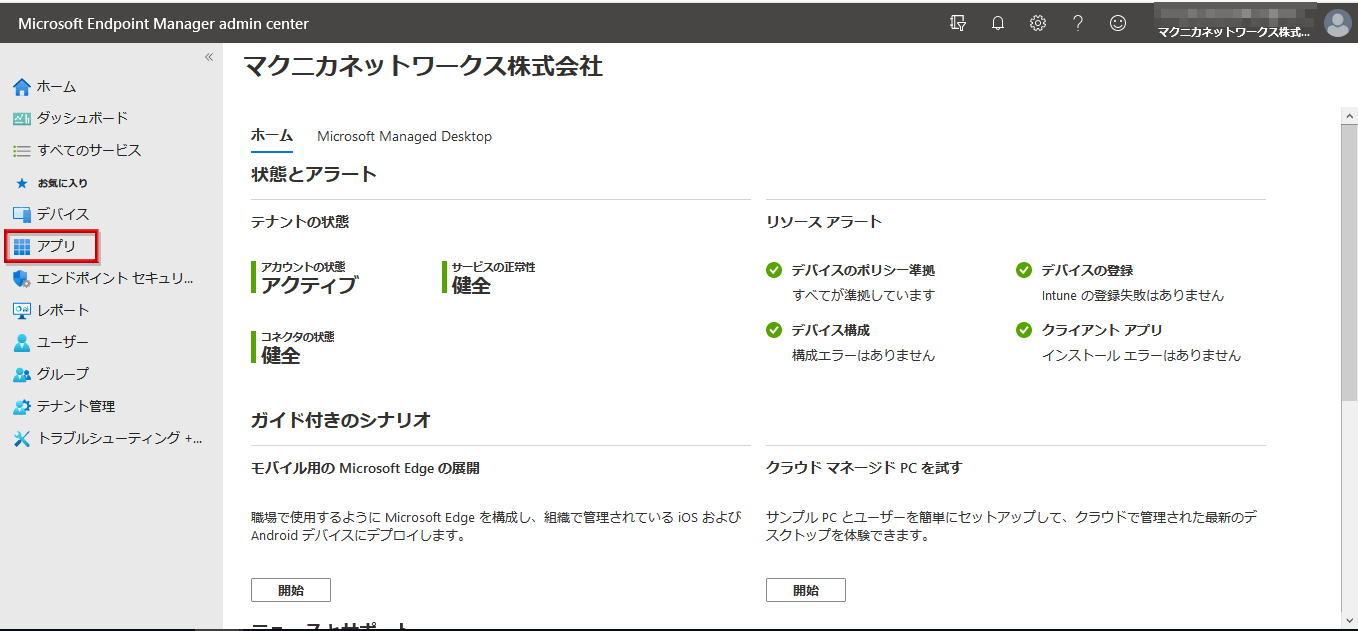
*In the above example, the management screen of Microsoft Endpoint Manager
- Select iOS/iPadOS by platform to enable Okta Mobile
- Click Add, select iOS Store App for app type, and click Select.
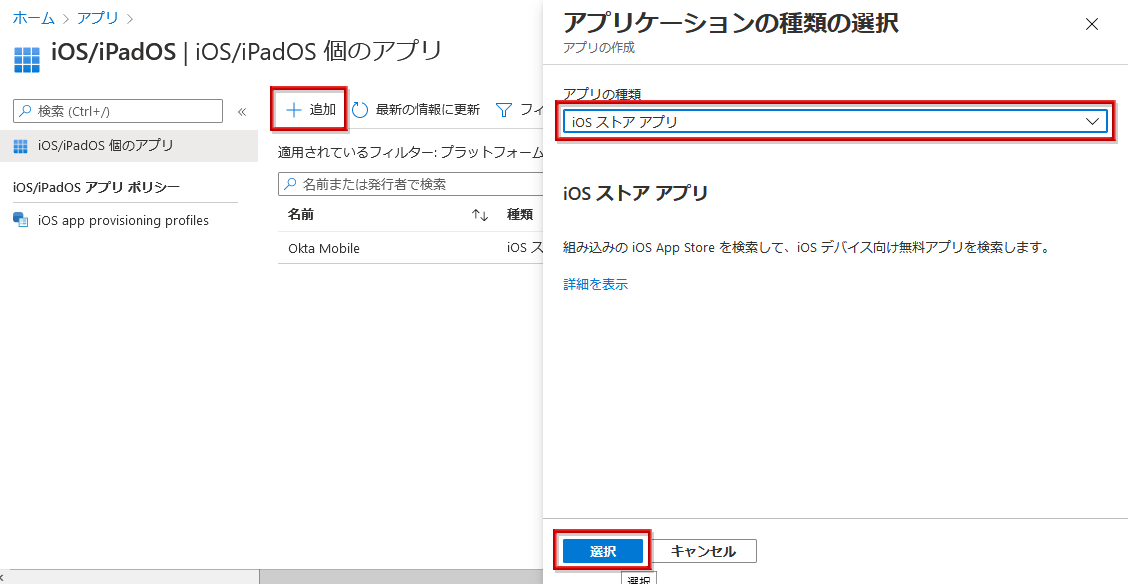
- On the Add app settings screen, click Search the app store.
