
Macnica Attack Surface Management
Macnica Attack Surface Management

GARTNER is a trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and other countries, and PEER INSIGHTS is a registered trademark of Gartner, Inc. and/or its affiliates and is used herein with permission. All rights reserved.
Gartner Peer Insights content constitutes the subjective opinions of individual end users based on their own experiences and does not represent the views of Gartner or its affiliates.
Gartner does not endorse any vendor, product or service depicted in Gartner Peer Insights, and Gartner disclaims all warranties, express or implied, with respect to the accuracy or completeness of this content, including any warranties of merchantability or fitness for a particular purpose.
Introduction company example

Trends in recent cybersecurity threats
Major incident factors in recent years
According to an investigation report by the National Police Agency, the top cause of incidents was publicly available assets.

Why are there so many security incidents now?
Attack techniques have changed in recent years and are extremely effective at exploiting weaknesses in enterprise security.

What is ASM (Attack Surface Management)?
What is ASM (Attack Surface Management)?
Attack Surface Management (ASM) is an initiative to identify and manage assets (Attack Surface) that can be used as attacks by cyber security threats.
Since the first step of ASM starts with an accurate grasp of assets, it is necessary to comprehensively grasp the company's assets.
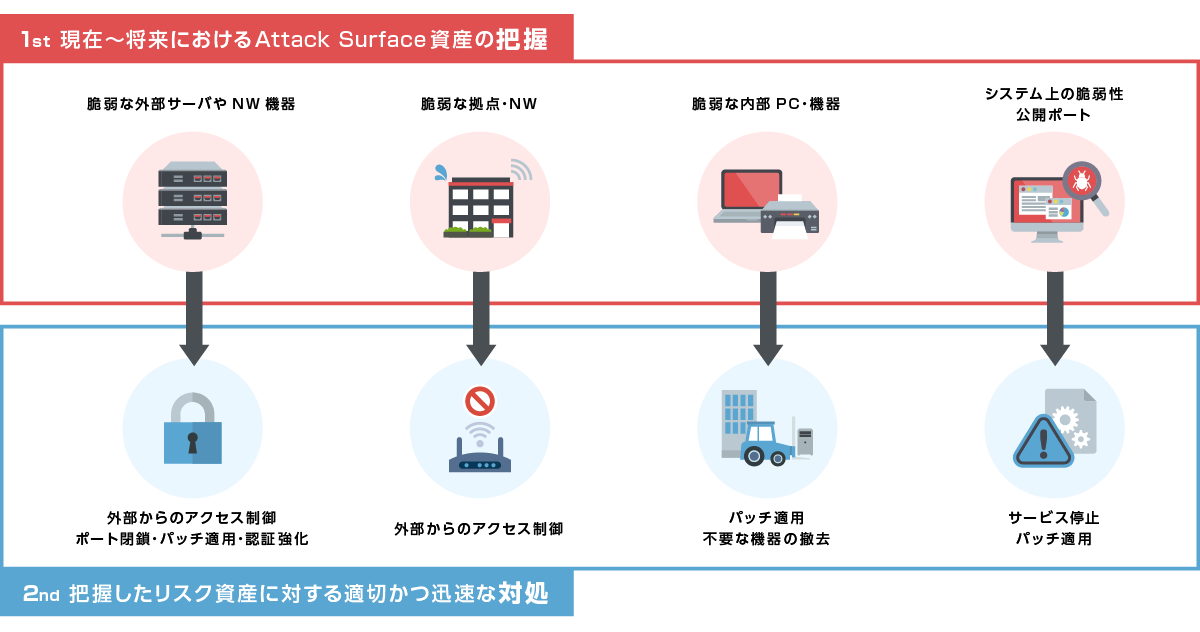
Key points that customers should do with ASM
The important points when implementing ASM are not only the current situation, but also the comprehensive "understanding" of assets that can respond to changes in the future, and the "priority" of countermeasures that take into account the urgency and importance of the identified asset risks. ranking”.
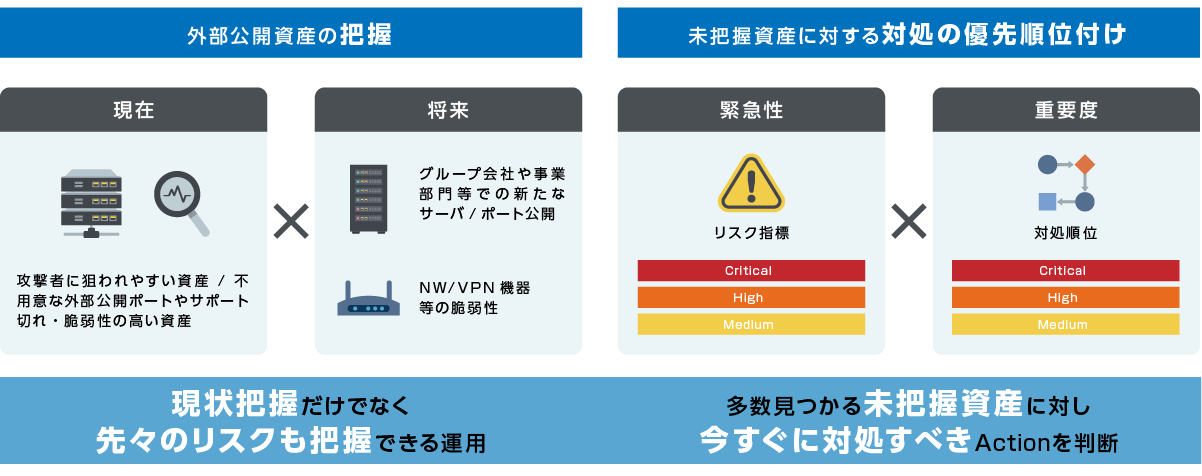
Macnica Attack Surface Management
Overall image
Macnica Attack Surface Management is a completely proprietary Macnica product that focuses on "understanding" the most important points and "prioritizing responses". Using the unique knowledge of our Security Research Center, we conduct a comprehensive investigation of assets, including those that are not yet known, and risk investigations that take into account the trends of attackers.

