product
- What you can do with CrowdStrike
- CrowdStrike Modules Falcon
- Falcon Prevent(NGAV)
- Falcon Insight(EDR)
- Falcon OverWatch (Threat Hunting)
- Falcon Discover (IT Asset Management)
- Falcon Spotlight (vulnerability management)
- Falcon Adversary Intelligence
- Falcon Identity Threat Protection/Detection
- Falcon Cloud Security(CNAPP)
- Falcon Surface(EASM)
- Falcon Shield(SSPM)
- Falcon Next-Gen SIEM
service
Application for evaluation machine
- FAQ

CrowdStrike
CrowdStrike
Hunt threats in a short period of time - CrowdStrike CrowdStrike

In recent years, cyberattacks targeting organizations have become more sophisticated, and EDR (Endpoint Detection and Response) is attracting attention as a security measure to counter these threats. CrowdStrike's "CrowdStrike Falcon" from the United States has been recognized as the industry leader in third-party evaluations among EDRs.
We spoke to Taku Nakajima and Fumihiko Igata of Macnica, the sole distributor in the Japanese market, about the system's advantages and the expected benefits of its introduction.
Detect unknown threats with expert threat hunting
Attackers who bypass existing security measures such as security measures at gateways and anti-virus measures at endpoints and infiltrate covertly carry out various malicious activities such as spreading infection and collecting information at endpoints. EDR can be used to expose such hidden fraudulent activity, identify the details of fraudulent activity, and respond appropriately to prevent the spread of damage.
In selecting an EDR, it is important not only to have advanced analysis functions, but also whether the vendor has excellent intelligence. The amount of information that EDR obtains from endpoints is very large, and most of it is the result of normal endpoint processing. Attackers are constantly devising new methods of concealment to hide their malicious activity in this flood of logs. Having information on the latest techniques is key to detecting fraudulent activity and determining the correct response.
“EDR requires expert point of view intelligence that is familiar with CrowdStrike Holdings、Inc. activity. 's intelligence is quickly reflected in our EDR product "CrowdStrike Falcon" and is used for detection.As a result, we are able to quickly detect and investigate advanced attacks using the latest techniques. (Mr. Nakajima)
Many of CrowdStrike Holdings、Inc. 's security experts are also employed in the managed hunting service "Falcon OverWatch" (OverWatch) provided by CrowdStrike Falcon.
Regarding this service, Mr. Nakajima said, "General SOC services receive alerts from security products and perform initial response and analysis, but OverWatch is not such a passive service. CrowdStrike Falcon user environments around the world Security experts monitor the collected information in real time and actively hunt for threats."
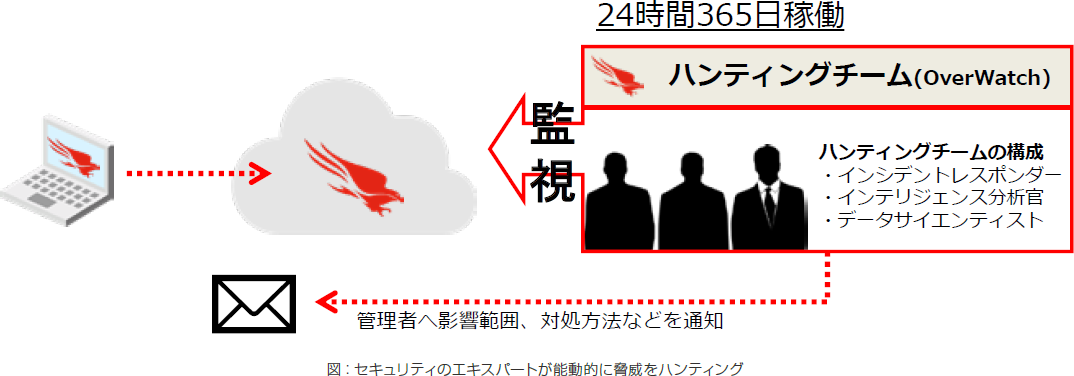
OverWatch offers 24/7 active threat hunting that leverages expert experience rather than relying solely on mechanical sensor detection. Companies using this service can discover threats that have been infiltrated by circumventing existing security measures.
