Business email compromise refers to fraudulent activity against businesses via email. In some cases, the emails are sent directly from the attacker, but in other cases, the supply chain companies are compromised in advance, the emails are snooped, and the emails are sent in the form of impersonating the supply chain company at the right timing.
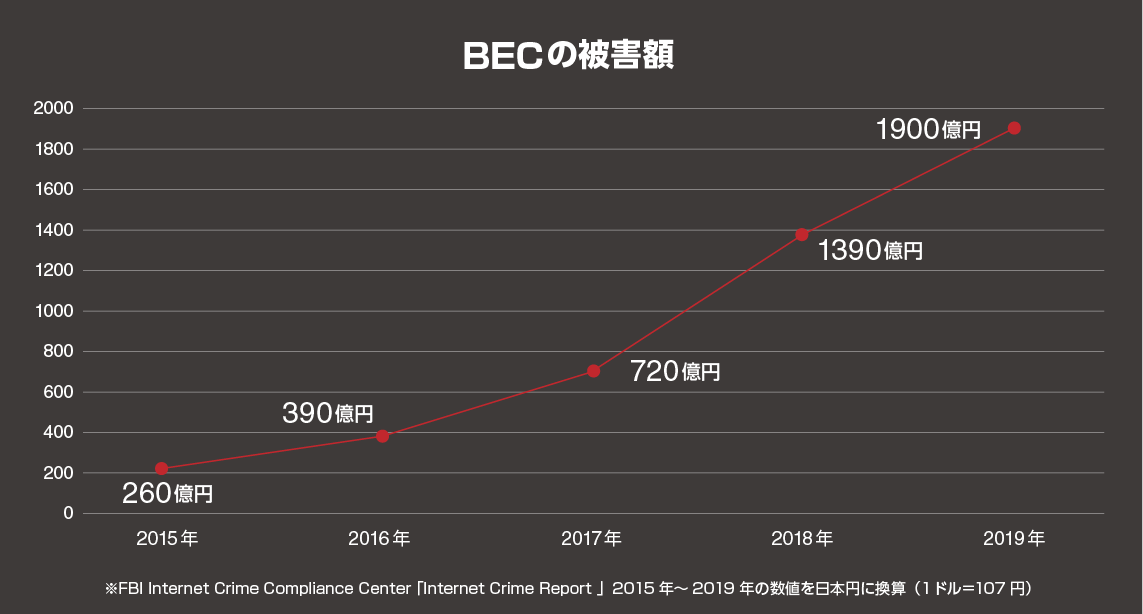
The damage caused by this attack is being reported every day, regardless of whether it is a company in Japan or overseas. In addition, the damage amount reported by the FBI in 2019 reached approximately 190 billion yen, and it is currently considered to be one of the threats that should be recognized. Below are the changes in the amount of damage reported by FBI IC3.
As mentioned above, many domestic and foreign companies have been reported to have suffered damage from BEC. We have not yet confirmed any trends such as specific fields being targeted. For example, in the example of an overseas municipality, part of the construction costs of a school was stolen by an attacker. At the time, the attackers were impersonating construction contractors.
Below is a summary of publicly available information. *1
Damage example
| Victim company | Publication time | Amount of damage *2 |
|---|---|---|
| Domestic airline industry | December 2017 | 380 million yen |
| united church | May 2019 | About 190 million yen (1.8 million US dollars) |
| US local government | August 2019 | About 270 million yen (2.5 million US dollars) |
| US local government | October 2019 | About 80 million yen (750,000 USD) |
| 国内自動車部品(欧州小会社) | September 2019 | 4 billion yen |
| Domestic publishing business (U.S. subsidiary) | October 2019 | About 3.1 billion yen (29 million USD) |
| British NGOs | February 2020 | About 130 million yen (932,000 pounds) |
| Puerto Rico government | February 2020 | About 280 million yen (2.6 million US dollars) |
| european investment fund | May 2020 | About 1.1 billion yen (US$10 million) |
*1: As of May 2020, we have listed the cases that we have been able to grasp.
