Macnica is the No. 1 distributor of Symantec products in Japan.
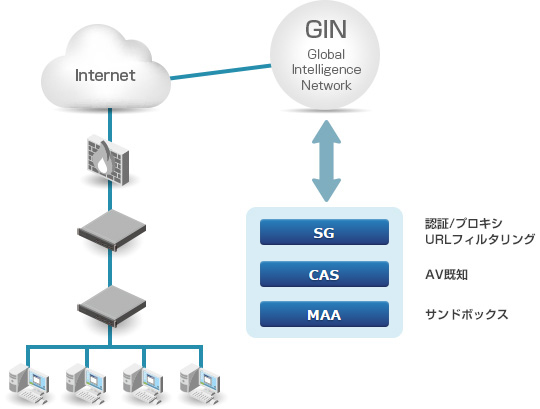
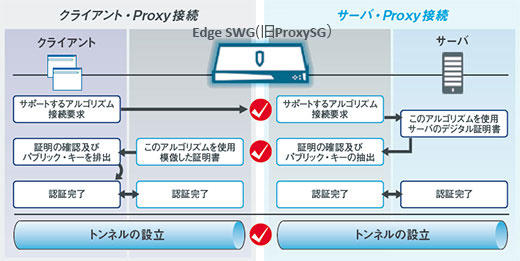
Edge SWG (formerly ProxySG)
包括的なWebセキュリティ機能を実装
Features
Dedicated proxy appliance is safe and fast
Equipped with SGOSTM, a self-developed operating system optimized from the kernel, it achieves high performance, robust security of the appliance itself, and easy installation and operation management.
Rich protocol control
Control HTTP, HTTPS, FTP, Telnet, SOCKS, P2P, TCP Tunnels, IM, Windows Media, Real Media, Quicktime, DNS, MAPI, CIFS, RTMP with features such as protocol termination, application layer visibility and policy control To do.
Relief from complicated operation management and increased burden
Perform a wide variety of security operations on a single platform. In addition, the intuitive web management interface allows you to easily and centrally manage policy rule settings.
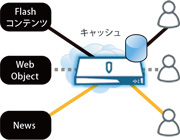
Advanced caching features
A proprietary cache algorithm automatically stores frequently used data on the HDD. Web access is accelerated by hitting objects in the cache and setting up multiple TCP sessions.
* RTMP cache is supported from SGOSv6.1, paid license
ユーザ認証
By linking with an authentication server such as LDAP, Radius, or Active Directory, you can set policies for each user or group. The authenticated user is reflected in the access log, and the web usage status of the user can also be grasped.

Access Control (Visual Policy Manager)
Multiple layers and multiple rules belonging to each layer enable flexible policy creation with various attributes as triggers.
Security policy implementation example
- Only HR departments are allowed to view job-search-related sites. Other departments are not allowed to browse.
- Strict regulation is applied during business hours, and free browsing is permitted depending on the category during lunch breaks.
Layer type
- Admin Authentication Layer
- Web Access Layer
- Socks Authentication Layer
|
- Web Authentication Layer
- DNS Access Layer
- Forwarding layers
|
- Admin Access Layer
- Web Content Layer
- SSL Intercept Layer
|
- Admin Authentication Layer
- Web Access Layer
- Socks Authentication Layer
- Web Authentication Layer
- DNS Access Layer
- Forwarding layers
- Admin Access Layer
- Web Content Layer
- SSL Intercept Layer
| 1.Source conditions |
2. Destination conditions |
3.Service terms |
- Client IP/SUBNET
- Authentication User/Group
- user agent
- ProxyIP/Port
- Request header etc.
|
- DstIP/SUBNET
- Hostname
- URL (Domain, scheme, path, regular expression)
- Extension MIME TYPE
- レスポンスヘッダ
- Response code, etc.
|
- Protocol (HTTP, FTP, Streaming, Telnet, etc.)
- Protocol methods (Get, Post, Put, Connect, Head, etc.)
- ICAP error code
|
| 4.Time conditions |
5.Action |
6.Track |
- year, month, date, day of the week
- hour, minute
- Duration, LocalTime, UTC Time
|
- Allowed, Not Allowed
- display any error screen
- HTTP compression
- More than 40 actions such as displaying a warning page
|
- Notifications via Eventlog, Mail, Syslog, SNMP
|
1.Source conditions
- Client IP/SUBNET
- Authentication User/Group
- user agent
- ProxyIP/Port
- Request header etc.