"In recent years, the speed at which attackers spread infections within an organization's network has increased dramatically. According to the 2018 CROWDSTRIKE GLOBAL THREAT REPORT released by CrowdStrike Holdings、Inc., it is said to take less than two hours. It takes about 100 days for the defender to notice an attack on average, and there are many cases where it is only after someone outside the organization points it out.As such, there is a large gap between the attacker and the victim And threat hunting is a countermeasure against threats that defenders do not notice.” (Mr. Nakajima)
A single agent for visualization, prevention, detection, and response
CrowdStrike Falcon has another big feature. The architecture provides not only EDR but also EPP (Endpoint Protection Platform), that is, various functions for protecting endpoints, with a single agent.
“In addition to next-generation antivirus (NGAV), this agent also has functions such as vulnerability visualization and restrictions on the use of USB devices. Emergency measures such as quarantining and stopping malicious processes can also be executed.Furthermore, it is also possible to detect endpoints on the same segment where agents have not been installed.In addition to EDR, antivirus and IT asset management,” explains Igata.
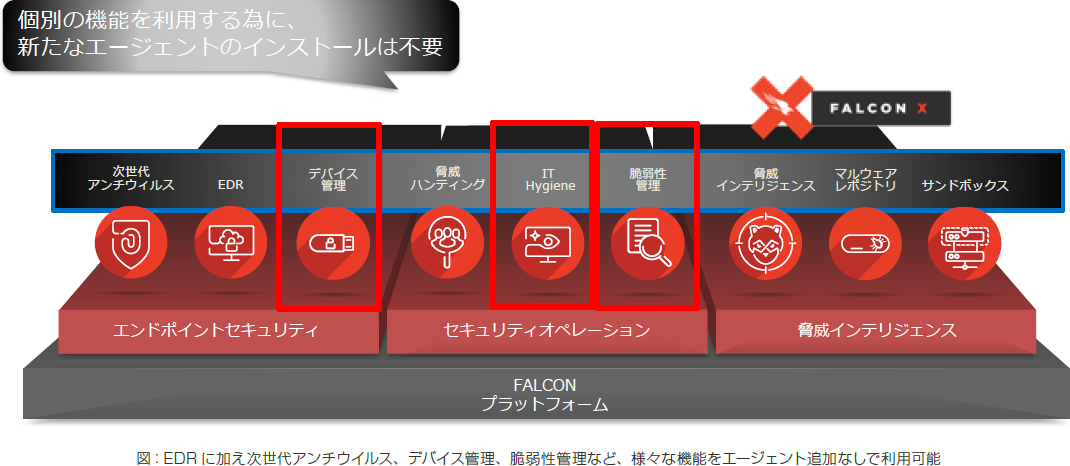
With this single-agent architecture, it is possible to integrate a series of countermeasures, from preventive measures such as visualization of stray devices and vulnerabilities, control of USB devices, detection and blocking of threats, and subsequent countermeasures. Needless to say, it is much more advantageous in terms of operation than introducing NGAV, EDR, IT asset management, USB device management, etc. separately. Because of these benefits, some organizations that are considering new EDR deployments are using CrowdStrike Falcon to replace the antivirus and IT asset management they have been using.
Moreover, since CrowdStrike Falcon is provided as a cloud service, you can manage endpoints that are directly connected to the Internet instead of LANs without any change.
“Some of the solutions that manage endpoints can only be managed by terminals within the LAN, but such mechanisms can pose challenges in initiatives such as work style reforms and digital transformation (DX). , Falcon can also be used to effectively protect portable terminals that are difficult to handle with existing solutions, terminals for remote work, and overseas or small-scale bases." (Mr. Igata)
日本でも多数の採用実績。10万ライセンス以上の大規模ユーザーも

Macnica was quick to recognize the potential of CrowdStrike Falcon, and in 2013 concluded a general agency agreement with CrowdStrike in Japan, and has been engaged in sales activities in the Japanese market.
There are currently about 100 users in Japan. On Macnica 's website, examples of Japanese users include Joyo Bank and Yokohama National University, as well as a large user with 100,000 licenses.
“In the first place, since EDR analyzes more deeply than conventional security products, the operational load tends to be heavy, so outsourcing is also an important option. Now, how about thinking about the future environment, including the operation?” (Mr. Igata)
Inquiry/Document request
In charge of Macnica CrowdStrike Co., Ltd.
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00