Imperva
インパーバ
Imperva WAF gateway(旧SecureSphere)
Webアプリケーションセキュリティ
Imperva WAF gatewayはWAF市場で圧倒的な実績と信頼性を誇り、金融、官公庁をはじめとした幅広い企業様に導入いただいております。また、昨今のクラウド化の高まりからImpervaもAWSやAzure環境でデプロイしオンプレミスと同等のセキュリティが担保できるアプライアンスをリリースしております。
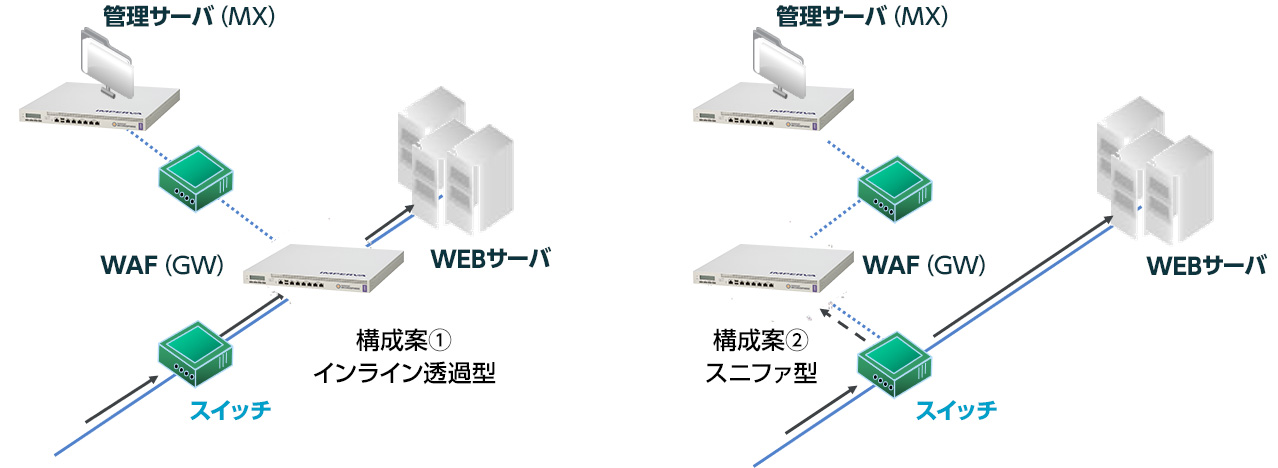
既存ネットワークに変更を加えない設置形態
- 透過ブリッジ (インライン)
- Fail Open / Close 対応
- スニッフィング (ノンインライン) 設置
- スイッチのミラーポートよりパケットコピー
多彩な攻撃防御手法
- シグネチャによるブラックリスト
- ADCから定期的 (平均1ヵ月に2度) に提供
- ブロック推奨シグネチャ、検知推奨シグネチャ
- ホワイトリスト (ダイナミック・プロファイリング機能)
- 通信内容からWeb 通信のホワイトリスト(プロファイル)を自動生成
- 相関攻撃検証
- 複数の異常から判断し複雑な攻撃を検知
- レピュテーション防御 (THREAT INTELLIGENCE 機能)
- 悪意ある送信元IP、匿名Proxy、フィッシングサイトURLを検知
WAFの運用例:セキュリティ強化
- 運用課題
- リスト型攻撃対策のために閾値ベースのカスタムポリシーを作成したが誤検知/誤遮断が多い
- 対策オプション
- 実態に合わせた閾値の調整(負荷高)
- Threat IntelligenceのBot検知を用いたポリシー&アラートの重みづけ(負荷低)
- Threat Intelligenceによる対策例:
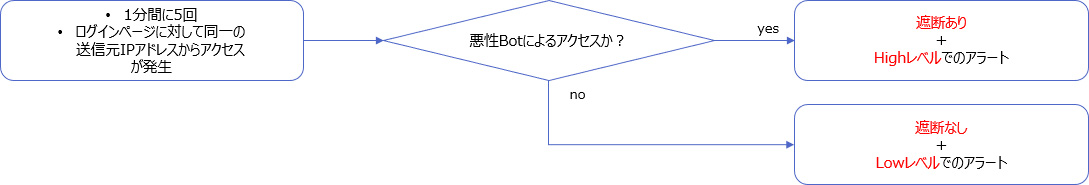
Threat Intelligenceの情報を条件としたカスタムポリシーの作成- 遮断の範囲を悪性度の高いアクセスのみへ限定するが、その他の不正な挙動の見られるアクセスについてもアラートをあげて記録を残す
1.「1分間に5回、ログインページに同一送信元IPアドレスからアクセス」→ 遮断はしないが、LowAlertでLogging
2.「1分間に5回、ログインページに同一送信元IPアドレスからアクセス」「悪性Botによるアクセス」 → Block + High AlertでLogging & ログ精査
- 遮断の範囲を悪性度の高いアクセスのみへ限定するが、その他の不正な挙動の見られるアクセスについてもアラートをあげて記録を残す
よくある質問
- 導入までのスケジュールを教えてください。
- 設定からサービスインまで1か月から2か月ほどです。チューニング含めた導入支援をご希望の場合は弊社よりご提供いたします。
- AWSやAzure環境でも利用可能でしょうか。
- はい、利用可能です。
お問い合わせ・資料請求
株式会社マクニカ Imperva 担当
- TEL:045-476-2010
- E-mail:imperva-info@macnica.co.jp
平日 9:00~17:00