
Imperva
Imperva
Ideal data security for next generation business
Introduction
While expectations are high for next-generation businesses that utilize data, the locations and formats of data are becoming fluid, and risk management and ensuring security have become issues for companies. This time, we will introduce points and solutions for maximizing data utilization while enduring management that is becoming more complex due to remote work and globalization, and strengthening governance.
table of contents
- Data Security Issues for Next Generation Business
- Organizing Data Security Requirements ~Responding to the Changing Business Environment~
- Ideal Data Security -Practice of Visualizing Data Assets-
1. Data security issues for next-generation business
Efforts to maximize organizational value through data utilization, such as rebuilding business models by promoting DX and expanding the scope of services by releasing APIs, are attracting attention. Data that companies used to use and disclose to the minimum necessary extent as "confidential information" has entered an era in which added value is created by expanding the scope of utilization, and attempts to create new profit models are spreading.
At the same time, changes in the business environment and companies themselves have created unprecedented data security risks. For example, many of you may be familiar with the following situation.
- Due to the spread of remote work due to the corona crisis, the use of the cloud is increasing, and the amount of work that is out of the reach of administrators is increasing.
- Human resources are becoming more diverse due to global expansion, and there are variations in employee values and compliance awareness.
- New services are increasingly being developed by business departments, and it is becoming difficult to centrally understand where and what data is due to the silo and complexity of related organizations.
While it is now possible to select a data management method according to the business situation, it has become difficult for the IT department to grasp the location and content of the data, and many companies have been working on it. employee training"" Formulation of data operation policy” risk management has reached its limits.
Examples of incidents of particular concern include:
▼Examples of Incidents of Concern
- Databases on the public cloud are unintentionally exposed to the public due to misconfiguration or inadequate governance
- Depending on the application, the database may be automatically replicated at startup, and because no one knew the existence of the replicated database, it was unprotected and suddenly subjected to a cyberattack.
- A large amount of confidential information is taken out due to internal fraud
- Because audit logs are simply accumulated and not properly analyzed, opportunities for early detection of unauthorized access are missed.
- The database structure is complicated, and it takes time to respond to incidents.
What is the “ideal form of data security” in the increasingly complex organization, human resources, and IT market? And how do we do that?
2. Organizing data security requirements - Responding to the changing business environment -
Conventional data security has been considered from the perspective of "how to control access subjects" on the premise that data storage locations and access sources are limited. However, from now on, it is necessary to actively increase liquidity to maximize the use of data, and the prerequisites have changed significantly.
So, let's start by sorting out the current issues and requirements for data security to realize next-generation businesses.
The current data security challenges can be summarized from four perspectives as follows.
For each challenge, list your data security requirements.
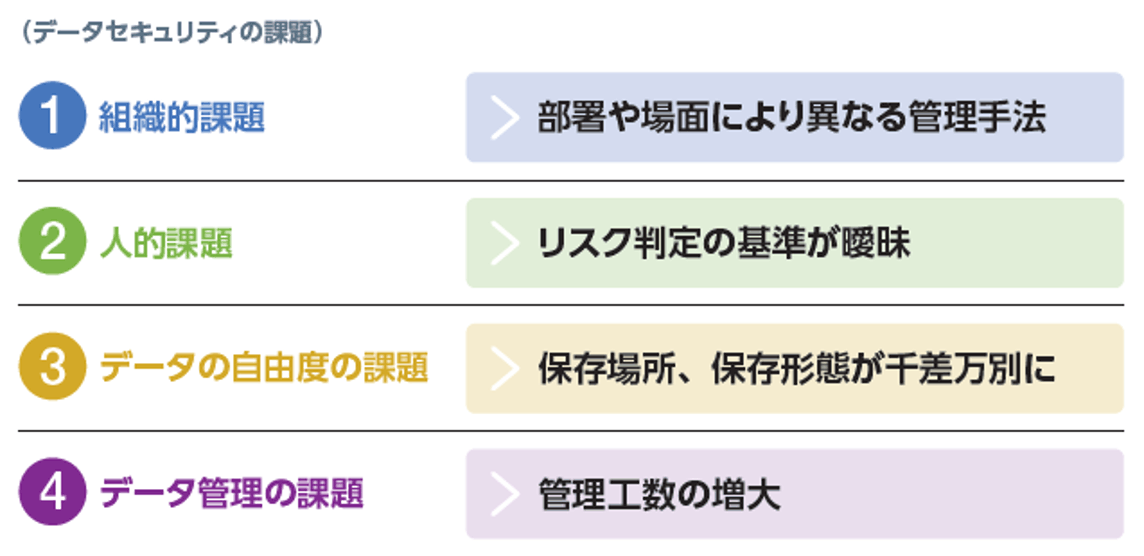
①Organizational issues >Management methods that differ depending on departments and situations
With the spread of remote work and the introduction of various business tools, the terminals, IP addresses, and applications that access data have become fluid, and it is necessary to deal with different management methods depending on the department and situation.
- Data security requirements
- 1-A: Corresponding to various logs of data audit and centrally visualizing them
- 1-B: Appropriate understanding of data access rights
(2) Human Issues > Standards for risk judgment are ambiguous
As globalization progresses, the positions and values of people involved in business are diversifying. There is an urgent need to establish unified monitoring rules according to data risks, without relying on personal judgment.
- Data security requirements
- 2-A: Uniform monitoring rules can be set according to data risks
(3) Issues with data flexibility > Storage locations and storage formats vary widely
Public cloud and DBaaS (Database as a Service) have become widespread, enabling flexible data management according to business conditions, while data storage locations and storage formats are diversifying. In addition to formatted structured data such as databases, unstructured data such as files also need to be considered.
- Data security requirements
- 3-A: Ability to monitor stored data by supporting abundant data storage locations
- 3-B: Identify data content and determine risk
④ Data management issues >Increase in management man-hours
Data storage locations are dispersed, data volumes increase, and the required analysis is becoming more sophisticated. The reality is that it is extremely difficult to do everything manually.
- Data security requirements
- 4-A: AI analysis can discover "situations that may cause fraud" without man-hours

A total of 4 challenges and 6 requirements were highlighted.
A security system that can meet all of these requirements can be said to be the "ideal form of data security" for next-generation businesses.
3. What is ideal data security? - Practicing visualization of data assets -
Next, let's think about "ideal data security" that satisfies these requirements. Here, we introduce the necessary security functions along the steps of actual data management. Get an overview of the features and capabilities that address each requirement.
\What security functions are necessary to visualize data assets and implement countermeasures? /
\ What is a “data security solution for next-generation business” that realizes comprehensive data security? /
*You can read the full text by downloading the white paper.
Inquiry/Document request
In charge of Macnica Imperva Co., Ltd.
- TEL:045-476-2010
- E-mail:imperva-info@macnica.co.jp
Weekdays: 9:00-17:00