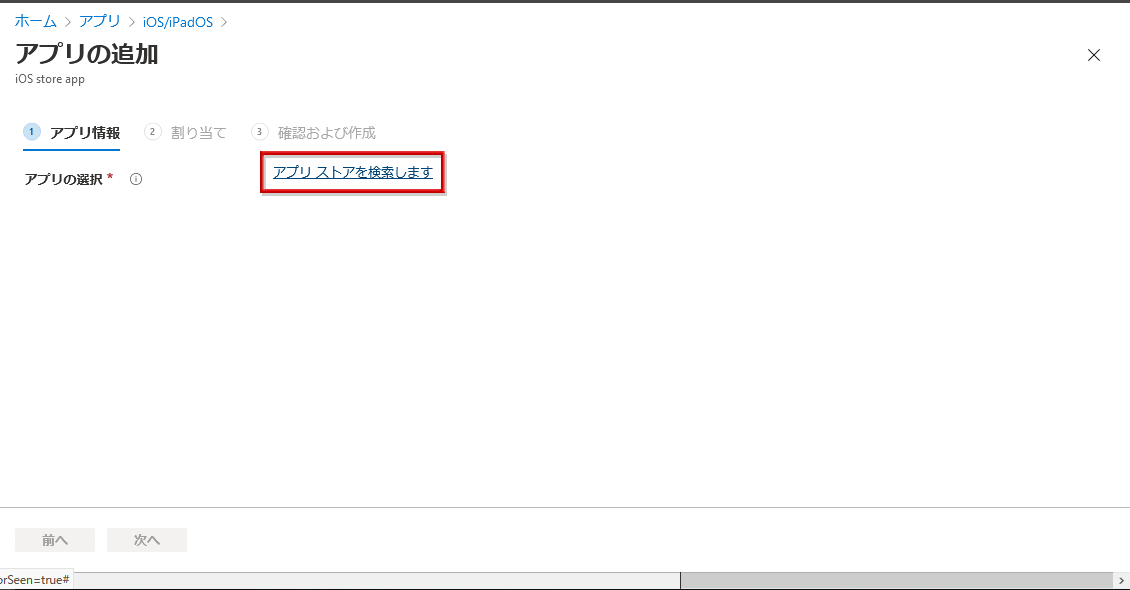
- Enter Okta Mobile in the search window, select Okta Mobile, and click Select

- Okta Mobile information will be reflected, so enter any name and click next
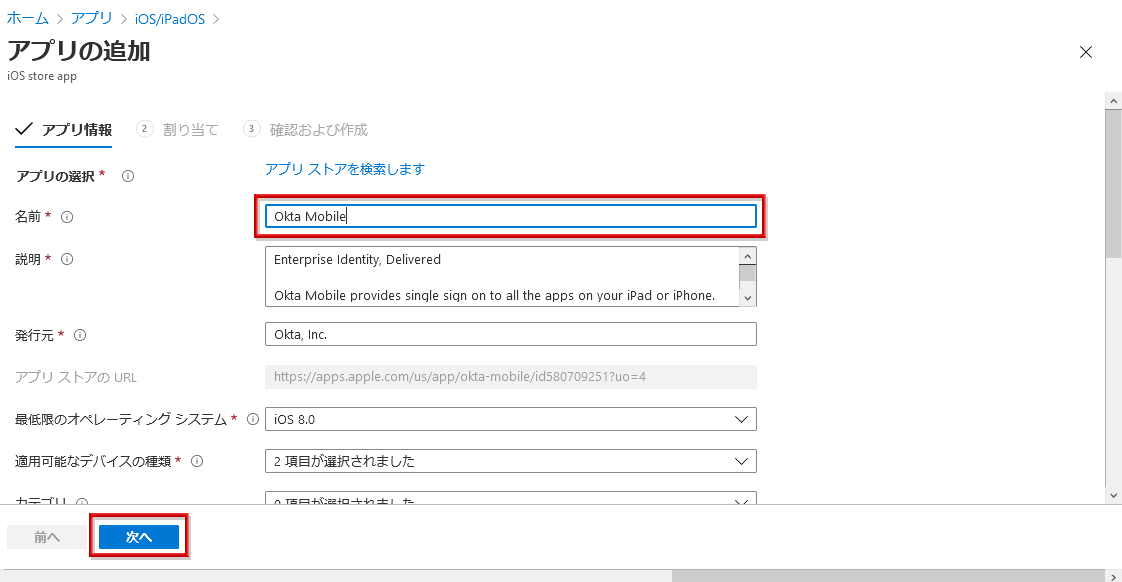
- After configuring the user groups that can use Okta Mobile, click Next
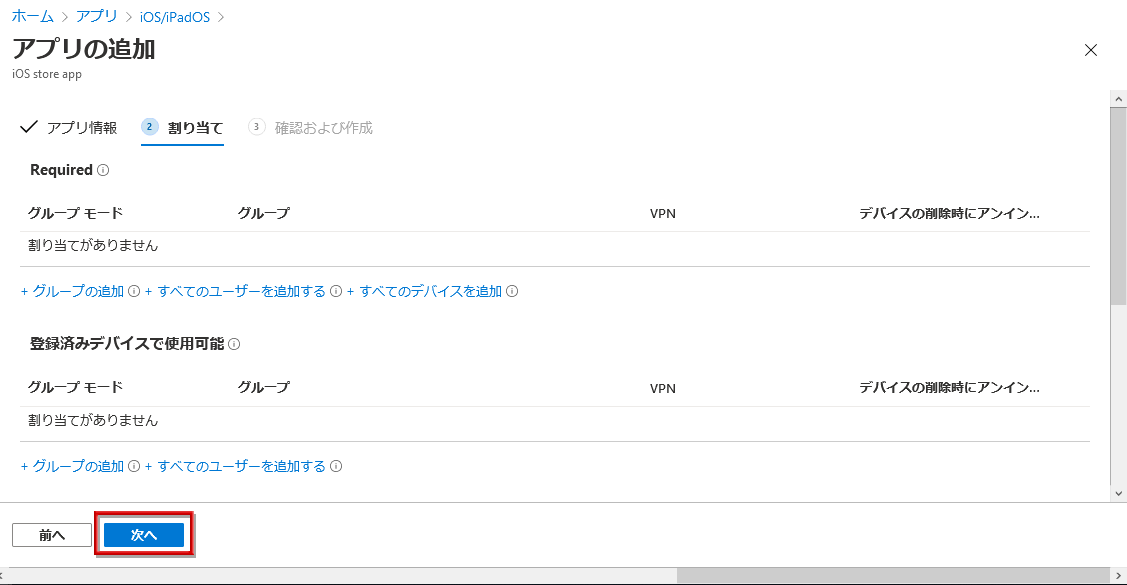
- After confirming the information of Okta Mobile to be added, click Create. Completion of adding the app (Okta Mobile) itself
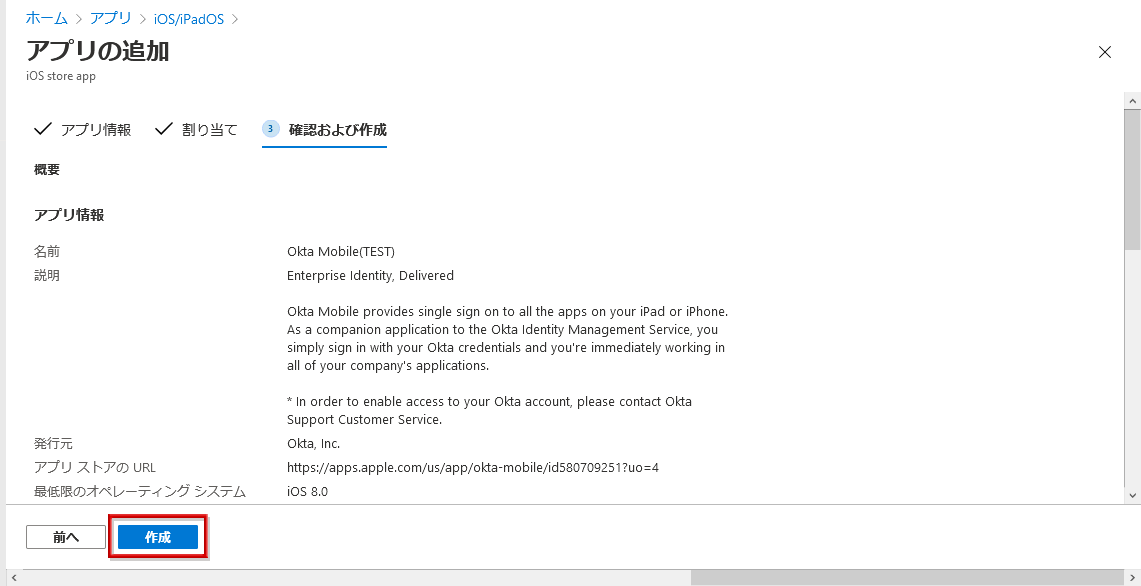