2. Destination conditions
- DstIP/SUBNET
- Hostname
- URL (Domain, scheme, path, regular expression)
- Extension MIME TYPE
- レスポンスヘッダ
- Response code, etc.
3.Service terms
- Protocol (HTTP, FTP, Streaming, Telnet, etc.)
- Protocol methods (Get, Post, Put, Connect, Head, etc.)
- ICAP error code
4.Time conditions
- year, month, date, day of the week
- hour, minute
- Duration, LocalTime, UTC Time
5.Action
- Allowed, Not Allowed
- display any error screen
- HTTP compression
- More than 40 actions such as displaying a warning page
6.Track
- Notifications via Eventlog, Mail, Syslog, SNMP
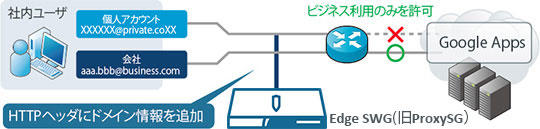
Restrictions on private accounts when introducing Google Apps
It is possible to restrict the use of private Gmail when using Google Apps. Edge SWG (formerly ProxySG) adds domain information to the HTTP header for communications to the Google server, allowing the server to accept only business domain emails and restrict private Gmail usage. allows you to
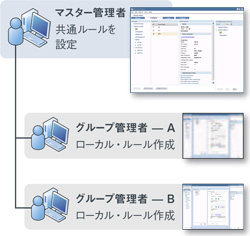
Integrated management and group administrator functions
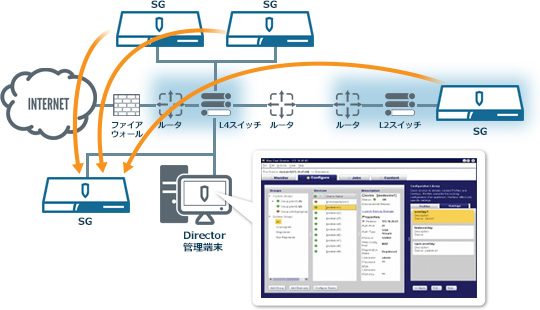
By using Director, you can set multiple Edge SWGs (formerly ProxySG) on a single management screen. In addition, administrators can be set for each group and delegated to create web access rules.
Rules that group admins can create
About "URL Lists" and "Category Lists"
deny access
allow access
rules can be set
Bulletin board write (POST method) control
By controlling postings on bulletin board sites, it is possible to prevent information leaks from the Web.
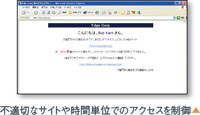
Display of warning screen
By displaying a warning screen that matches the access policy, the company's Internet access policy can be made known/enforced.
Visibility and control of HTTPS communication
The SSL proxy function decrypts encrypted HTTPS communication and blocks spyware, viruses, and information leaks from webmail that try to evade.
IPv4 ⇔ IPv6 translator *supported from SGOSv5.5
Since requests in IPv4 format can be automatically converted to IPv6, it is possible to access servers on the IPv6 Internet on behalf of clients that can only use IPv4. You can continue your business without upgrading your applications and network infrastructure to IPv6.
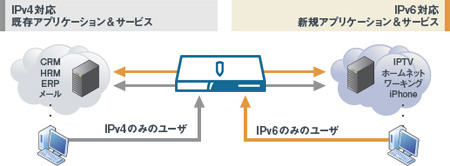
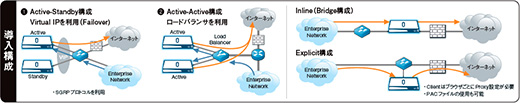
Deployment configuration
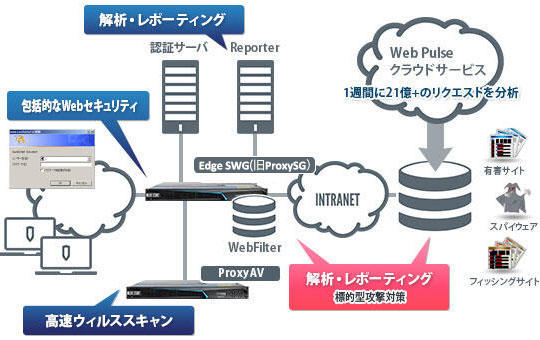
Blue Coat Intelligence Services
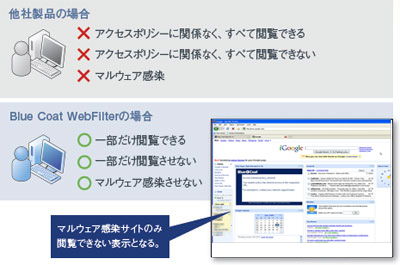
High-precision URL filtering with security features
Blue Coat Intelligence Services combines URL filtering and anti-malware capabilities (Web Pulse cloud analytics) to help keep users productive, stop malware downloads and web threats, and enforce compliance.
