
Falcon Shield
Falcon Shield
Who’s in control: The SaaS app administrator paradox
Imagine being locked out company-wide from your company's CRM app, like Salesforce, because your organization's external administrators tried to disable MFA for their own convenience. This external administrator doesn't consult with the security team or consider the security implications, and acts solely on the ease of login that his team needs.
However, this CRM app defines MFA as the top security setting. For example, Salesforce has a setting called "High Assurance Login Value" that immediately locks out all users who don't use MFA as a safety measure. In that case, the entire organization will be brought to a standstill, which will have a major impact on operations.
The big concern is that this is not a one-time event. Administrators of business-critical SaaS apps are often outsiders to the security department and have significant control. These managers, who are not focused on security measures, are working to improve their department's KPIs. For example, Hubspot is usually owned by the marketing department, and Salesforce is usually owned by the business department. Business units own SaaS apps because they allow them to get work done more efficiently. However, securing a company's SaaS app stack from a security perspective is the responsibility of security teams, and to do so effectively, full control of SaaS apps is essential.
The 2022 SaaS Security Survey Report, conducted by CSA and Adaptive Shield, delves deeper into this paradox, presenting data collected from CISOs and security professionals. In this article, we examine key data from survey respondents and consider solutions for security teams.
SaaS apps under business unit control
A typical company uses a variety of SaaS apps, from cloud data platforms, file sharing apps, and collaboration apps to CRM apps, project management, work management, marketing automation, and more (see Figure 1). Individual SaaS apps are required to fulfill specific niche roles required by businesses. Without SaaS apps like these, you could fall behind your competitors and take longer to hit your KPIs.
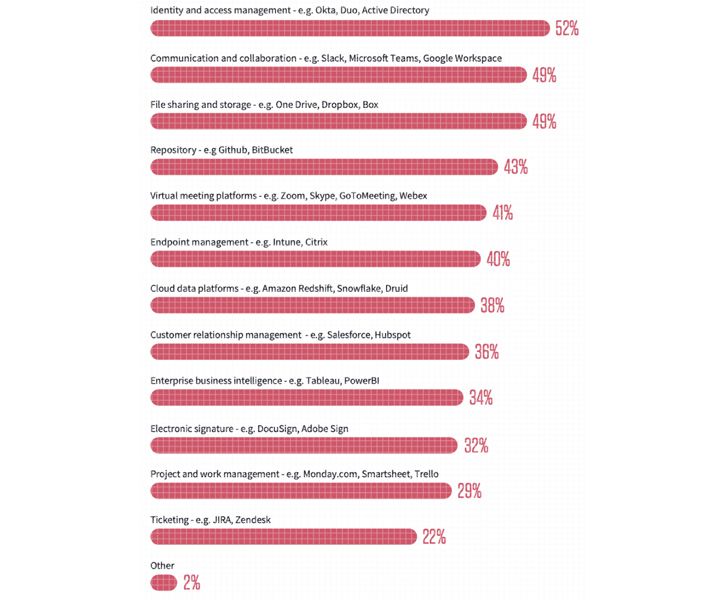
Figure 1: Types of apps used (2022 SaaS Security Survey Report)
According to the 2022 SaaS Security Survey Report, 40% of SaaS apps are managed and owned by non-security teams such as sales, marketing, and legal departments (see Figure 2). According to the report, management of SaaS apps is primarily left to security and IT teams, but complicating the threat landscape is that 40% of management is done by business units that have full access rights.
Security teams can't take that ownership away. This is because business application owners need to maintain a high level of access to related SaaS apps to optimize the apps for ease of use. However, it is unreasonable for security teams to expect business app owners to ensure a high level of SaaS security without deep knowledge of security or vested interests (security KPIs that affect departmental work outcomes).
