Specifications/Technical Information
Specifications/Technical Information
Evaluation machine application/FAQ
Application for evaluation machine
- FAQ

Github
github
Security with GitHub
Challenges in source code security
Application security
- Unable to identify dependencies and vulnerabilities of the OSS used by the company, and unable to identify the scope of impact
- According to internal rules, secret information should not be mixed into the source code, but it is not thoroughly enforced.
- I used a static analysis tool in the past, but I gave up on using it because a huge number of alerts were generated and the operation did not go well.
Security for users
- Since developers can edit the public settings of the repository themselves, there is a risk that confidential information such as corporate assets will be leaked.
- There is a risk of ID/password being stolen, personal access tokens or SSH keys being leaked, and unauthorized login being performed.
- An employee left the company, but was still accessible after leaving the company

Secure with GitHub Enterprise
Application Security
supply chain
of open source components
Stay safe and compliant
Stay safe and compliant
code
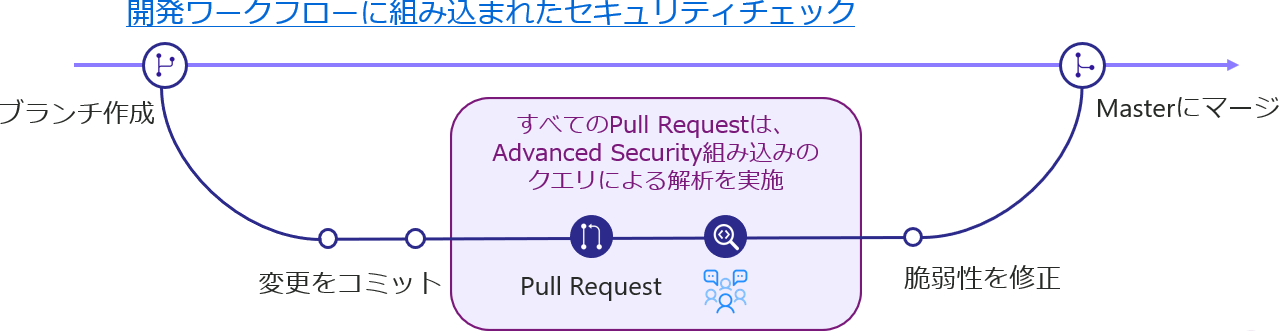
as part of the workflow
Detect and fix code vulnerabilities
Detect and fix code vulnerabilities
Development lifecycle
security and compliance
Create and execute policies as code
Create and execute policies as code
Developer Security
supply chain
by permission settings
Prevention of confidential information leaks
Prevention of confidential information leaks
code
By checking the connection source
secure access
secure access
Development lifecycle
Level of trust with multi-factor authentication and authorization
Access control according to
Access control according to
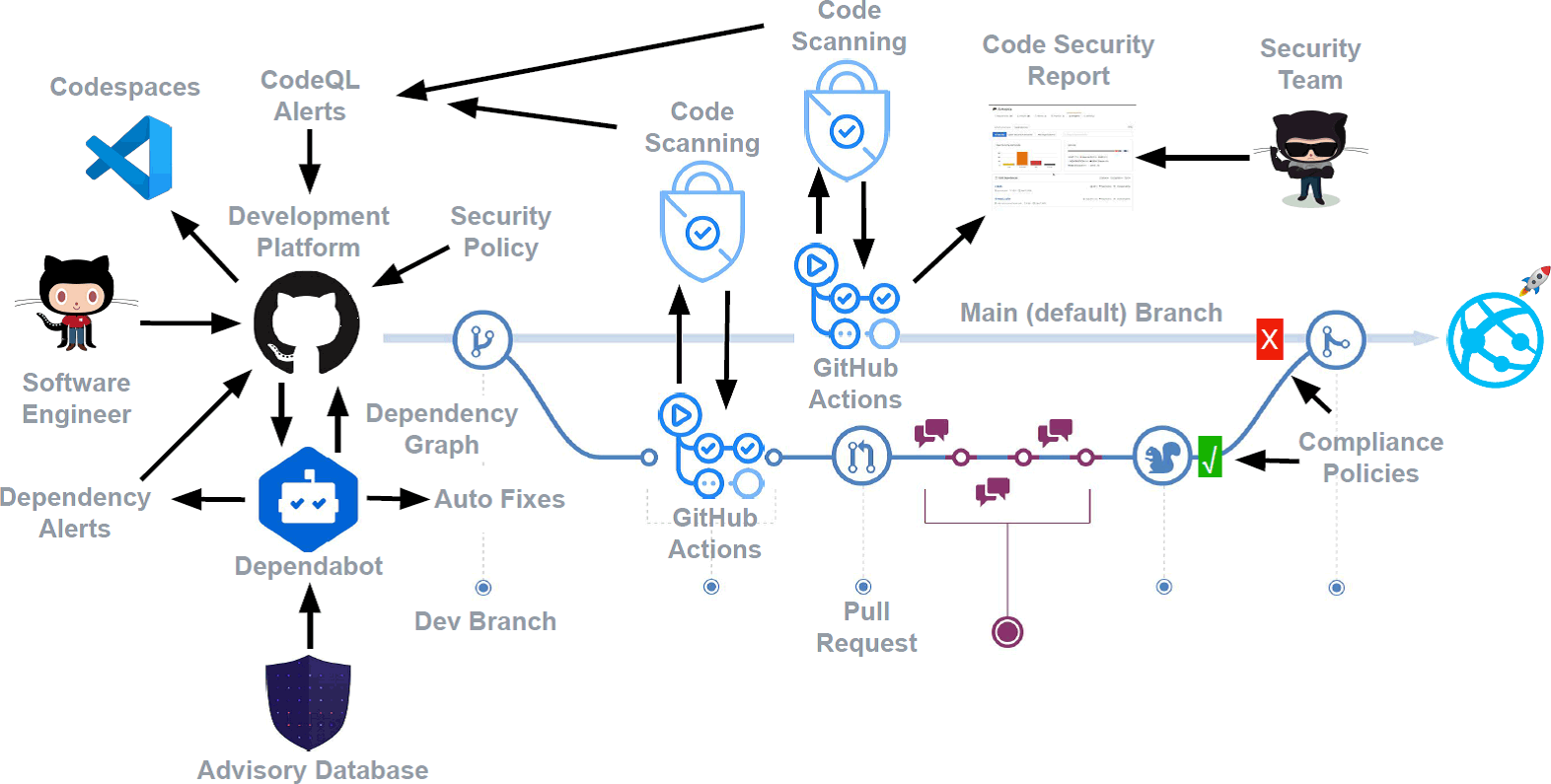
Current security features provided by GitHub
supply chain
- Dependency graph
View and understand dependencies - Advisory database
A database that records package vulnerabilities - Dependabot alerts
- Dependabot security updates
Dependent Package Vulnerability Notifications and Pull Request Creation for Automatic Fixes - Dependency review *
See new dependencies and vulnerabilities in pull requests
code
- Secret scanning *
Detect API tokens and other secrets hidden in Git history - Code scanning *
Static analysis for every git push operation, integrated into workflow with CodeQL analysis