Blue Coat Intelligence Services Features
| supported language |
Enhanced Japanese web page and global support (more than 54 countries) |
| number of categories |
80 categories |
| Scalability |
User-definable custom categories |
| Flexibility |
1サイト最大4つのカテゴリに分類 |
| High precision |
Proprietary machine analysis and dedicated evaluator analysis |
| Security |
Hybrid defense of security category and real-time reputation* |
| problem solving |
Categories can be modified in as little as one day |
* The security category updates the database once every 5 minutes, always responding to the latest threats.
Threats Stopped with Hybrid Defense
- Keyloggers, botnets, phishing, spyware, unknown malware
- Fake software update, Fake AV pattern file update
- Tampered web redirect attack ・・・etc
POINT
Threats that signature-based threat protection cannot protect against
Symantec products prevent intrusions with WebPulse!
Advantages of multi-host pages and dynamic URL link support
- If there is a link to a site that is "not permitted" within a site that is "permitted" in the access policy, only that link will be blocked.
- If malware is installed in a link on a good site, the connection is blocked only for that link, preventing the intrusion of malware.
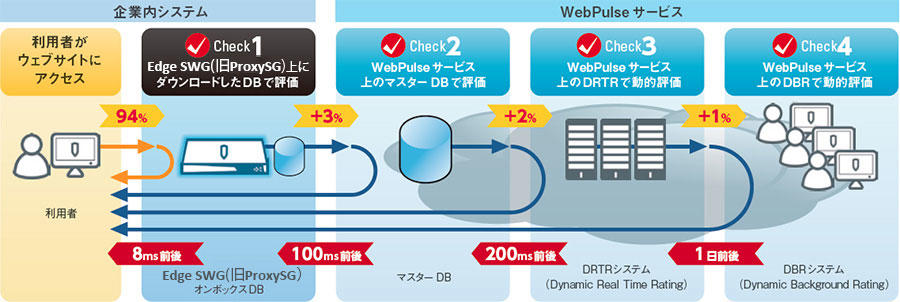
A hybrid URL filtering system linked with cloud services
WebPulse aggregates, evaluates, and classifies unknown website information sent from Blue Coat Intelligence Services users around the world in real time, and provides the results to users with feedback from the threat detection engine. Newly classified information can be updated at intervals of up to 5 minutes.