- In order to give the Okta side secret to the added Okta Mobile, select App configuration policy, click Add, Managed device
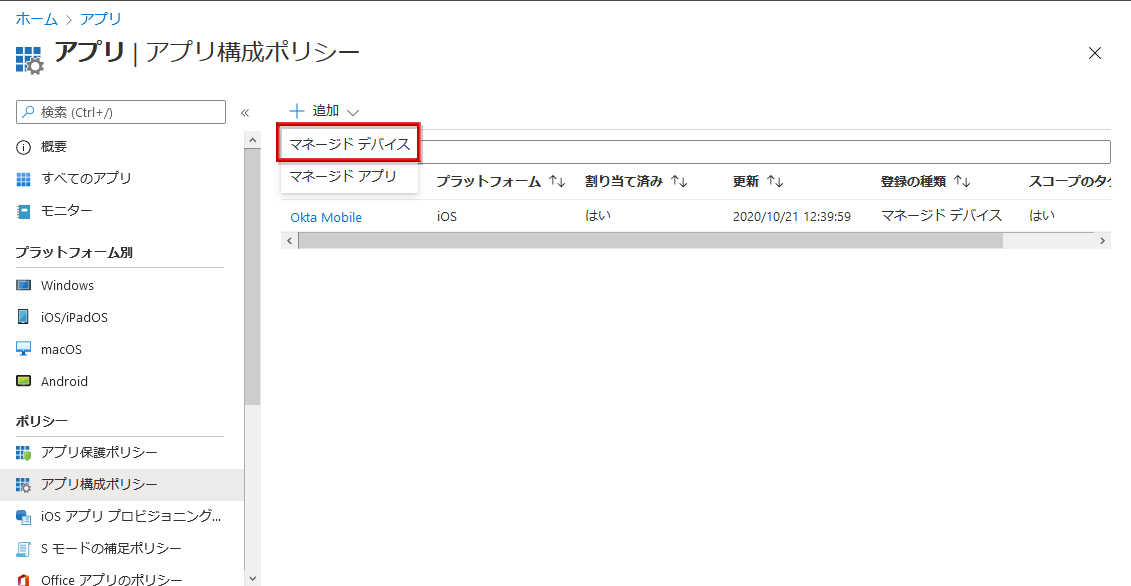
- The app configuration policy setting screen will be displayed. Select iOS/iPadOS with any name and platform, and click Select app.

- After selecting the Okta Mobile you added, click Next
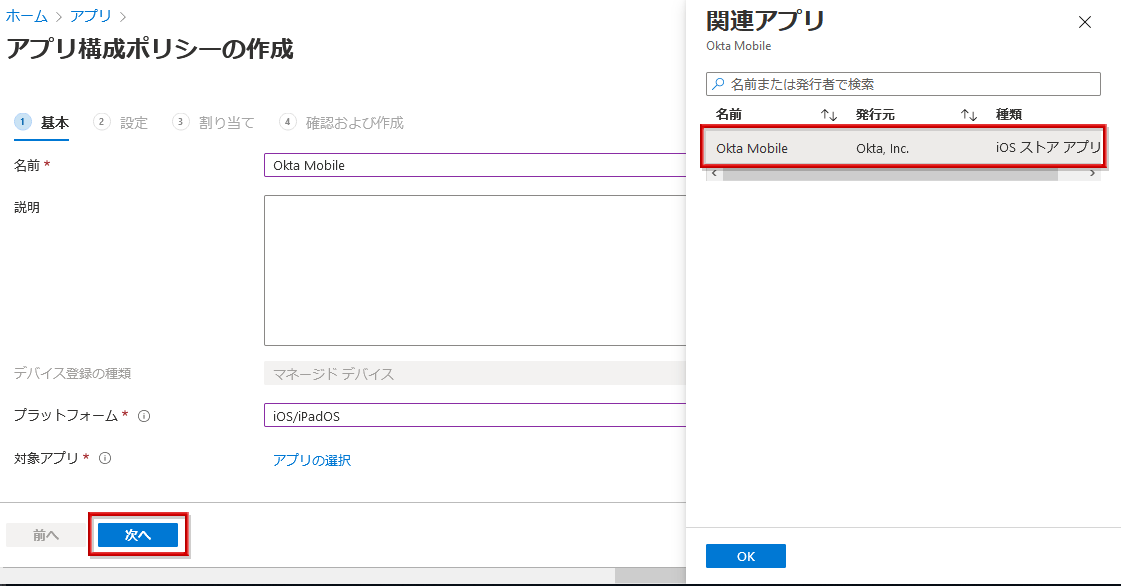
- Select Use Configuration Designer in Configuration settings format
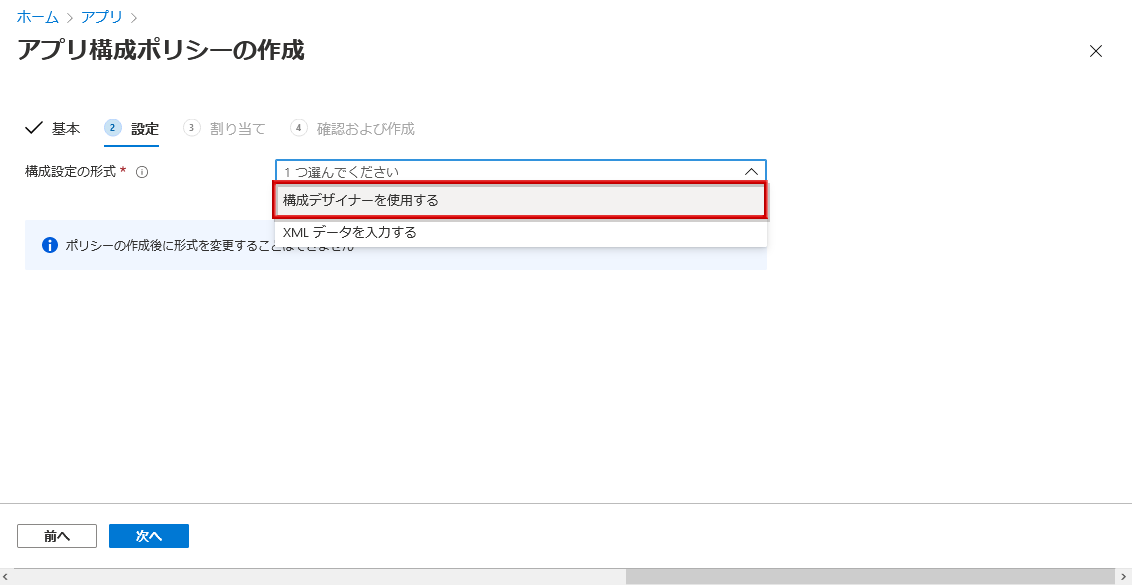