*2: Calculated at 1 US dollar = 107 yen, 1 pound = 135 yen
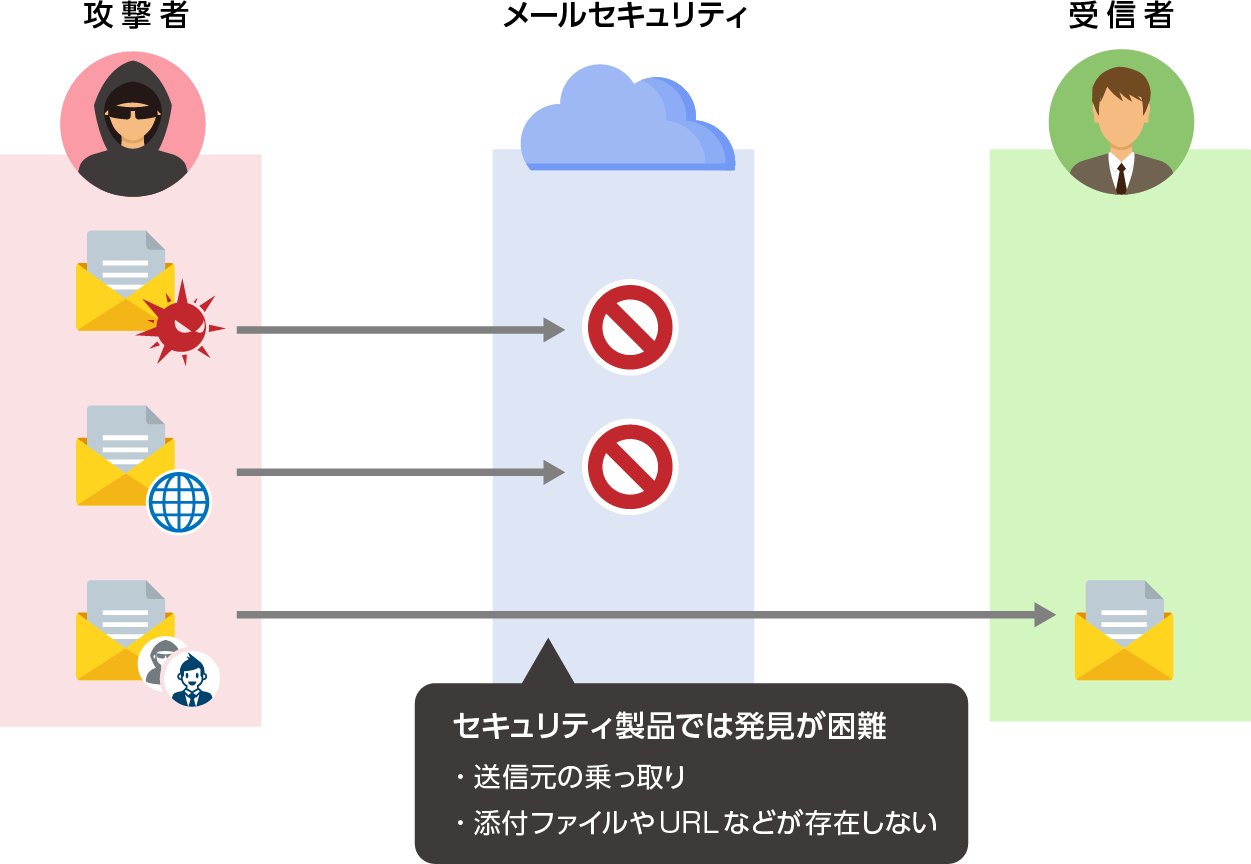
Defenders also recognize that this attack is basically based on a deception technique called social engineering, and that it is difficult to prevent damage with the conventional approach of discovering malicious points (attachments, URLs, etc.). This is the point you need to make.
