
Island
アイランド
ブラウザで起きたことをすべてコントロールする(コントロール)
ブラウザがデバイスのセキュリティ状態やユーザアイデンティティ、すべてのWebアプリケーションに応じて、動作を変えることができたらどうでしょうか?また従来のVDI等で実現していたデータの持ち出しの制限をブラウザのみで実現できたらどうでしょうか?
エンタープライズブラウザ の登場によって、企業が思い描いたままにブラウザは制御できるようになっています。今までよりも安全に、しかもユーザ体験を損ねずにコントロールできます。
- 超詳細なポリシーを設定して、アプリやデータの使用方法を制御し、すべてを正しい場所に保ちます。
- 保護が必要なアプリケーションと不要なアプリケーションの間に、インテリジェントな境界線を作成して、すべてのユーザー、デバイス、アプリ、ネットワーク、場所、および資産にわたってDLPなどの保護が自然に適用されます。
ブラウザの活動をすべて確認する(可視性)
ブラウザはWebアプリケーション、つまりは重要なデータとユーザが密接に関わるポイントです。それにも関わらず、可視性が乏しい領域となっています。
エンタープライズブラウザは、Webプロキシなどのゲートウェイインフラストラクチャーに依存せず、それ自体でブラウザ内の活動を記録することができます。つまり、社内で開発した独自アプリケーション等を含め如何なるWebアプリケーションでも可視化可能です。
- すべてのブラウザの動作を記録:通信先の情報は重要です。しかし、ブラウザではもっと多くの活動が行われています。企業の重要なデータが含まれたWebサービス上で、重要なアクションのスクリーンショットを確認し、どこでクリックされたのかまで確認できたらどうでしょうか?
- 各アクションの文脈を理解して、どれを記録すべきか、どれをプライベートに保つかを知ることができます。
- カスタマイズ可能なダッシュボードですべてのアクティビティを表示し、SIEMや分析プラットフォームと統合して完全な可視化を実現します。
ブラウザ自体にセキュリティが組み込まれている(セキュリティ)
今日、SaaSの台頭により、ブラウザ経由で多数のWebアプリケーションへアクセスしています。しかし、現在主流のブラウザは、企業が利用するように設計されておらず、重要なデータへのアクセス保護や、マルウェアやフィッシングなど様々な脅威に対して対策ができていません。
ブラウザ自身が安全であれば、今までエージェントソフトウェアで実現していたセキュリティがブラウザのみで実現できます。
- ゼロトラストによる設計:ブラウザを介してアイデンティティ、デバイス、およびアプリケーションをリンクさせ、ゼロトラストを効果的にワーク環境に組み込みます。
- ブラウザに組み込まれた重要なセキュリティツール:ネイティブブラウザアイソレーション、自動的なフィッシング保護、ウェブフィルタリングなどが含まれます。
- Island Private Access:ブラウザを介してゼロトラストネットワークアクセスを拡張し、安全にプライベートアプリとネットワークに接続します。
今まで以上に速く、スムーズに働く(生産性)
エンタープライズブラウザのRPA(Robotic Process Automation)機能を使うことにより、Webアプリケーション上での自動化や組織独自のワークフローの強制などを実現できます。また、従業員が必要なWebアプリケーションのブックマークや拡張機能のインストールを管理することができるため、ログインした直後から業務を開始することができます。