- Enter the following information in the configuration key and click Next
- Domain: Okta Tenant URL (e.g. https://demo.okta.com)
- managementHint: Secret Key that you copied in advance
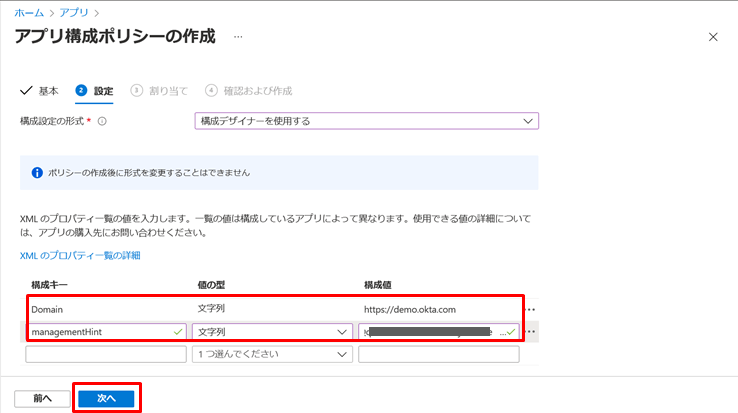
- In Assigned To, select any Assigned Target and click Next
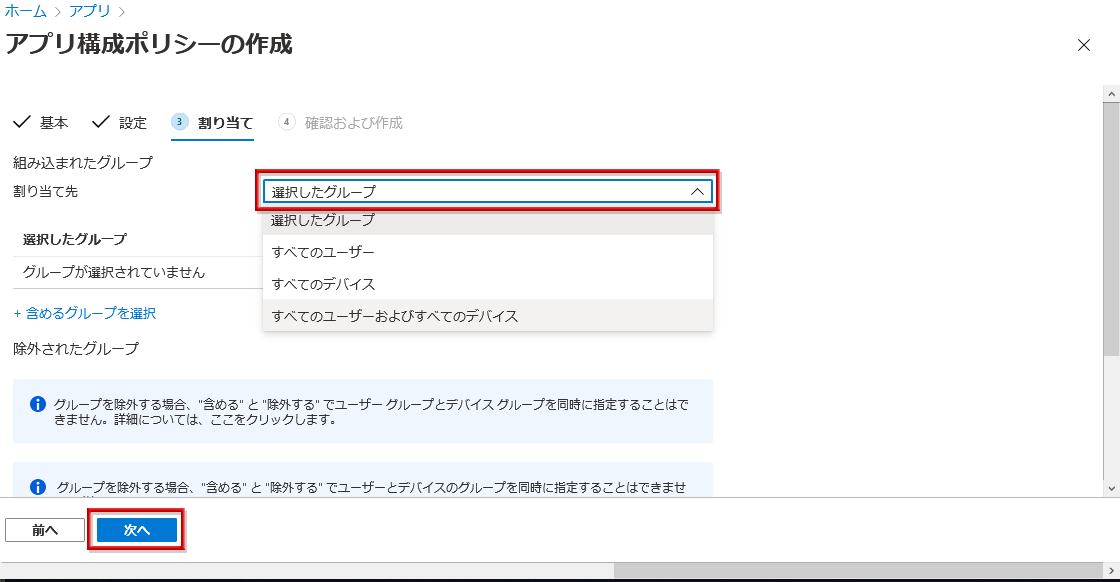
- Confirm the policy information to be added and click Create
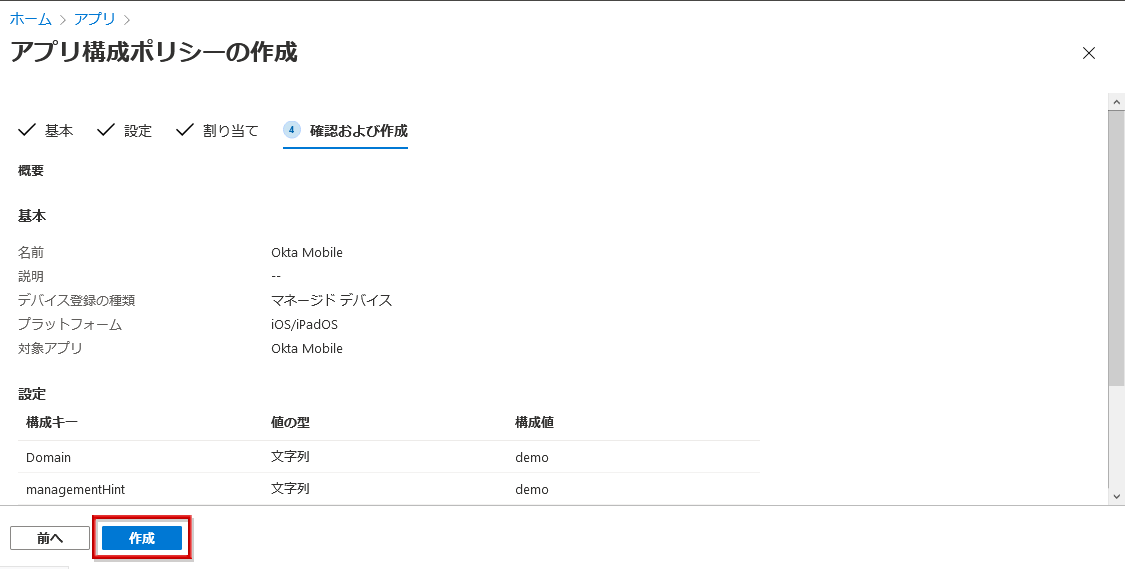
- If the added policy is displayed in the list, the setting on the MDM side is complete.
