product
- What you can do with CrowdStrike
- CrowdStrike Modules Falcon
- Falcon Prevent(NGAV)
- Falcon Insight(EDR)
- Falcon OverWatch (Threat Hunting)
- Falcon Discover (IT Asset Management)
- Falcon Spotlight (vulnerability management)
- Falcon Adversary Intelligence
- Falcon Identity Threat Protection/Detection
- Falcon Cloud Security(CNAPP)
- Falcon Surface(EASM)
- Falcon Shield(SSPM)
- Falcon Next-Gen SIEM
service
Application for evaluation machine
- FAQ

CrowdStrike
CrowdStrike
The latest endpoint security measures to overcome evolving cyber attacks

Use CrowdStrike products to counter threats that cannot be detected and protected by EDR alone.
The importance of endpoint security measures has come to be emphasized, and many companies have already begun to introduce next-generation antivirus (NGAV) and EDR (Endpoint Detection and Response) products. Cyberattack techniques and methods continue to evolve on a daily basis, and many security personnel are concerned about whether they can truly protect their company's environment. Macnica is therefore holding a seminar titled "Evolving Cyberattacks and the Key to Selecting Endpoint Security." The latest threats and countermeasures will be explained through six sessions, including talks by Mr. Nawa of the Cyber Defense Institute and Mr. Ueno of Tricorder, who are well versed in the latest security trends and efforts, as well as by companies that have introduced CrowdStrike products recommended by Macnica.
Six traditional security controls that have lost their effectiveness

Mr. Toshio Nawa (affiliated with Cyber Defense Institute, Inc.), who was the first to take the stage, explained the methods and background of typical cyber attack cases in recent years that had a serious impact on business activities. He then points out that there are six traditional security controls that are no longer effective.
First, we emphasize that human resource security management measures should never be implemented. For example, the mental pressure given to ``lower the open rate'' during ``(1) Targeted Attack Email Training'' may actually become a breeding ground for accident concealment. What Mr. Nawa suggests is to conduct phishing awareness training that uses incentives to create a foundation for increased reporting, and then repeat the PDCA cycle of monitoring, identifying, evaluating, and responding to risks. In these activities, the use of EDR and other technologies that enable quick responses will be effective.
The next option is ``(2) Slide-style e-learning.'' Mr. Nawa says that since ``imagination'' is more important than ``knowledge'' in the practice of risk management, basic training in creativity through storytelling should be provided.
He also revealed that there are organizations that still believe in the effectiveness of ``(3) MAC address filtering for Wi-Fi connections,'' even though MAC addresses can be easily spoofed.
Regarding ``(4) Appointment of CISO through internal personnel transfer,'' issues such as lack of knowledge, skills, and experience, internal politics, promotion activities that depend on authority, and bias influenced by specific areas within the company are cited, and countermeasures are being taken. We recommend that you consider appointing someone from outside.
In addition, ``⑤ Memory-based password changes'' to avoid the risk of resetting passwords that were leaked in the past, and ``⑥ Security check sheets for outsourced companies'' to prevent false reports. It is cited as a management measure that has lost its meaning. Finally, Mr. Nawa strongly emphasized the need for human resources with the same authority as Member of the Board responsible for cybersecurity leadership.

Cybersecurity from an attacker’s perspective: What is the optimal defense strategy to minimize damage?

The optimal defense strategy in cybersecurity becomes more effective by incorporating the attacker's perspective. Therefore, Tricoder Co., Ltd. provides "penetration testing" as a service that actually infiltrates companies.
Representative Board Director Nobuaki Ueno, who spoke at the seminar, explained the recent trends by saying, ``attackers have clear intentions and objectives, and are sometimes organized or nationally motivated.'' He also points out that attacks are carried out using ``social engineering'' based on preliminary research, and that the attack surface has expanded as a result of advances in remote work and use of the cloud.
Therefore, what is required of the defender is to once again check why the various measures are being taken, and then to ask whether the measures being implemented for the things that should be protected are ``working comprehensively.'' Just make sure. Penetration testing can measure that.
After conducting tests, it is important to address issues that have come to light, such as system vulnerabilities and operational vulnerabilities (reusing passwords, obsolete procedures, etc.). Furthermore, when evaluating cyber resilience capabilities, it is important to quickly discover attacks and aim to minimize damage by responding before major damage occurs, assuming that an intrusion, infection, or ID leak has already occurred. .
What you need to be aware of is that actual threats are more complex and sophisticated than anticipated threats, and that threats are constantly evolving, so you need to regularly review and update your countermeasures. Therefore, penetration testing should be conducted regularly. However, testing requires specialized skills, and it is not easy to conduct it in-house because objectivity may be compromised and potential problems may be overlooked.
Therefore, Mr. Ueno proposes the option of outsourcing, listing the advantages and disadvantages (Figure 1). Among the strengths, ``objectivity and fair evaluations that are not influenced by internal politics or bias'' are values that should be especially noted in cases where management does not understand the need for security measures even after appealing to them.