- カスタムブラウザの自動化:ソースコードを一切触らずに、どんなウェブアプリも自分のワークフローに合わせることができます。
- 強力な生産性機能:スマートなクリップボードマネージャ、スクリーンキャプチャ、パーソナライズされたホーム画面のショートカットなど、作業をスムーズでシンプルにします。
- シングルサインオン:ユーザーは一度サインインするだけで、必要なすべてのアプリやリソースにアクセスできます。
仕事における理想的なエンドユーザ体験(ユーザ体験)
- すべてのための1つのブラウザ:デスクトップ、モバイル、管理デバイス、非管理デバイスに関係なく、どんなデバイスやOSに対してもIslandをインストールできます。
- Chromiumベース:通信の速度、レンダリング、拡張機能など、すべてがあなたが期待する通りに動作します。
- 完全な透明性を保つ:ステータスインジケーターや通知を介して、常にどのポリシーが有効かをユーザーに通知することができます。
アーキテクチャ
幅広いOSをサポート
PC端末、モバイル端末ともに豊富なOSをサポートします。
導入に必要なステップは、端末にブラウザをインストールするだけです。
※管理者権限は不要

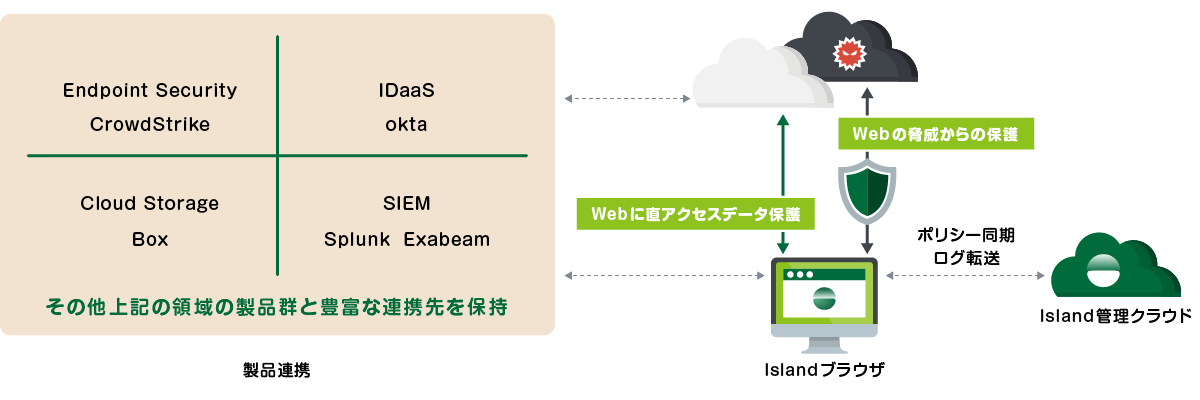
アーキテクチャ
エンタープライズブラウザは、シンプルなゼロトラストネットワークを提供します。ポリシーはクライアント端末に同期されているため、ブラウザは直接Webサーバにアクセスを行い、かつセキュリティを担保することができます。その他にも豊富な製品連携が用意されており、必要に応じたセキュリティ強化を実現できます。
- Endpoint Security:デバイスポスチャ機能を有しており、エンドポイントのソフトウェアの稼働状況によりアクセスをコントロールできます。
- IDaaS:SCIMによるユーザプロビジョニング、SSOによる認証を実現できます。
- Cloud Storage:ダウンロードしたファイルを強制的に指定したクラウドストレージへ保存させることが可能です。
- SIEM:ブラウザログは、SIEMなどのログサーバに転送することができます。
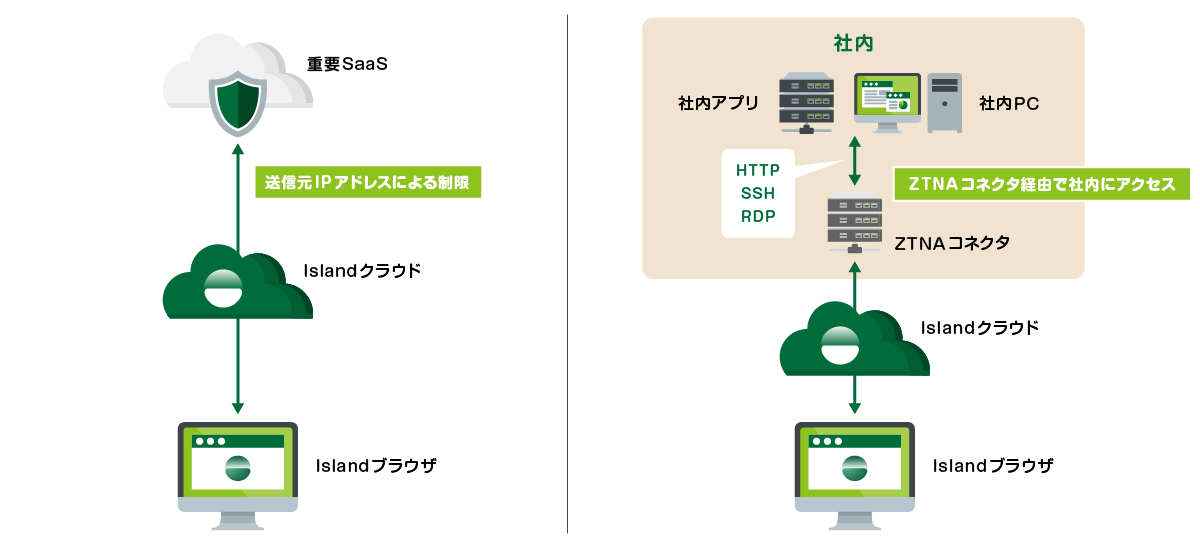
多彩なアクセス
エンタープライズブラウザは、用途に応じて多彩なアクセスを可能にします。
- Islandクラウドを経由することによる、SaaS側での送信元IPアドレスベースのアクセス制限
- ZTNAコネクタ経由での社内サーバへのアクセス
- ブラウザ内でのSSH/RDP接続
Islandの導入方法
Islandエンタープライズブラウザは従来のブラウザ同様に簡単に導入することができます。また、組織の要件に合わせて、すべての端末でエンタープライズブラウザのみを利用することも、消費者向けブラウザと併用し、共存させることも可能です。従来のブラウザとエンタープライズブラウザを共存させると、エンタープライズブラウザでの制御が失われるのでは?と考えるかもしれません。しかしそうではありません。ブラウザエンフォースメントにより、必要な時、必要な制御が提供されます。
3つの導入方法
1.非管理端末への導入
外部委託業者やBYOD端末などの個人端末でも、従業員のプライバシーを保護しながら、必要な場面でエンタープライズブラウザを利用できます。エージェントのインストールは不要で、簡単に導入でき、すぐに効果を発揮できます

