Specifications/Technical Information
Application for evaluation machine
- FAQ
How to comply with "NIST SP800-190"? Container image vulnerability management

How to deal with vulnerabilities that can be included in container images as a very important factor in considering container security? There are points like this. Regarding this point, in "NIST SP800-190" issued by NIST of the United States as a guideline for container security, recommended countermeasures against major risks are described as follows in "4.1.1 Image Vulnerability".
Vulnerability management tools and processes specific to container technology are required. Traditional vulnerability management tools make many assumptions about host durability and app update mechanisms and frequency that are fundamentally at odds with the containerized model. These tools often fail to detect vulnerabilities in containers, providing a false sense of security.
Organizations should use tools that incorporate a pipeline-based build approach and container and image immutability into their design to provide more actionable and reliable results. Key aspects of effective tools and processes include:
1. Integrate the entire image lifecycle, from the beginning of the build process, through the registry your organization uses, to the runtime.
2. Visibility into all layers of the image, not just the base layer of the image, but also the application frameworks and custom software used by the organization. Visibility should be centralized across the organization and provide flexible reporting and monitoring views tailored to the organization's business processes.
3. Policy-Driven Enforcement. Organizations should create "quality gates" at each stage of the build and deployment process to ensure that only images that meet organizational vulnerability and configuration policies are allowed to proceed. For example, organizations should be able to set rules in the build process to prevent the progression of images containing vulnerabilities with Common Vulnerability Scoring System (CVSS) [18] ratings above a selected threshold. .
Source: Excerpt from Japanese translation by NIST SP800-190 IPA
https://www.ipa.go.jp/files/000085279.pdf
As a concrete measure to implement the above, how does Prisma Cloud visualize open source vulnerabilities contained in container images? about,Palo Alto Networks blog postI will introduce it with reference to.
Where do you get vulnerability information?
What data sources do you get reliable vulnerability information for in detecting vulnerabilities in container images? is the important point. NVD (National Vulnerability Database) is a representative source of vulnerability information, but the blog post points out the following points as problems that depend only on NVD.
- By omitting the correct version range information for a specific vulnerability that a Linux distribution has fixed independently, it is possible to trigger alerts for vulnerabilities that would otherwise not be affected.
- You may miss specific vulnerability data published by the Linux distributions themselves.
- Some software vendors publish vulnerability advisories on their own dedicated webpages or feeds in parallel with issuing CVEs, or without issuing CVEs at all.
Therefore,Prisma Cloud feeds vulnerability information through a state-of-the-art mechanism that combines multiple official data sources (NVD, Linux distributions, security advisory information from various vendors). This allows us to provide customers with more reliable vulnerability alerts.
Uniquely covers vulnerabilities for which no CVE number has been released
Looking at the diagram below, it's very intuitive and easy to understand, but when using Prisma Cloud, information about CVEs that have not yet been reported by NVD or MITER, and information about maintainers in the vulnerability feeds of NVD and distributions Vulnerability information still under analysis is provided.
Since many vulnerabilities have been publicly discussed or patched before being assigned a CVE, Palo Alto Networks has independently assigned them a "PRISMA ID."
The purpose of this PRISMA ID is not to replace the CVE, but rather to bridge the gap between vulnerability disclosure and inclusion in the NVD, allowing customers to have earlier visibility into the risk of applicable vulnerabilities. increase.