Specific architecture centered on EDR and CrowdStrike

Kenta Konnouchi of the First Sales Department, Security Division 1, Macnica Networks Company, says that EDR should be positioned at the heart of security measures. The reason is that many attacks occur at endpoints, and the information essential for investigating the attacker's trail can be obtained from the endpoint. However, there are some areas that EDR cannot collect, so he says it is important to collect the missing information from other solutions and compare it to improve the accuracy of the information and visualize the overall picture of the incident.
Of the many EDR products available, Macnica recommends CrowdStrike products. There are three main reasons for this. The first is their "high detection and investigation capabilities," which have been highly praised in many external surveys. Konno explains, "We are so confident in them that we want you to check them out with a PoC beforehand."
The second point is the use of threat intelligence. CrowdStrike 's business began with the provision of threat intelligence, and the company has a wealth of information on threat actors around the world. The third point is that it is a solution that can be smoothly expanded to include EDR and other related fields with "one console and one agent."
CrowdStrike has a product lineup that can handle not only EDR but also areas such as AD and cloud, and in addition to being able to support peripheral areas with the same product, we also offer collaboration with a wide range of third-party products in addition to our own solutions. Its strength is that it is designed with this in mind, so it can be used to help each organization realize its ideal state.
Macnica supports the creation of optimal environments and operational operations by combining products such as VectraAI for NDR (Network Detection and Response), Okta for IDaaS (ID as a Service), Netskope for Security Service Edge, and Splunk and Exabeam for SIEM (Security Information and Event Management), as well as its own integrated SOC (Security Operation Center) service.
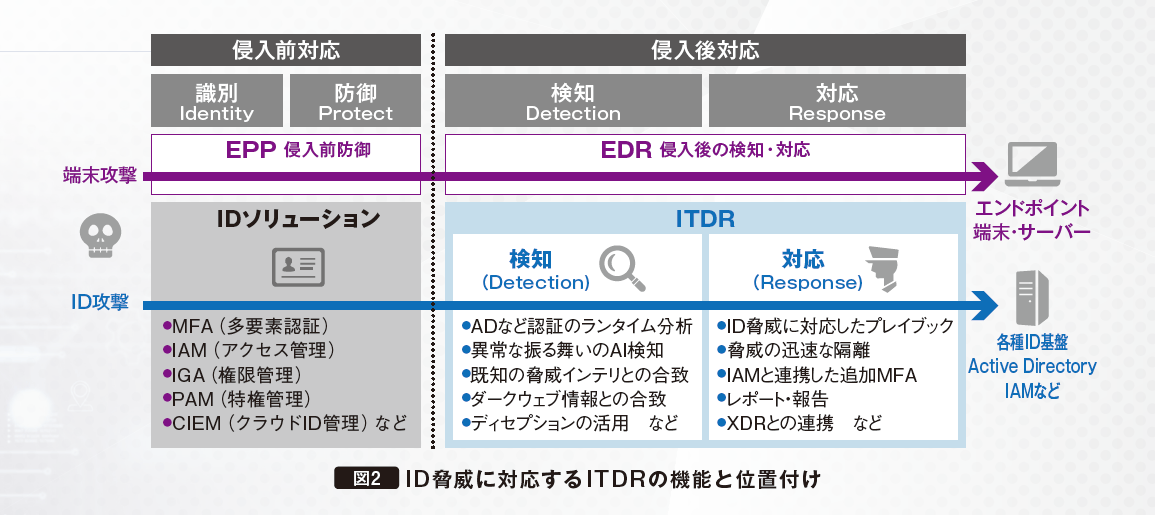
Necessity of "ITDR" solution that detects and protects ID threats that EDR cannot prevent

Kazuki Tsunemoto, Chief of Security Division 2 Sales Department, Macnica Networks Company, points out, ``With zero trust, ID-based access control will become mainstream, and ID will become the new boundary for companies.'' There is already a lot of interest in integrating authentication through IDaaS, with Macnica survey revealing that more than 50% of Japanese companies are implementing it.
Meanwhile, attackers are targeting identity information to gain entry into Zero Trust environments. Even with the introduction of EDR, which detects behavior based on the assumption that a device has been compromised, it is difficult to detect impersonation using a legitimate ID, and the damage is increasing.
Therefore, attention has been focused on ITDR (Identity Threat Detection and Response), a solution that detects and responds to threats based on behaviors such as authentication, based on the assumption that services for identity management such as Active Directory (AD) and IDaaS are compromised. (Figure 2). For example, attacks targeting IDs (attempts to steal passwords), abnormal access behavior (unusual IP address/simultaneous access from multiple locations), suspicious accounts (login with an unusual user/dormant account), It is possible to detect activities such as usage) as a threat and automate responses such as device isolation.
CrowdStrike 's ITDR has three major advantages. One of them is XDR, which integrates EDR and ITDR. Since EDR and the console can be integrated and operated, when an incident occurs, it is possible to check the risk score of the user or device and perform a correlation analysis with the ID. In addition, it supports multi-vendor ID infrastructure such as Okta, covers not only detection and response but also prevention, and also provides AD risk assessment.
Please download the rest of the document by clicking the button below.

Regarding the selection criteria and effects after implementation from CrowdStrike users,
We will introduce you in detail.
Inquiry/Document request
In charge of Macnica CrowdStrike Co., Ltd.
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00