活動を再開した「Emotet」マルウェアへの対応について
公開日:2020年 8月 7日
最終更新日:2021年 1月27日
Emotet と呼ばれるマルウェアが、2020年7月中旬頃から配布の活動を再開させています。複数のメディアや機関から情報が発信されているため、すでにご存知の方も多いかもしれません。
[参考]マルウエア Emotet の感染に繋がるメールの配布活動の再開について(追加情報)
そのような状況を受け、改めて弊社取扱製品での検知状況をまとめるとともに、弊社で観測した事例をいくつか紹介したいと思います。
Emotetの攻撃の流れ
弊社でもEmotet を使った攻撃を多数確認しておりますが、今の所、前回の国内で被害が多く発生した攻撃キャンペーン時と比較し、マルウェアの機能改善はあるものの、手法自体には大きな変更がないように思えます。
※直近の攻撃において、特徴的な変化が確認された場合には本ページを更新していきたいと思います。
マルウェア「Emotet」感染までの攻撃は以下の流れで行われます。
- 添付ファイル付きメールが配送※1
- メールに添付されたWordファイルなどのOffice文書を開封
- マクロの有効を許可
- マクロ経由でWMI※2が実行され、さらにPowerShell が起動
- PowerShellがEmotet マルウェアのダウンロードと実行
- Emotet マルウェアに感染
※1 のタイミングで、添付ファイルの代わりにURLリンク付きメールが配送されるケースも確認されています。この場合、メール本文中のURLをクリックすると、Word ファイルなどのOffice文書がダウンロードされます。
※2 WMI = Windows Management Infrastructureと呼ばれるWindows OSの正規の管理ツール