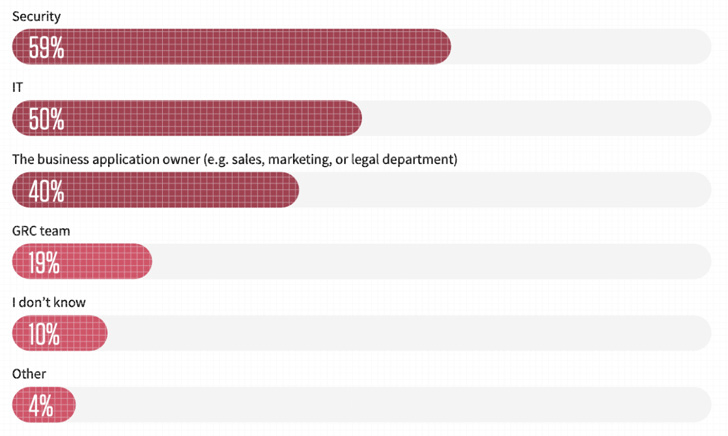
Unraveling the SaaS app ownership paradox
When asked about the main causes of security incidents caused by misconfiguration (Figure 3), survey report respondents cited the following as the top four causes:
- Too many departments have access to security settings
- Changes to security settings are not visible
- Lack of knowledge about SaaS security
- Abuse of user privileges
All of these reasons lie directly or indirectly in the SaaS app ownership paradox.
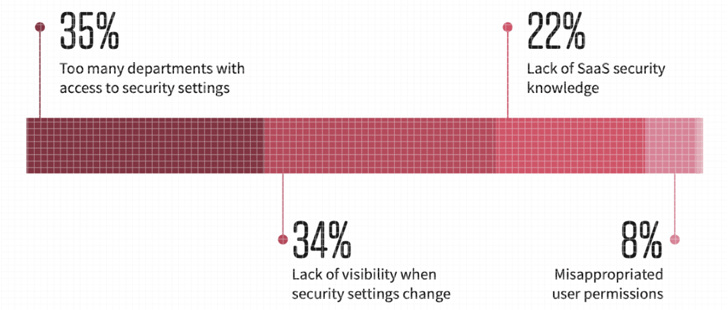
Figure 3: Top causes of security incidents (2022 SaaS Security Survey Report)
A major cause of security incidents caused by misconfigurations is that too many departments have access to security settings. This is closely related to the second most common cause: lack of visibility into security changes. The business unit may change app settings to optimize the app's usability without consulting or notifying the security department.
Additionally, business unit owners who do not pay sufficient attention to security can easily cause misuse of user privileges. Users are often granted privileged permissions that they don't need.
How security teams can take back control
The only efficient way to bridge the communication gap in this shared responsibility model is with SaaS Security Posture Management (SSPM). When an organization's security team owns, manages, and utilizes an SSPM solution, it ensures that the security team has complete visibility into all of the company's SaaS apps and their security settings, including user rights and permissions. I can.
Businesses can go a step further and add app owners to the SSPM platform so they can proactively view and manage all settings for their apps. Scoped administrators (Figure 4) allow security teams to grant app owners access to their apps. This allows security teams to remediate security issues with the app owner's permission.
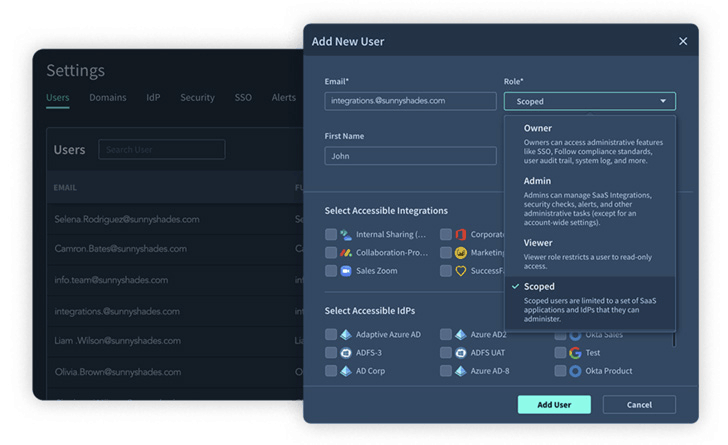
Figure 4: Scoped Administrator feature in Falcon Shield's SSPM platform
There is no way to prevent a business unit from accessing the security settings of a SaaS app. Educating users across the organization on the basics of SaaS security should reduce the risks that business units can pose, but this isn't always possible, and even when it is, it's not enough. To avoid situations like this, use a solution that gives security teams visibility and control through alerts on configuration changes, audit logs that collect and visualize actions within SaaS apps, scoped administrators, and more. need to be introduced.
Inquiry/Document request
Macnica Falcon Shield
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00