BECの分類
BEC is categorized by the FBI, IPA, etc., but considering the difference in countermeasures, we classify it into the following two.
classification
Pattern 1. Direct form
A pattern in which an attacker commits fraud against a target company. Attackers pretend to be executives of their own organization or affiliated companies (such as supply chains) and communicate urgent and confidential requirements. There are cases where a third party impersonating a real lawyer intervenes once the exchange is done.

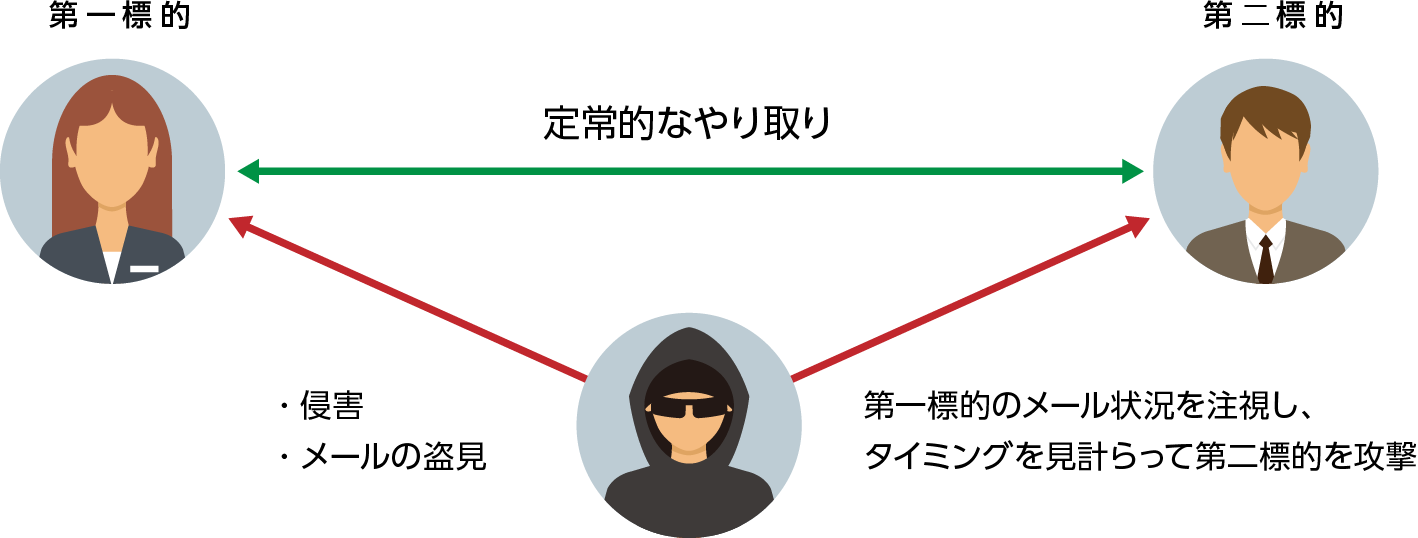
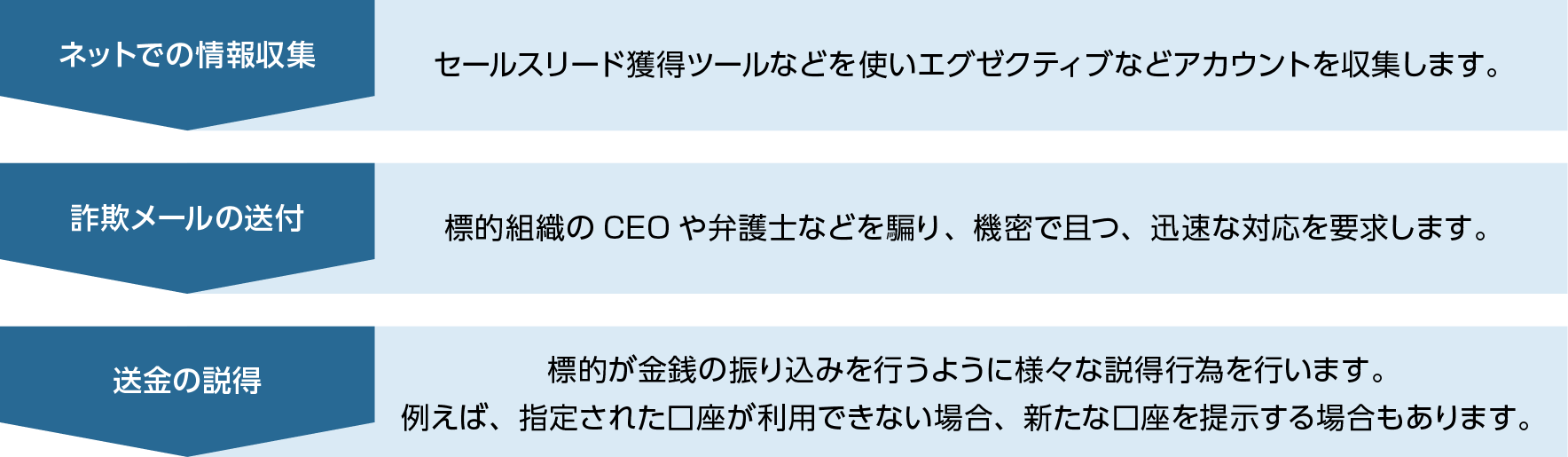
Pattern 2. Indirect/Partner Infringement
Attackers masquerade as business applications (Office365, etc.) used by companies to steal credentials through phishing, brute force attacks against publicly available email services, etc., or compromise using malware. infiltrate the email infrastructure of After that, after waiting for the invoice sent from the first target to the customer, the second target will be notified that the invoice has been replaced for various reasons and requested to make a transfer to the fraudulent remittance account. It is said that the primary target of the indirect type is often vendor companies, which often issue invoices, because of this kind of attack strategy.
Kill chain in BEC
Pattern 1. Direct form
Pattern 2. Indirect/Partner Infringement

Patterns for sending fraudulent emails
There are three possible deception methods in the phase of sending fraudulent emails in the kill chain in pattern 2 above. Each also has disadvantages for attackers.
technique
例)contact@example.comドメインを持つ企業が侵害されていた場合
| Attack method | Sender email address example | Advantages for attackers | Disadvantages for attackers |
|---|---|---|---|
| (1) Send an email from a compromised Box | contact@example.com | It is easy to deceive the target because there is no room for suspicion other than the content of the email. | Traces such as transmission history remain, and there is a high possibility of being discovered |