弊社取扱製品における検出状況
以下は、弊社で入手したEmotetやお客様の環境で確認された事例をベースに、前述のEmotet の攻撃の流れの各ステップ(①~⑥)に照らして記載しております。
新たな攻撃手法が発生した際には結果が変化する可能性がありますことご留意ください。
| メーカー | 製品名 | 対応状況 |
| Broadcom | Symantec Endpoint Protection14 |
|
| CrowdStrike | Falcon |
|
| FireEye | FireEye EX/ETP/NX |
EX/ETP:
NX:
|
| Menlo Security | Menlo SecurityセキュアOffice 365/セキュアG Suite(メールアイソレーション) |
|
| McAfee | VirusScan Enterprise Endpoint Security MVISION Endpoint |
|
| Team T5 | TeamT5 ThreatSonar(Mpression Cyber Security Service™ スレットハンティング&インシデントレスポンスサービスで利用) |
|
攻撃メールについて
ここから弊社が観測できたメールサンプルの一部をご紹介したいと思います。返信型の場合は、実際に弊社が送付したメールのリプライとして、攻撃が送付されてきます。それ以外のケースでは、時期にもよりますが「請求書」に関連した件名が多いように思います。
弊社が受信した攻撃の多くは、なりすましメール対策の一つであるSPF(Sender Policy Framework)をPassしておりました。