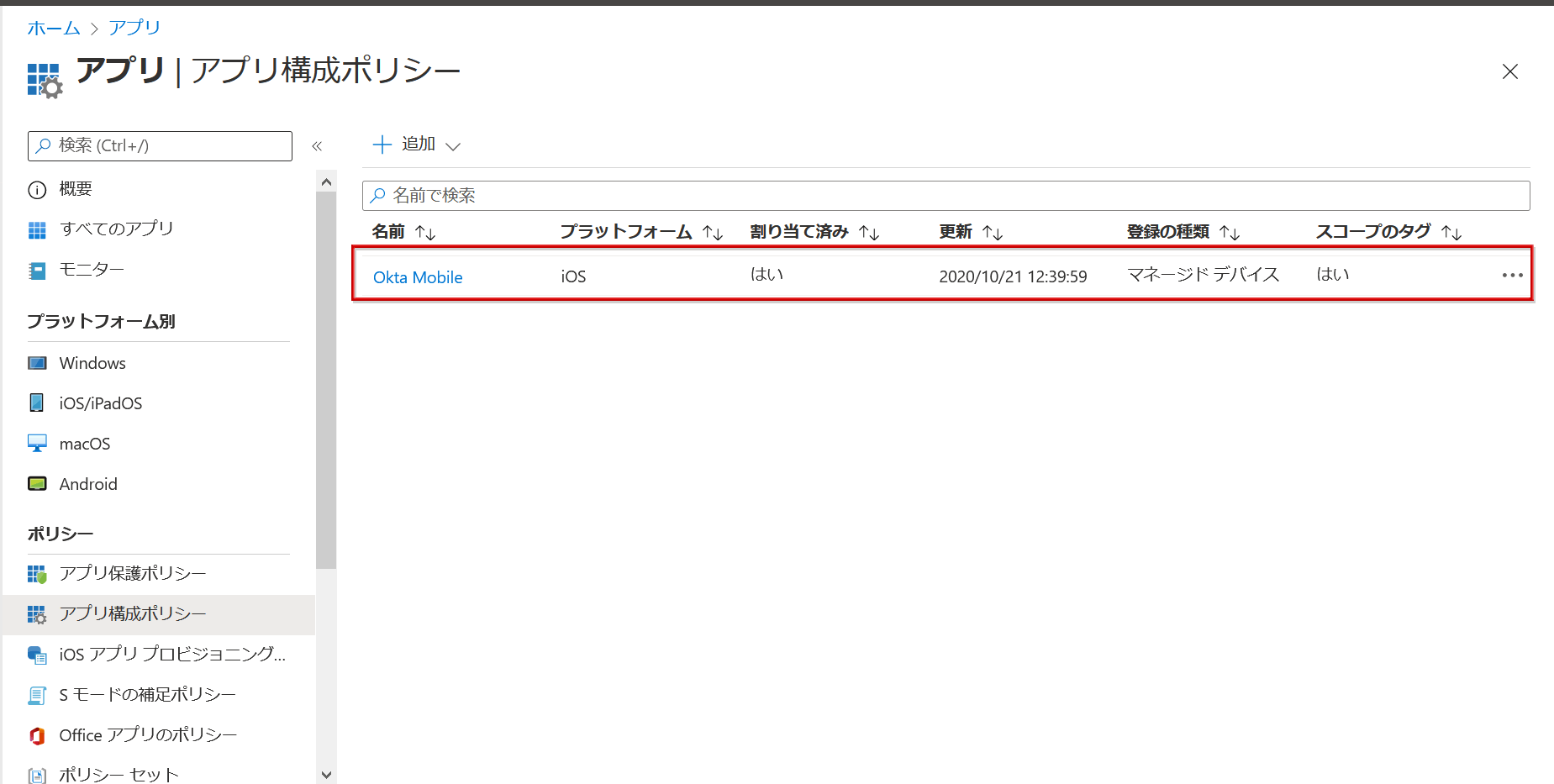
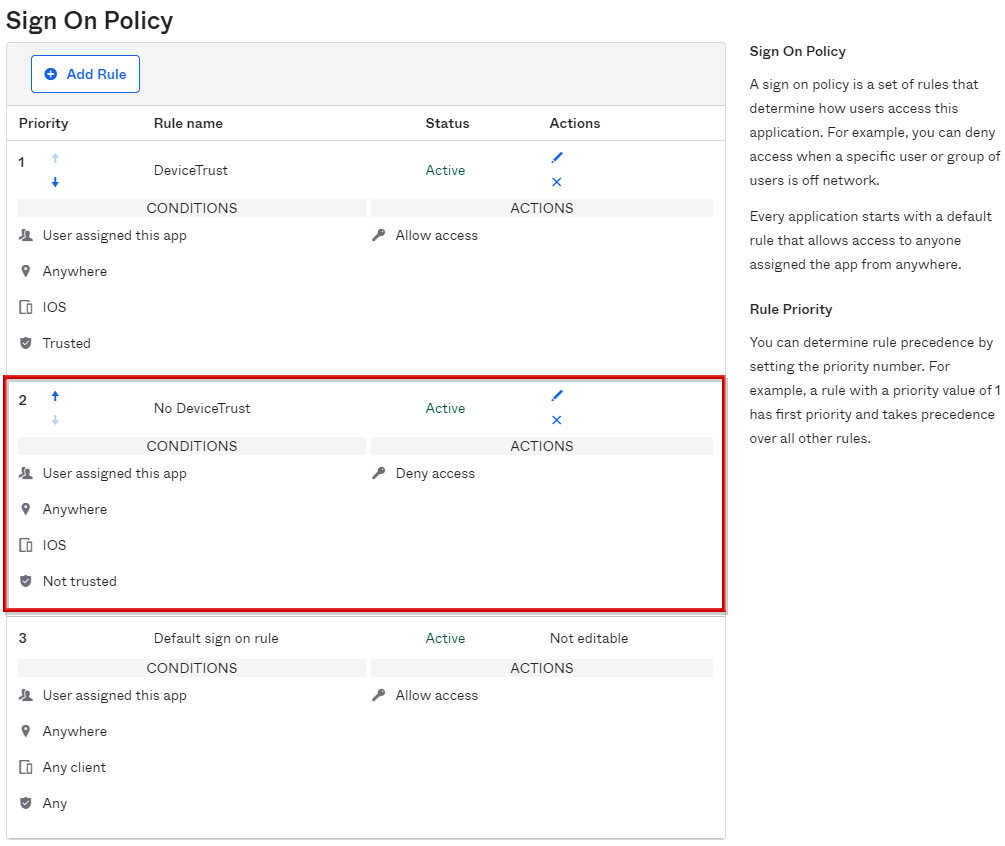
Set policy on Okta side
- Transition to Applications > Applications screen. Click any application to apply the Device Trust Policy
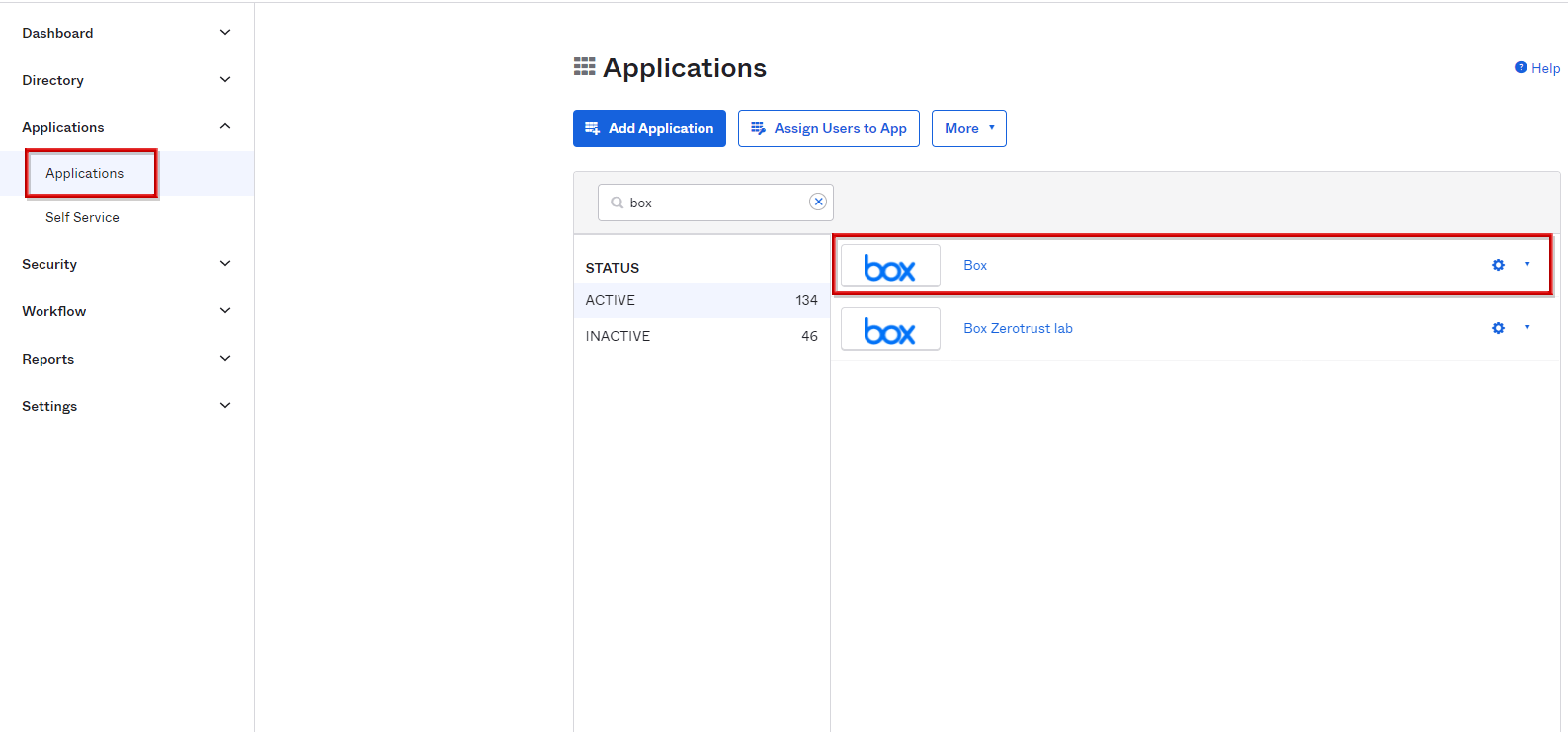
- Select the Sign On tab and go to the bottom of the page
- Click Add Rule in Sign On Policy
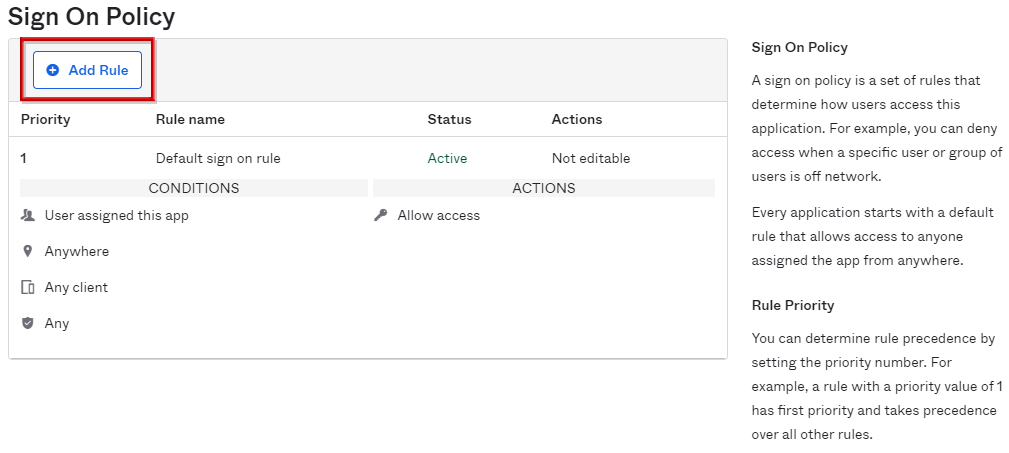
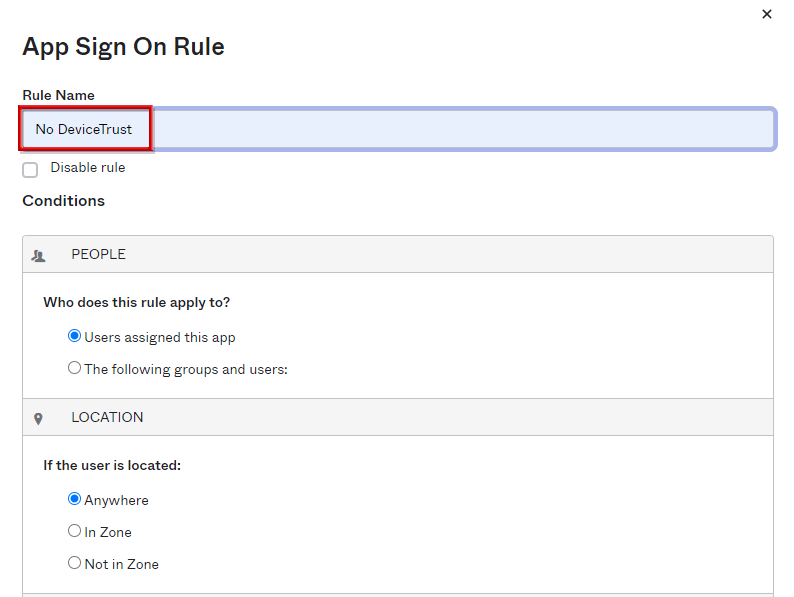
- Since the policy content setting screen is displayed, enter a name in Rule Name
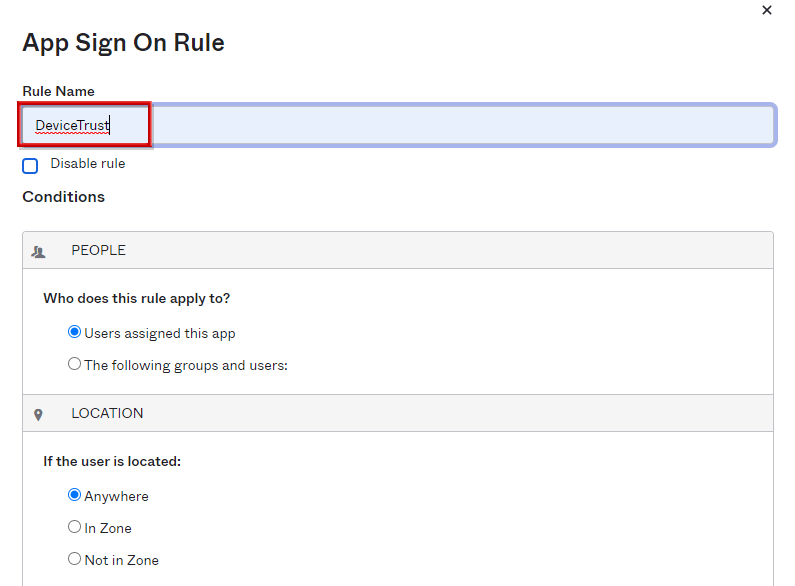
- Check only iOS in CLIENT, select the following items, and click SAVE