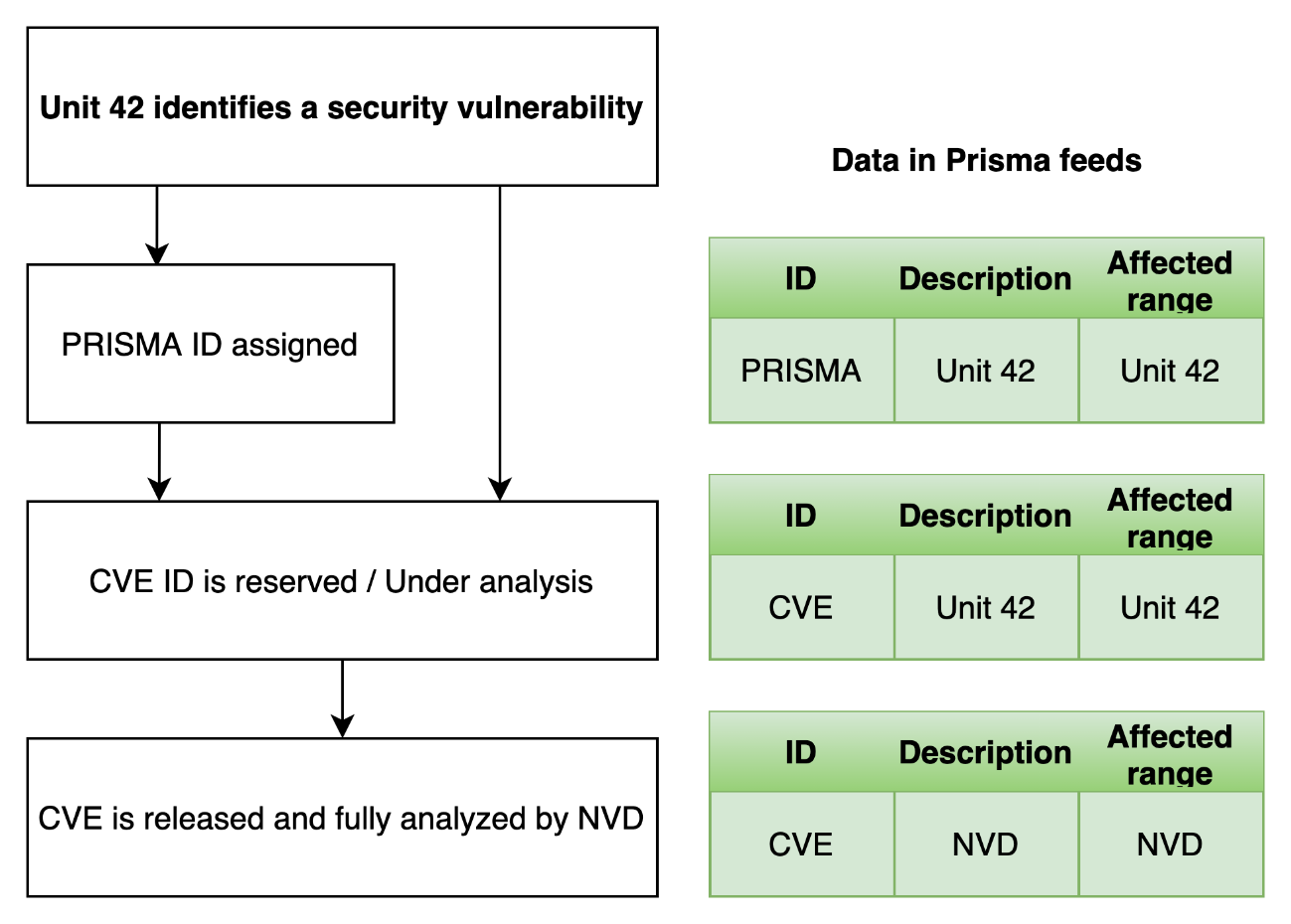
Image: Taken from https://www.paloaltonetworks.com/blog/prisma-cloud/open-source-vulnerability-management/
Summary
There are many tools, including free tools, that can simply visualize vulnerabilities in container images. is done. Of course, container image vulnerability management is just one part of Prisma Cloud's broad container security capabilities. If you are interested in implementing container security, please contact us.
Inquiry/Document request
In charge of Macnica DevOps
- TEL:045-476-1972
- E-mail:twistlock@macnica.co.jp
Weekdays: 9:00-17:00