またメールを滞りなく配送するためなのか、Display Name のみ偽装を行い、偽装したドメイン元がDKIM(DomainKeys Identified Mail)を設定している場合にもFailとはならず、Passしていました(一部、DKIMを利用していないドメインに対して、DKIMによる署名が施されているケースがあり、このケースではDKIMはFailとなっていました)。この表示名の偽装は、2019年年末のキャンペーンでも同様のようでした。
一般的には、SPF/DKIMなどのテクノロジーはなりすまし対策として有効と考えますが、このように回避されるケースもあるため、過信は禁物だと考えられます。
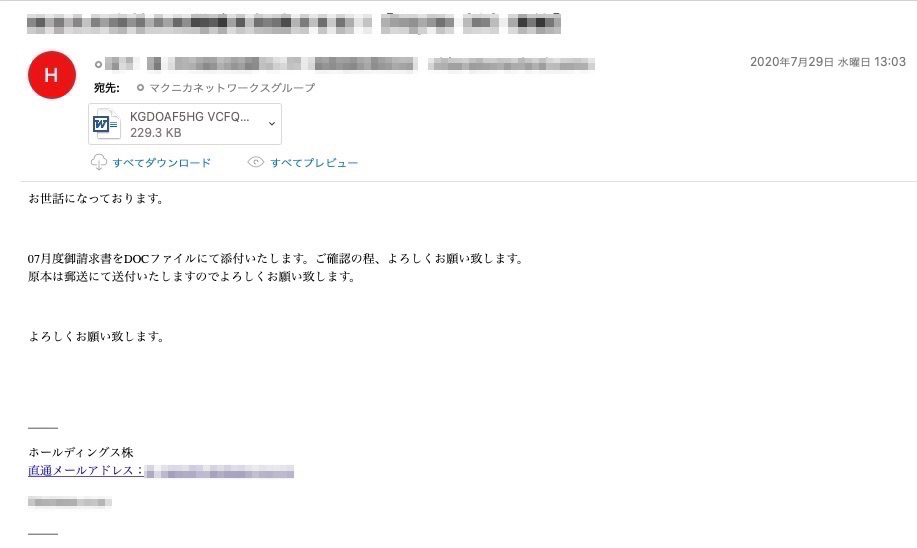
添付ファイルパターン
URLパターン

表示名にメールアドレスを利用しているパターン
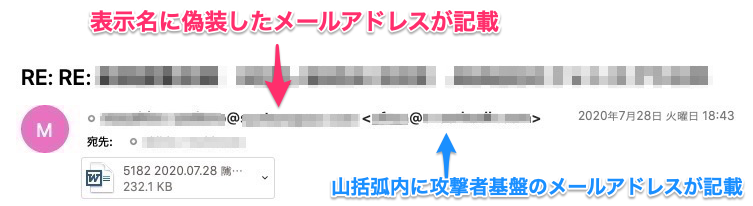
2020年9月から観測されている例
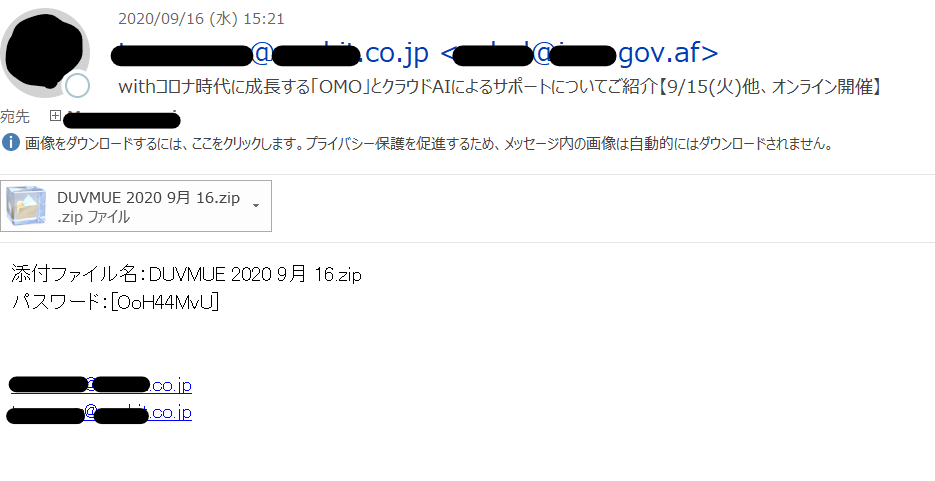
日本語本文が自然な事例
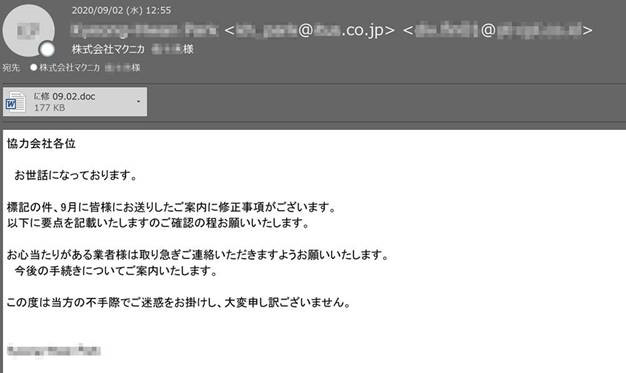
以下のケースでは、「表示名にメールアドレスを利用しているパターン」と同様の手口で送信者部分を偽装しています。また件名と宛先の表示名を一致させるような工夫がされていました。
メール内の本文自体についても、以前のメールと比べて不自然な点が少なくなっているように見受けられます。
また、上記以外にも、日本国内で広く流通する特定製品のサポート満足度アンケート調査を装うケースなども見つかっております。
日本語の不自然さでは見抜くのがますます難しくなっているように思えます。
怪しいファイルは開かない、万が一開いたとしてもマクロの有効化は行わない点について引き続き警戒が必要です。
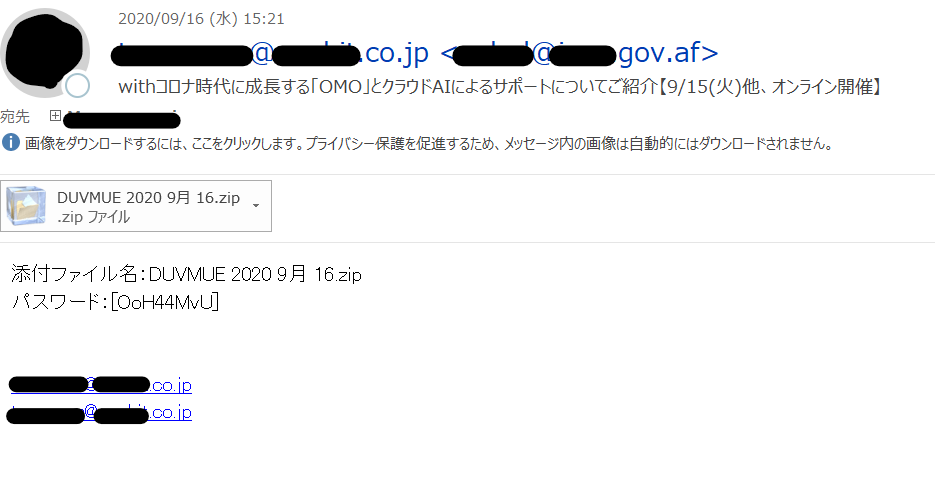