Macnica 's proud group of security experts - Security Research Center -
Macnica Attack Surface Management utilizes the knowledge of experts at the Security Research Center, who are well-versed in the trends and methods of cyber attacks both in Japan and overseas, to discover assets and assess threats from an attacker's perspective.

manager of centre
Kenzo Masamoto

Assistant Director
Yutaka Sejiyama

Chief
Ryo Shota

Chief
Hajime Yanagishita

chief
Hiroshi Takeuchi

chief
Takeshi Teshigahara

chief
Goya Yamazaki

Chairman
Yuji Kakeya
- international conference
- Black Hat USA Arsenal 2013 - 2016、2023
- HITCON CMT 2023
- Mandiant Cyber Defense Summit 2021
- VB2020 localhost
- CONFidence 2020
- HITCON Pacific 2018
- BSides Austin 2018
- Black Hat Asia Arsenal 2017、2024
- DEF CON 25 Demo Labs 2017
- Domestic conference
- Japan Security Analyst Conference 2018、2021、2022、2023、2024
- BSides Tokyo 2023
- (ISC)2 Japan Chapter Annual Conference 2022
- Sasakawa Peace Foundation Cyber Security Seminar 2019, 2021
- Information Security Workshop in Echigo Yuzawa 2021
- Shirahama Symposium 18th
- Supervised translation of books
- Incident Response 3rd Edition
- Other social activities
- Security Camp National Convention Instructor
- Government Security Advisor
- Research Committee Member, 21st Century Public Policy Institute, Japan Business Federation
- FY2021 Multinational Cyber Defense Competition
- Security Community Hamasec Operated
- threat research
Solution features and research methods
We utilize the unique knowledge of our Security Research Center experts to conduct accurate and comprehensive research.
We use the customer's head office domain and group company domains listed on the website as the initial values, check the Whois information, MX records, NS records, etc., and from there trace the connections between related domains and IP addresses to identify customer-related assets.
We can also identify assets, including domains, unauthorized servers, and overseas bases, that you yourself are not aware of.
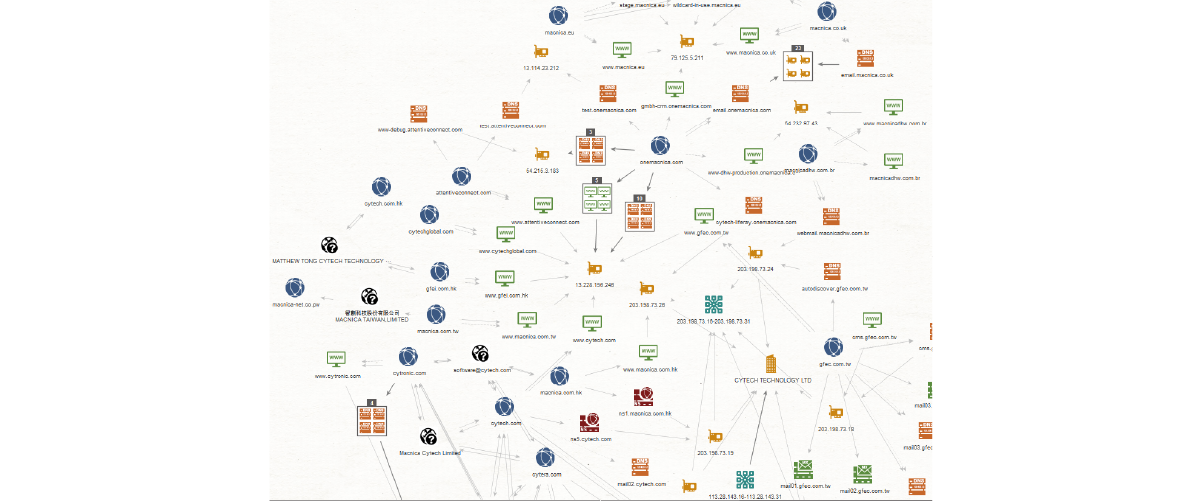
Survey image
Output sample - Status management and immediate notification -
The output is immediately usable and shows at a glance the discovered unknown assets, risk indicators, and priority of measures.
We provide both English and Japanese versions and recommended actions, so you can easily explain the situation to your overseas bases and group companies.

Portal function for administrators
This is a portal designed to reduce the operational burden of continuously managing assets available to the public.

feature
- View company-related assets and visualize connections
Only the results of scrutiny and triage of discovered public assets and risk information are displayed on the portal. You can check the connection between your own company's domains, subdomains, IP addresses, services, and other asset information and the asset information of each organization (overseas bases and group companies). You can assign any tag information to each asset and manage it.
- Progress management of risk management
The status of countermeasures against risks such as vulnerabilities and externally exposed ports can be visualized in an easy-to-understand manner. The countermeasure status is preset with the statuses required for ASM operation based on Macnica ASM's many years of experience, and the timeline for countermeasures against each risk can be recorded with simple operations.
- Vulnerability management
For vulnerabilities and risks that are disclosed daily, experts perform risk-based assessments based on attacker trends and the impact of exploitation, and after setting appropriate priorities, alerts are sent only for risks that require action. Notifications are sent immediately via email, and in parallel with this, risk information, recommended actions, and reference information (such as information from manufacturers) can also be viewed on the portal.
User company interviews
Arconics Co., Ltd.
SEGA SAMMY HOLDINGS CO., LTD.
Primary Distributor