Development lifecycle
- Branch protection
Define conditions when branches and pull requests are merged - Commit signing
Provided all commits are signed - Security Center
(Security Overview)
Visualize the risk situation within your organization
*Provided in GitHub Enterprise's paid option "GitHub Advanced Security"
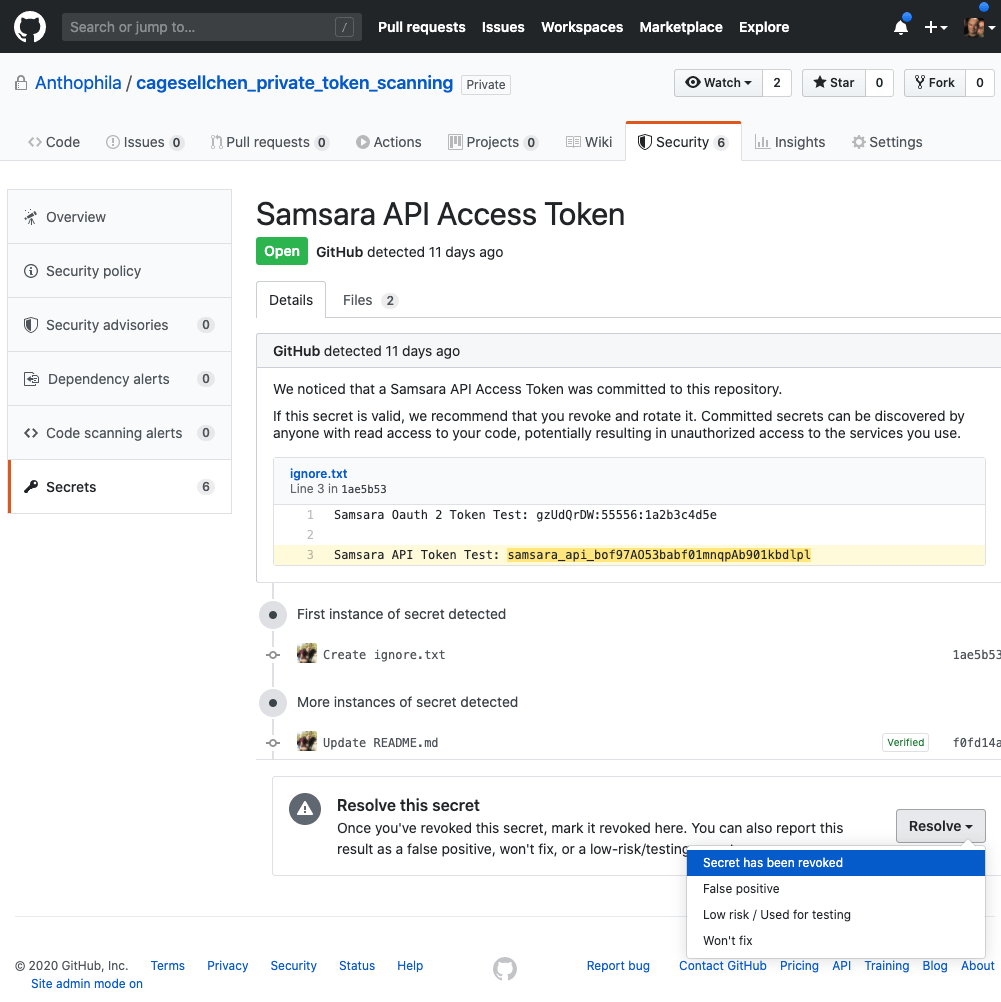
Code security - secret detection -

- Automatically detect whether authentication tokens and private key information (secrets) for communicating with external services are mixed in with code pushed to GitHub
Supported secret information is here - Scan all git history after enabling the feature
- Push protection function prevents source code containing secret information from being pushed
| GHEC | GHES | |
| Secret Scanning | ○ | ○ |
* Provided as a paid option "GitHub Advanced Security" of GitHub Enterprise
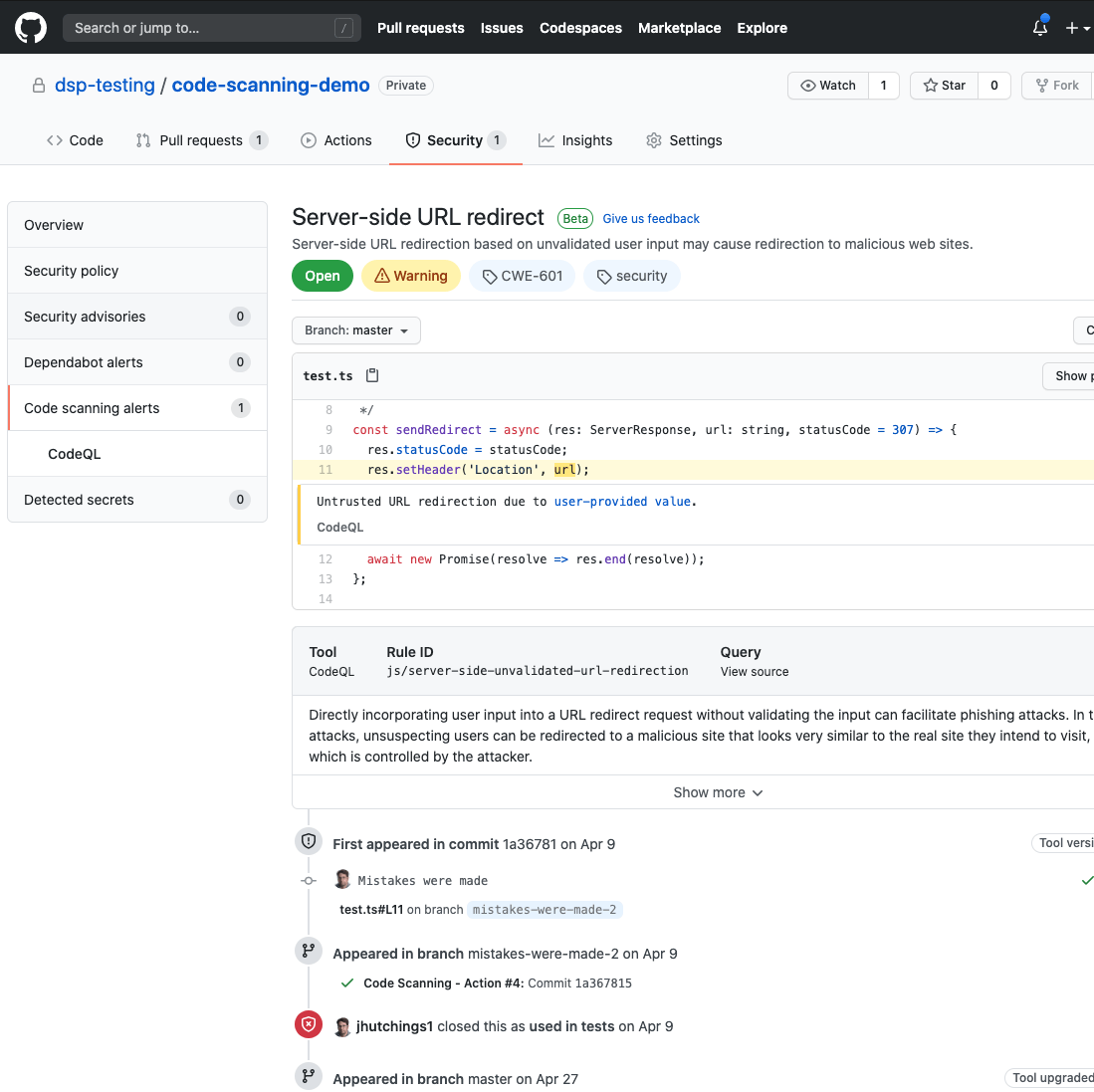
Code Security - Code Vulnerability Detection -

- It is possible to automatically analyze the code under development and check whether the code of the pattern that causes the vulnerability is written (CodeQL)