悪性ファイルがパスワード付きZIPで配送されてくる事例
一部のメールは、ZIPファイルのパスワード保護機能を利用して、悪性なファイルを配送しています。この攻撃の場合、本文中のパスワード表記やお使いのセキュリティメールゲートウェイによっては、検出できない可能性があります。エンドポイントでの監視などと複合的に対処されることをご検討ください。
2021年1月から観測されている事例
1月中旬より、Emotetを配布する活動が再開しています。弊社で確認できたサンプルを以下に記載します。また、詳細は割愛いたしますが、攻撃プロセスが上述のものから変化しております。主な変化点としては、.exe ファイルで配布されていたEmotet が .dll ファイルで配布されるようになっております。
緊急事態宣言に乗じたメール
緊急事態宣言に伴い、企業が実際に送信していたと思われるメールが悪用されています。メール本文自体に違和感を確認することはできません。そのため、改めて送信元メールアドレスを確認いただくことが重要と思われます。確認の際は、表示名ではなく 山かっこ内 "< >"を注視するようにしてください。表示名は取引先などを装っている可能性があります。
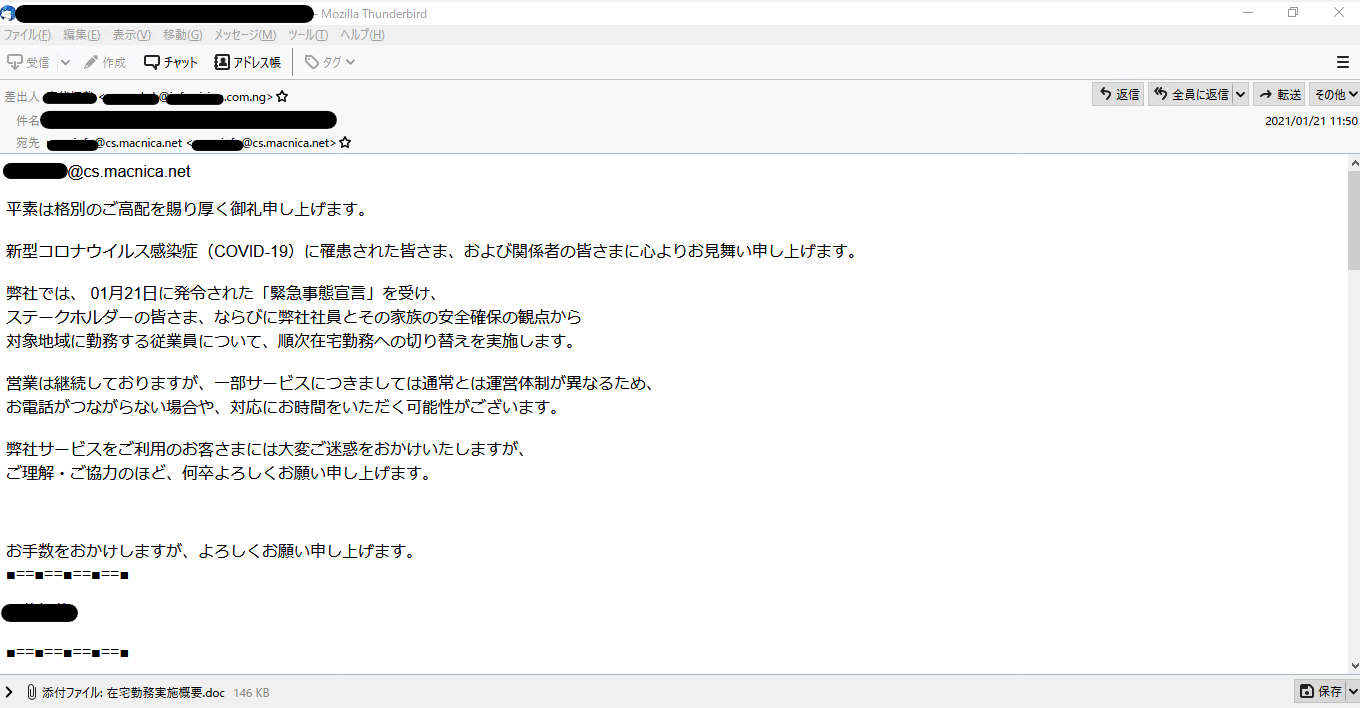
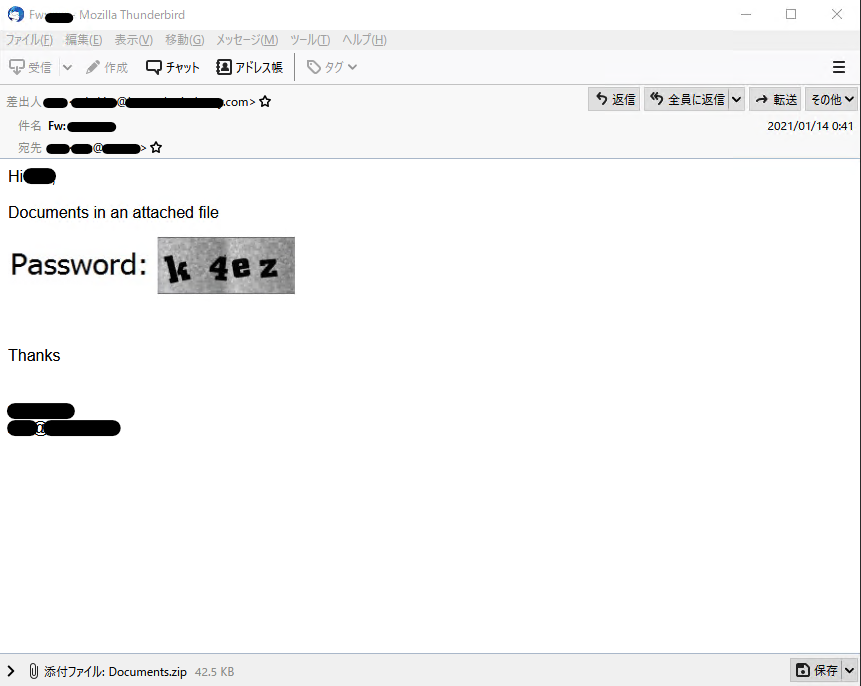
画像によるパスワード通知
ZIPファイルのパスワード保護機能を利用して、悪性なファイルを配送する手口は以前からありましたが、最近のEmotetの配送の手法として、以下のようにパスワードを画像として表記する方法が確認されています。この攻撃の場合、お使いのセキュリティメールゲートウェイでは、検出できない可能性があります。エンドポイントでの監視などと複合的に対処されることをご検討ください。