| (2) Send an email with a disguised email address | contact@example.com | Disadvantages of 1 are eliminated | If the primary target has sender authentication (DMARC) set, there is a high possibility that the email will not be delivered. |
| ③ Create a similar domain and send an email | contact@examp1e.com | Freely create and send email accounts | Recipients may discover that the source is a look-alike domain |
Countermeasure method
Countermeasures in BEC do not end with a solution to detect suspicious emails. It may be necessary to review operations and policies such as accounting. In addition, there are cases in which companies that have been spoofed or victims of fraud have shared the damages evenly, so it is not enough to take measures to prevent only one company from being deceived.
Based on the above kill chain, countermeasures are listed for each phase.
Proposed countermeasures in the kill chain
The following are kill chain-based countermeasures. For the sake of convenience, the description assumes that the mail service is built on SaaS, but most of them can be applied to on-premise systems as well.
Proposed countermeasure
| Attack procedure | Proposed countermeasure |
|---|---|
| Collecting information on the Internet | none |
| to your email account unauthorized logon |
|
| Box reconnaissance |
|
| Sending fraudulent emails |
|
| Persuasion to send money |
|
BEC email sample
Email example for Pattern 1:
In many cases, emails are sent impersonating an executive, such as the CEO of your own organization or an external organization. In many cases, you will be told that there is an urgent need for action, such as:
Also, in this pattern, there are cases where a similar domain (eg examp 1 e.com) is used as the sender, or free mail is used for Reply-To.