- Scan items can be GitHub querysets (over 2,000 patterns supported) or custom queries developed by the community on GitHub
- Extensible with other static analysis tools
* Currently, it can be linked with ShiftLeft, Anchore, etc. - Supported language/environment
https://codeql.github.com/docs/codeql-overview/supported-languages-and-frameworks/
| GHEC | GHES | |
| Code scanning | ○ | ○ |
* Provided as a paid option "GitHub Advanced Security" of GitHub Enterprise
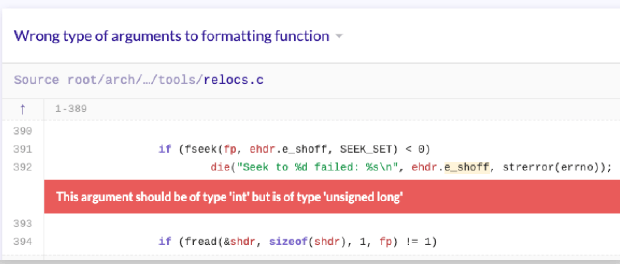
Effects of Code Scanning
- Find vulnerabilities early in development
Reduce remediation costs by preventing known vulnerabilities during the development phase - Accurate analysis
CodeQL interprets the call graph of the code and the meaning of the code and performs analysis, so it achieves very high accuracy (= few false positives). It also reduces the time spent reviewing analysis results. - prioritized alerts
Analysis results are prioritized in 3 stages, so you can deal with the most important ones first - Leverage community
Leverage queries created by GitHub, other companies and the open source community
Inquiry/Document request
Macnica GitHub
- TEL:045-476-2010
- E-mail:github-rt@macnica.co.jp
Weekdays: 9:00-17:00