管理されていないデバイスにIslandブラウザを導入し、完全かつ忠実にコントロールすることができます。デバイスポスチャー機能を利用して、プラットフォーム標準のコンプライアンスを確保し、監査とフォレンジックロギングで完全な可視性を確保します。 ラストマイルコントロールにより、データが承認された場所にのみ移動することを保証します。
- 非管理端末
- 遠隔地
- BPOs / コールセンター
- BYOD
- スケーラブルで効果的な展開モデル
- プラットフォームのフルサポートによりデバイスの互換性の確保
- コントラクターの行動を完全にコントロールし、可視化
- 組織とユーザのプライバシー
2.重要なSaaS・Webアプリを利用するユーザへの導入
SaaSやWebアプリの可視性と制御を高めることができます。通信の暗号化前後を監視できるブラウザならではの特権的なポジションを活用し、どのWebアプリケーションでも必要なセキュリティを効果的に実現します。特に表示データのマスキングやコピー&ペースト、印刷などラストマイルを効果的に管理・制御できる点はブラウザ特有のメリットと言えます。
導入想定ユーザ:コールセンター、重要なデータを取り扱う従業員、外部委託業者

重要なアプリやデータリポジトリへのアクセスを、Islandブラウザを通じて完全に制御できるようにします。セキュアなアクセスを必要とするユーザーグループにブラウザを導入し、ブラウザエンフォースメントでIslandを使用するよう強制します。 Islandは、クラウドやオンプレミスのアプリケーションを確実に保護し、データの流出を防止します。
- ハイリスクなユーザグループ
- コールセンター
- 遠隔地
- データがアプリケーションから離れないように閉ざされたループシステムを構築する
- 重要なアプリにはIslandを強制し、重要でないアプリには他のブラウザを使用する
- 特定のユーザーグループに統制された方法でIslandを展開する
3.全体への導入
エンタープライズブラウザは、通信の復号化などを必要とせず、自然な形で脆弱性、マルウェア、フィッシング、データ漏洩などの脅威から保護します。ブラウザの更新や拡張機能の管理、ブラウザに保存される資格情報の保護など、企業のセキュリティ課題や盲点を補完し、セキュリティを強化します。

Islandを組織全体の主要なデフォルトブラウザとして導入することで、機密データのコンプライアンスに基づいた使用、Webブラウジングに関する適切なガードレール、フィッシングや認証情報の取得に対するネイティブセキュリティを確保できます。Islandの生産性向上機能でエンドユーザーを喜ばせ、仕事の効率と満足度が向上します。
- フルプラットフォームサポート
- 全従業員への展開
- 管理及び非管理端末
- 組織のブラウザをアップグレードし、可視性とコントロール能力を得る
- 生産性向上機能を搭載したカスタマイズされたユーザ体験でエンドユーザーを喜ばせる
- Islandブラウザのログでコンプライアンスを示し、フォレンジック調査を強化する
- 既存のセキュリティ投資を最適化する
お問い合わせ・資料請求
株式会社マクニカ Island 担当
- TEL:045-476-2010
- E-mail:Island-sales-i@macnica.co.jp
平日 9:00~17:00