- Create a database based on a huge amount of actual access information by users around the world
- A system that fully considers the diverse usage situations of the world
-
- WebPulse: Cloud network type URL filtering service
- DRTR/DBR: Dynamically analyze and evaluate uncategorized sites and categorize them
Blue Coat Intelligence Services Category
Abortion, Adult/Mature Content, Liquor, Alternative Spirituality/Faith, Arts/Culture, Auctions, Audio/Video Clips, Securities/Commerce, Business/Economy, Charity/Non-Profit, Chat/SMS, Child Pornography, Cloud Infrastructure , Threatened Sites, Computer/Information Security, Content Delivery Networks, Controlled Substances, Cryptocurrencies, Dynamic DNS Hosts, Ecards/Invitations, Education, Email, Email Marketing, Entertainment, File Storage/Sharing , Finance, Children's, Gambling, Gaming, Gore/Extreme, Government/Legal, Hacking, Health, Humor/Jokes, Informational, Internet Connected Devices, Internet Telephony, Lingerie/Swimwear, Job Search/Career, Malicious outbound data/botnets, malicious sources/malnets, Marijuana, media sharing, military, mixed content/potentially adult, news, newsgroups/forums, nudity, office/business applications, online meetings, Peer-to-Peer (P2P), Personal Sites, Personal Ads/Dating, Phishing, Piracy/Copyright Concerns, Placeholders, Political/Social Advocacy, Pornography, Potentially Unwanted Software, Proxy Avoidance, Radio/Audio Streaming , real estate, reference, religion, remote access, restaurant/food, fraud/questionably legal, search engine/portal, sex education, shopping, social network, social/daily life, software download, spam, sports/recreation, questionable, technology /Internet, Tobacco, Translation, Travel, TV/Video Streaming, Uncategorized, URL shortening, Vehicles, Violence/Intolerance, Weapons, Web Advertising/Analytics, Web Hosting, Web Infrastructure
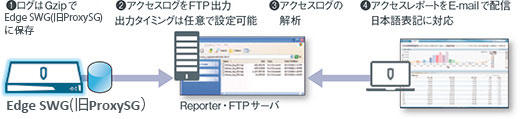
Reporter
Strengthen internal controls and visualize security
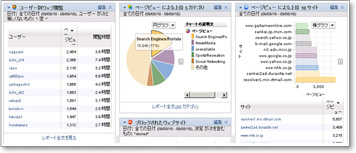
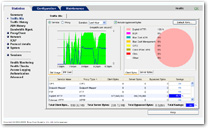
Reporter is a powerful analysis and reporting tool that visualizes all web usage in your enterprise. At-a-glance, customizable dashboards and reports are intuitive and easy to understand, with drill-down views. Reporter plays a critical role in business-critical initiatives such as security, compliance enforcement, and bandwidth management.
report
Predefined log analysis reports can be scheduled and automatically emailed.
trend analysis
You can grasp the web access status from various angles with the preset template.
Close-up analysis
You can drill down into interesting logs discovered by trend analysis and pinpoint the problem.
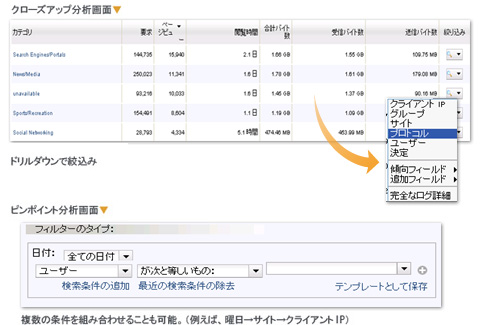
Pinpoint analysis
If the target of log analysis is clear, you can quickly grasp the problem by setting analysis conditions.
Analysis conditions
Date → Client IP, Group, Site, Malware, User, Time Zone, Day of Week, Equal, Not Equal, Include, Not Include, etc.
View reports according to permissions
With authentication using LDAP or username/password, users with viewing privileges can view a set range of reports.
- Give managers access to data about their direct reports
- Give each user access to their own usage data
* Up to 50 accounts can view reports simultaneously.
Integrated management
WDirector is an appliance that provides a single point of control for distributed Edge SWGs (formerly ProxySGs). Automate change, policy, and configuration management for Edge SWG (formerly ProxySG) and apply policies by region, branch office, or logical group to customize enterprise or organization-wide management.
Centralized management from a single point eliminates the need for IT personnel to work directly with each device. This maximizes productivity and enables you to respond to emerging problems and threats in a timely and effective manner.
Main management functions
- You can quickly configure and deploy additional devices.
- You can easily upgrade your existing system.
- New policies and configurations can be managed centrally by device, by group of devices, or by region.
- It enables proactive network management and prevents problems before they occur.
| 1. Configuration management |
2. Policy management |
3. Content management |
|
Edge SWG (formerly ProxySG) appliance configuration standardization, failure protection, centralized monitoring and control
|
Distribute and synchronize application delivery and security policies across your organization
|
Reduce consumption of valuable resources with bandwidth policies and content controls
|
1. Configuration management
Edge SWG (formerly ProxySG) appliance configuration standardization, failure protection, centralized monitoring and control
2. Policy management
Distribute and synchronize application delivery and security policies across your organization
3. Content management
Reduce consumption of valuable resources with bandwidth policies and content controls