- DEVICE TRUST: Select Trusted
- ACTIONS ACCESS: Select Allowed
- Confirm that the policy has been added to the policy list
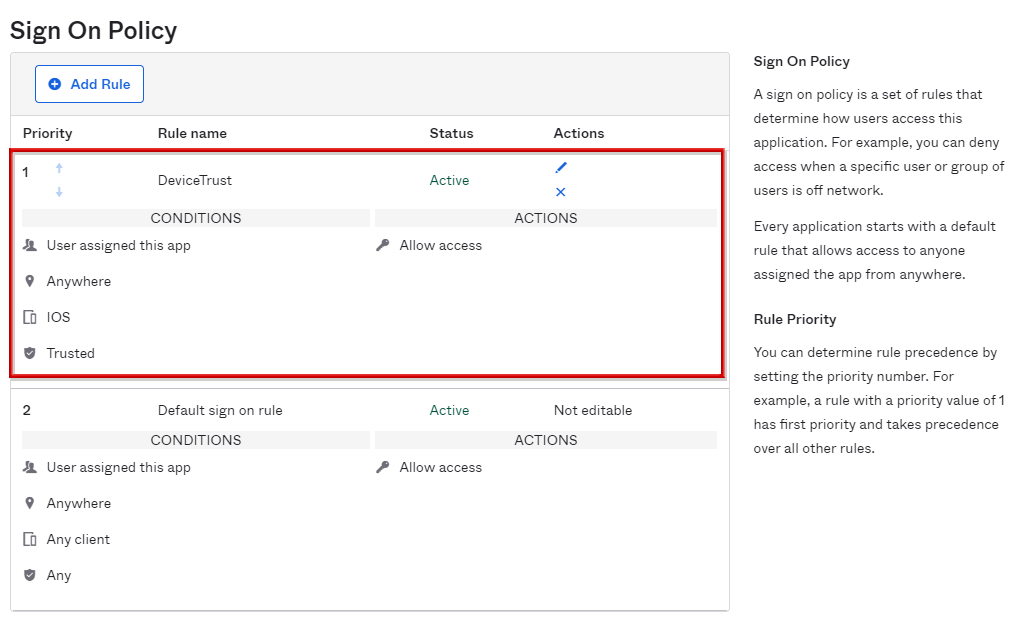
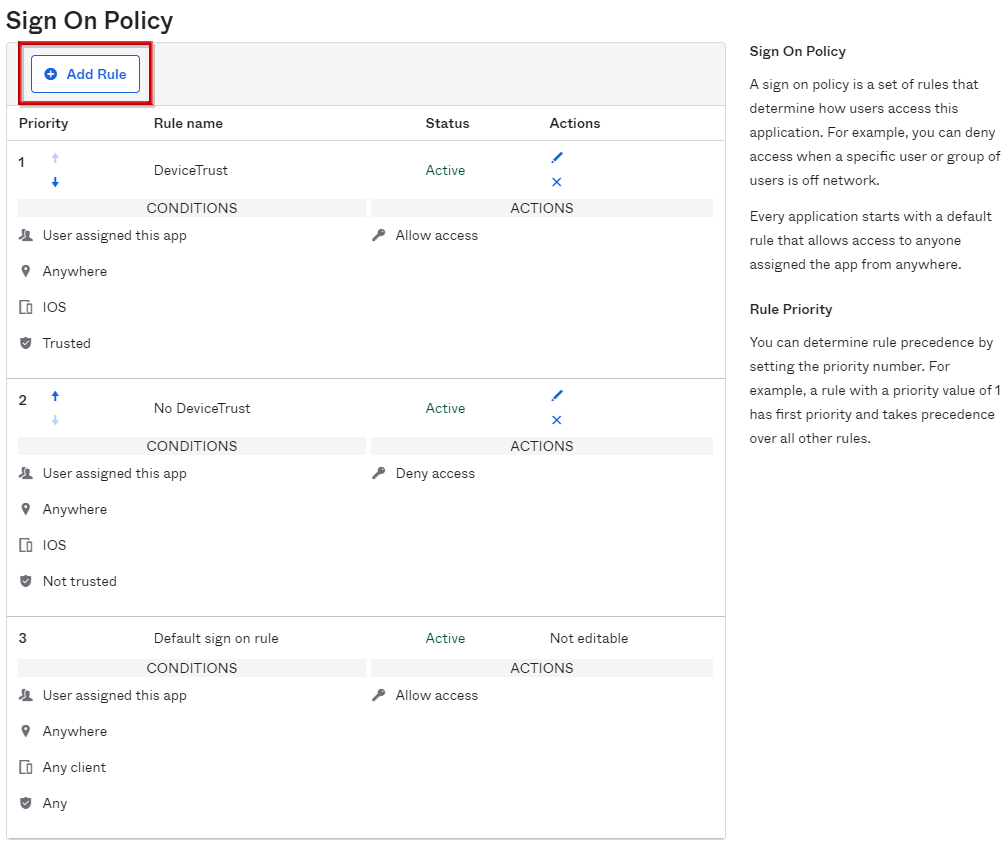
- Click Add Rule in Sign On Policy again
- Since the policy content setting screen is displayed, enter any name in Rule Name
- Check only iOS in CLIENT, select the following items, and click SAVE
- DEVICE TRUST: Select Trusted
- ACTIONS ACCESS: Select Allowed
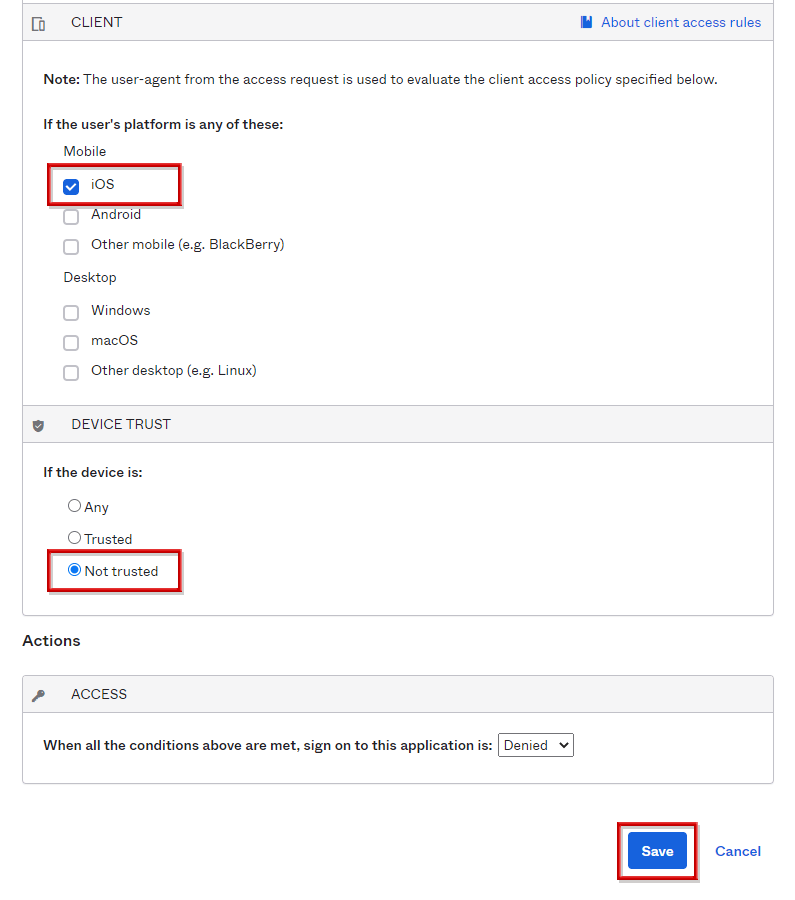
- Confirm that the corresponding policy has been added to the policy list, and complete the settings
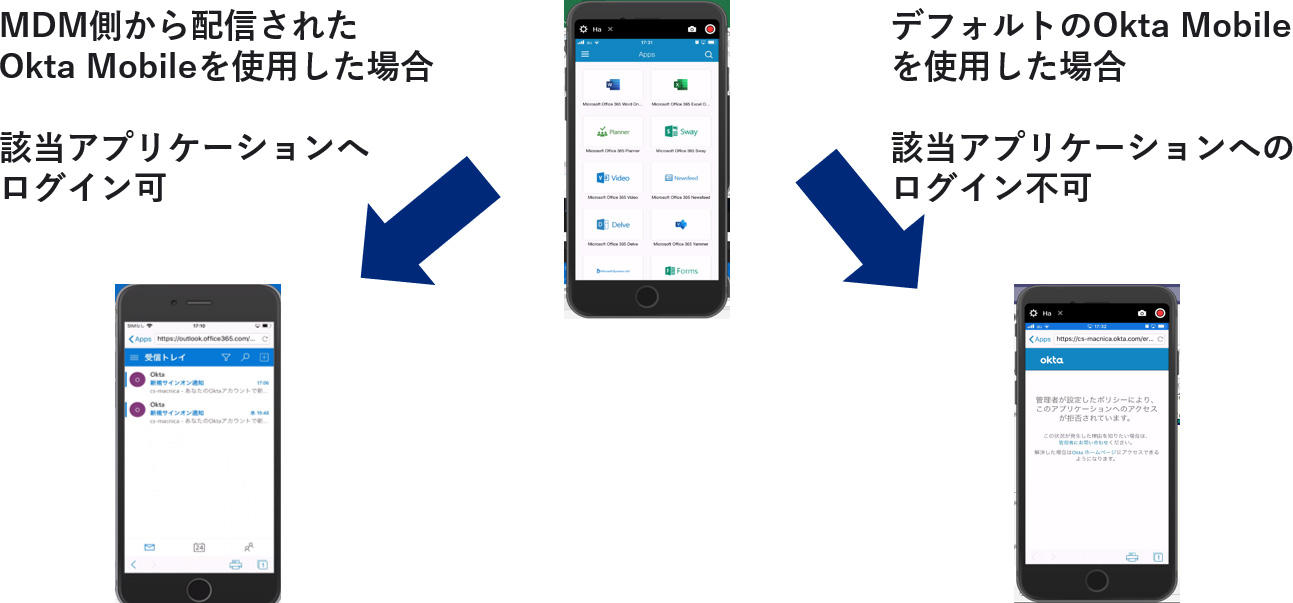
[Reference] Operation verification of device trust
Notes on iPadOS
Even if Device Trust is enabled for iOS devices, Device Trust is not enforced when accessing the app from Okta Mobile on iPad. As a result, apps can be accessed from Okta Mobile on unmanaged iPads.
This is because the Okta Mobile app recognizes iPad OS 13 or later as macOS instead of iOS. (Due to the specification change of iPad OS, the user agent became the same as Mac from iPad OS 13)
The corresponding method is as follows.
- Prevent access to apps from Okta Mobile on iPad
-
- By enabling "Do not display application icon in the Okta Mobile app" in Okta's app settings General, the app icon will not be displayed on Okta Mobile
- If this setting is performed, the app icon will not be displayed on Okta Mobile on all iPhone/iPad/Android devices, but in the case of these mobile devices, use SP-Initiated using a dedicated app.
- If you want to use the app from Okta Mobile on your iPad/Android device, do the following:
-
- If you are not using macOS, set macOS access to Denied in the Sign On Policy
- When using macOS, Device Trust is performed on macOS with high priority in Sign On Policy, and Not Trusted macOS is Denied.
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00