NTT Docomo Business Inc.
reference
Difference from vulnerability diagnosis

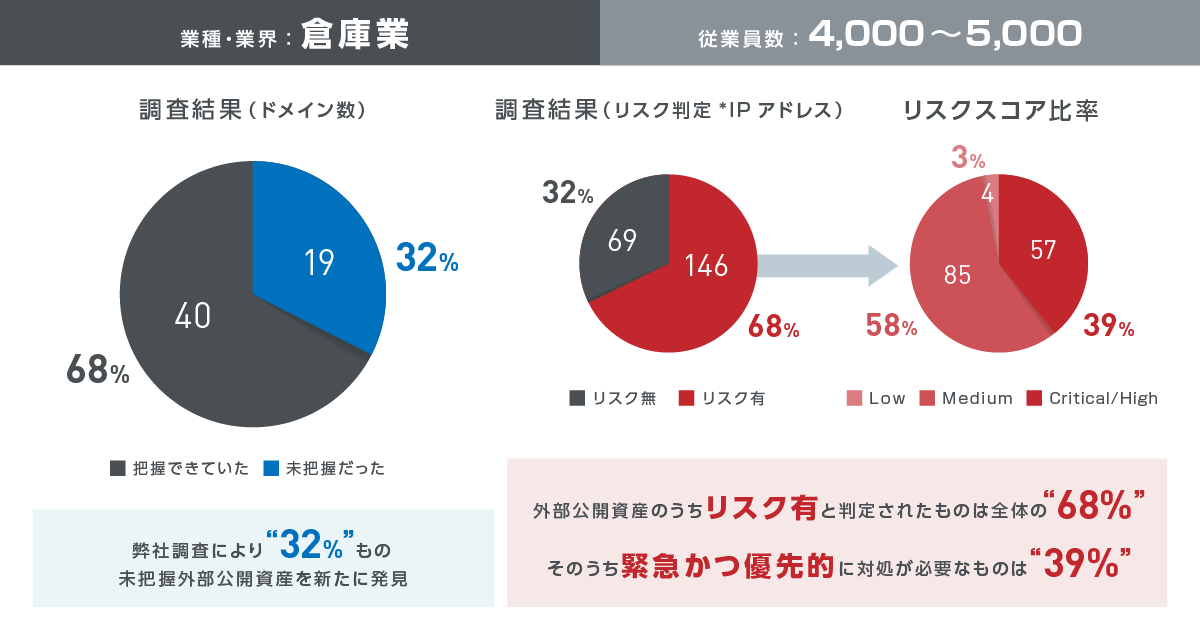
Customer survey case study of our solution implementation ①
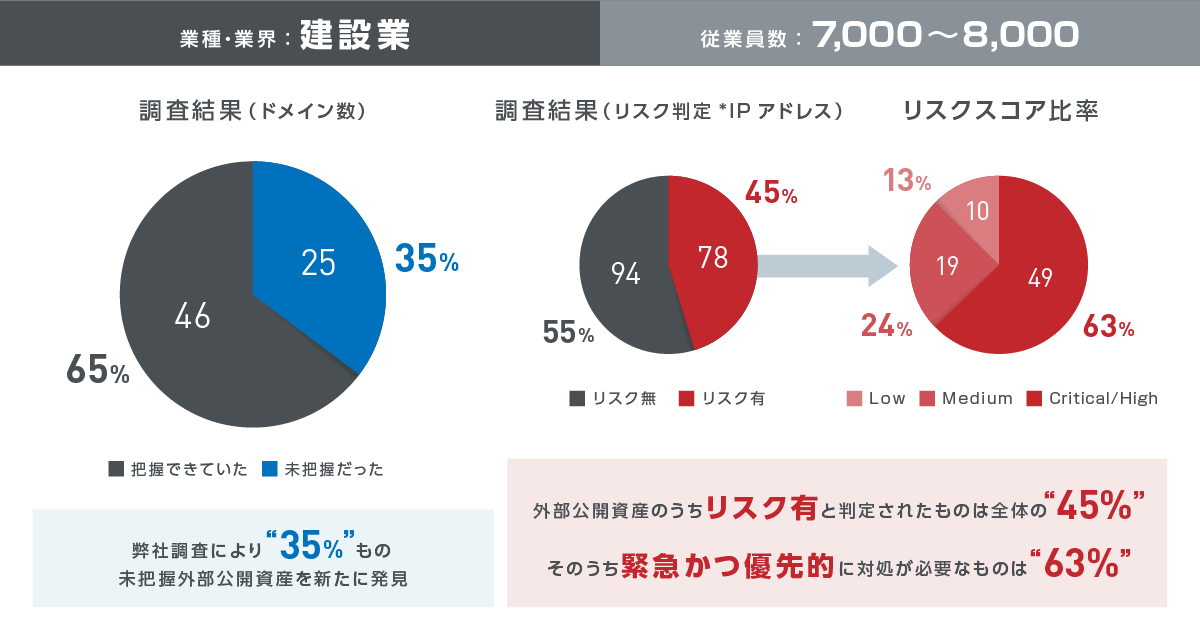
Customer survey case study of our solution implementation ②
Inquiry/Document request
Macnica Macnica ASM
- TEL:045-476-2010
- E-mail:sec-service@macnica.co.jp
Weekdays: 9:00-17:00
